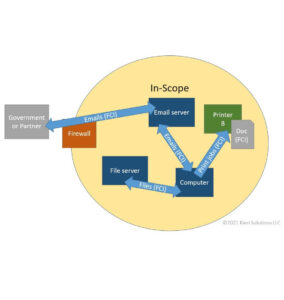
Almost every defense contractor makes one or more of these design errors when they start building their CMMC Level 3 network
Author: Amira Armond
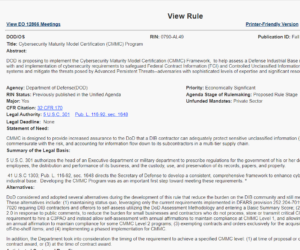
DFARS 252.204-7012 controls discussion for CMMC
Why is there a page for DFARS 252.204-7012 on a CMMC website? DFARS 252.204-7012 is a contract requirement for defense contractors that handle or might handle Controlled Unclassified Information (CUI). Unlike the CMMC, DFARS 7012 is currently required and should be a priority for DoD contractors that deal with CUI. You can tell if your Read More
How to submit a NIST SP 800-171 self assessment to SPRS
Answers to common questions about how to submit your NIST SP 800-171 self assessment to SPRS. Register an account, how to handle multiple…
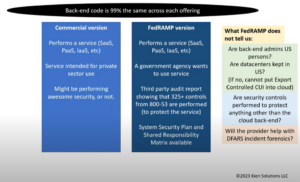
FedRAMP “Equivalent” Memo released
Must read for anyone with DFARS 252.204-7012 in their contract! FedRAMP equivalent is defined for DFARS 252.204-7012 Summary: FedRAMP Equivalency, as used in DFARS 252.204-7012, means that the cloud provider has been third-party-validated, with a full audit, by a FedRAMP Third Party Assessment Organization, to have implemented every control from the FedRAMP Moderate baseline. How Read More
CMMC Level 2 Self-Assessment Analysis
Our sponsor, Kieri Solutions, has released an in-depth review and analysis of CMMC Level 2 Self-Assessments according to the CMMC Proposed Rule. Not official guidance for CMMC Proposed Rule This paper is for educational purposes and is not authoritative in any way for the CMMC Program. Includes instructions to comment on CMMC Proposed Rule Towards Read More
Webinar – CMMC Proposed Rule Review
Our sponsor, Kieri Solutions, produced this webinar to review the hottest topics of the CMMC Proposed Rule. Thanks to Vincent Scott, Brian Hubbard, Jil Wright, and Amira Armond (all Certified CMMC Assessors and Instructors) for providing insightful review and commentary! 32CFR CMMC Proposed Rule Webinar What are your thoughts? Do you think Certification Assessments will Read More
CMMC Rule links to text (with December 26 content)!
Here are links to the text of the CMMC Proposed Rule: 32 CFR (CMMC Program) Downloadable PDF of Federal Register text (this version has page numbers): https://public-inspection.federalregister.gov/2023-27280.pdf Federal Register home page for CMMC and comments: https://www.federalregister.gov/documents/2023/12/26/2023-27280/cybersecurity-maturity-model-certification-cmmc-program Docket Information (the rule agenda): https://www.regulations.gov/docket/DOD-2023-OS-0063 Public comments posted regarding rule: https://www.regulations.gov/document/DOD-2023-OS-0063-0001 Regulatory Impact Analysis 32 CFR Part 170 Read More
Is GCC-High required to pass CMMC?
Amira Armond (CMMC Instructor, Certified CMMC Assessor, President Kieri Solutions) answers the question “Is GCC-High required to pass a CMMC assessment?” This is actually an explanation of what the FedRAMP program is and is not. This video is meant for educational and entertainment purposes only. These are opinions presented in a purposefully simplified format. Enjoy, Read More
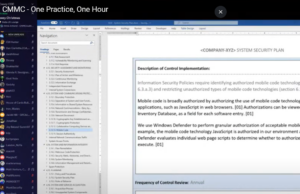
How the secret sauce is made – one practice, one hour
How does a defense contractor create a plan to perform each requirement in CMMC and NIST SP 800-171? Will you fail if you don’t write policy statements which regurgitate each requirement in a ‘shall” form? AKA “𝘚𝘢𝘧𝘦𝘨𝘶𝘢𝘳𝘥𝘪𝘯𝘨 𝘮𝘦𝘢𝘴𝘶𝘳𝘦𝘴 𝘧𝘰𝘳 𝘊𝘜𝘐 𝘢𝘵 𝘢𝘭𝘵𝘦𝘳𝘯𝘢𝘵𝘪𝘷𝘦 𝘸𝘰𝘳𝘬 𝘴𝘪𝘵𝘦𝘴 𝘴𝘩𝘢𝘭𝘭 𝘣𝘦 𝘦𝘯𝘧𝘰𝘳𝘤𝘦𝘥.” The answer is no. You don’t need to Read More
Joint Surveillance Assessment – what is it like?
This is an interview with Jose Rojas (TTC) and Ozzie Saeed (IntelliGRC) about their experience being assessed by Kieri Solutions, an Authorized C3PAO, as part of the Joint Surveillance Voluntary assessment program. Other than the obvious congratulations to both of them for helping TTC achieve a perfect “110” score on their assessment, we discuss what Read More
CMMC News – October 2023 – the DFARS Rule
Rulemaking Timeline for CMMC DFARS Rule The proposed CMMC Rule has been submitted to the Office of Information and Regulatory Affairs. Several groups (mostly cybersecurity professionals) have met with DoD CIO and OIRA to give recommendations for the rule. Most of them submitted documents with their feedback which can be downloaded from the EO 12866 Read More
What does “monitor” mean in CMMC?
Logan Therrien and Amira Armond from Kieri Solutions (an Authorized C3PAO) discuss the concept of monitoring and how it is evaluated by CMMC assessors. Several assessment objectives in CMMC Level 2 require monitoring. 🔍 the physical facility where organizational systems reside is monitored;🔍 the support infrastructure for organizational systems is monitored.🔍 visitor activity is monitored.🔍 Read More
Why so few Defense contractors are compliant
𝐇𝐨𝐰 𝐥𝐨𝐧𝐠 𝐝𝐨𝐞𝐬 𝐢𝐭 𝐭𝐚𝐤𝐞 𝐚 𝐜𝐨𝐦𝐩𝐚𝐧𝐲 𝐭𝐨 𝐠𝐨 𝐛𝐚𝐧𝐤𝐫𝐮𝐩𝐭 𝐢𝐭 𝐰𝐡𝐞𝐧 𝐜𝐚𝐧’𝐭 𝐰𝐢𝐧 𝐰𝐨𝐫𝐤? One year? Two? Three? Let me tell you a story about how a system of perverse incentives caused our current cybersecurity situation in the Defense Industrial Base. Back in 2017 (six years ago), new and renewing DoD contracts started including Read More
Podcast – increasing the likelihood of passing CMMC assessments
This podcast by Omnistruct features Amira Armond, John Riley, and George Usi. Recorded in May-June 2023. They discuss the basics of CMMC, the “hardest” requirement (FIPS of course), the aspects that contractors have the most difficulty with, and the status of the roll-out. Check it out! The link below has the full text transcript: Omnistruct: Read More
CMMC Breaking News – July 25, 2023
Today we had two big events in #CMMC and US Federal Contractor Cybersecurity. The Rule for CMMC moved to the Office of Management and Budget. That means a timer has started, 90 days or less, for the review to complete. Expect the text to be published by mid-October. There is still a possibility that it will come Read More
3.13.11 FIPS 140-2 Validated Cryptography
It is time, finally, to talk about the #1 “Other than Satisfied” requirement in 800-171, per historic DIBCAC assessments. 😱 💥 💥 𝐅𝐈𝐏𝐒 140-2 𝐕𝐚𝐥𝐢𝐝𝐚𝐭𝐞𝐝 𝐌𝐨𝐝𝐮𝐥𝐞𝐬 💥 💥 😱 Listen up – I’m going to tell you how to succeed at this requirement. It might take money, it might take time, but it CAN be Read More
3.5.3 Multifactor Authentication
Multifactor Authentication: #2 of the top 10 “Other than Satisfied Requirements” for 800-171 assessments by DIBCAC. 𝐔𝐬𝐞 𝐦𝐮𝐥𝐭𝐢𝐟𝐚𝐜𝐭𝐨𝐫 𝐚𝐮𝐭𝐡𝐞𝐧𝐭𝐢𝐜𝐚𝐭𝐢𝐨𝐧 𝐟𝐨𝐫 𝐥𝐨𝐜𝐚𝐥 𝐚𝐧𝐝 𝐧𝐞𝐭𝐰𝐨𝐫𝐤 𝐚𝐜𝐜𝐞𝐬𝐬 𝐭𝐨 𝐩𝐫𝐢𝐯𝐢𝐥𝐞𝐠𝐞𝐝 𝐚𝐜𝐜𝐨𝐮𝐧𝐭𝐬 𝐚𝐧𝐝 𝐟𝐨𝐫 𝐧𝐞𝐭𝐰𝐨𝐫𝐤 𝐚𝐜𝐜𝐞𝐬𝐬 𝐭𝐨 𝐧𝐨𝐧-𝐩𝐫𝐢𝐯𝐢𝐥𝐞𝐠𝐞𝐝 𝐚𝐜𝐜𝐨𝐮𝐧𝐭𝐬. My theory is that most of the time when this requirement is failed, it is because the IT department didn’t know Read More
What are Spot Checks for?
𝐂𝐌𝐌𝐂 𝐀𝐬𝐬𝐞𝐬𝐬𝐦𝐞𝐧𝐭 𝐒𝐩𝐨𝐭 𝐂𝐡𝐞𝐜𝐤𝐬 “𝘐𝘧 𝘤𝘰𝘯𝘵𝘳𝘢𝘤𝘵𝘰𝘳’𝘴 𝘳𝘪𝘴𝘬-𝘣𝘢𝘴𝘦𝘥 𝘴𝘦𝘤𝘶𝘳𝘪𝘵𝘺 𝘱𝘰𝘭𝘪𝘤𝘪𝘦𝘴, 𝘱𝘳𝘰𝘤𝘦𝘥𝘶𝘳𝘦𝘴, 𝘢𝘯𝘥 𝘱𝘳𝘢𝘤𝘵𝘪𝘤𝘦𝘴 𝘥𝘰𝘤𝘶𝘮𝘦𝘯𝘵𝘢𝘵𝘪𝘰𝘯 𝘰𝘳 𝘰𝘵𝘩𝘦𝘳 𝘧𝘪𝘯𝘥𝘪𝘯𝘨𝘴 𝘳𝘢𝘪𝘴𝘦 𝘲𝘶𝘦𝘴𝘵𝘪𝘰𝘯𝘴 𝘢𝘣𝘰𝘶𝘵 𝘵𝘩𝘦𝘴𝘦 𝘢𝘴𝘴𝘦𝘵𝘴, 𝘵𝘩𝘦 𝘢𝘴𝘴𝘦𝘴𝘴𝘰𝘳 𝘤𝘢𝘯 𝘤𝘰𝘯𝘥𝘶𝘤𝘵 𝘢 𝘭𝘪𝘮𝘪𝘵𝘦𝘥 𝘴𝘱𝘰𝘵 𝘤𝘩𝘦𝘤𝘬 𝘵𝘰 𝘪𝘥𝘦𝘯𝘵𝘪𝘧𝘺 𝘳𝘪𝘴𝘬𝘴. 𝘛𝘩𝘦 𝘭𝘪𝘮𝘪𝘵𝘦𝘥 𝘴𝘱𝘰𝘵 𝘤𝘩𝘦𝘤𝘬(𝘴) 𝘴𝘩𝘢𝘭𝘭 𝘯𝘰𝘵 𝘮𝘢𝘵𝘦𝘳𝘪𝘢𝘭𝘭𝘺 𝘪𝘯𝘤𝘳𝘦𝘢𝘴𝘦 𝘵𝘩𝘦 𝘢𝘴𝘴𝘦𝘴𝘴𝘮𝘦𝘯𝘵 𝘥𝘶𝘳𝘢𝘵𝘪𝘰𝘯 𝘯𝘰𝘳 𝘵𝘩𝘦 𝘢𝘴𝘴𝘦𝘴𝘴𝘮𝘦𝘯𝘵 𝘤𝘰𝘴𝘵. 𝘛𝘩𝘦 𝘭𝘪𝘮𝘪𝘵𝘦𝘥 𝘴𝘱𝘰𝘵 𝘤𝘩𝘦𝘤𝘬(𝘴) 𝘸𝘪𝘭𝘭 𝘣𝘦 𝘸𝘪𝘵𝘩𝘪𝘯 𝘵𝘩𝘦 𝘥𝘦𝘧𝘪𝘯𝘦𝘥 Read More
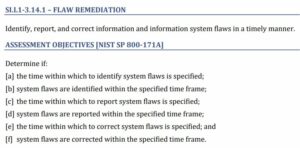
3.14.1 Identify, report, correct system flaws
Continuing the Top 10 “Other than Satisfied Requirements” for 800-171 assessments by DIBCAC. “𝐈𝐝𝐞𝐧𝐭𝐢𝐟𝐲, 𝐫𝐞𝐩𝐨𝐫𝐭, 𝐚𝐧𝐝 𝐜𝐨𝐫𝐫𝐞𝐜𝐭 𝐢𝐧𝐟𝐨𝐫𝐦𝐚𝐭𝐢𝐨𝐧 𝐚𝐧𝐝 𝐢𝐧𝐟𝐨𝐫𝐦𝐚𝐭𝐢𝐨𝐧 𝐬𝐲𝐬𝐭𝐞𝐦 𝐟𝐥𝐚𝐰𝐬 𝐢𝐧 𝐚 𝐭𝐢𝐦𝐞𝐥𝐲 𝐦𝐚𝐧𝐧𝐞𝐫.” This is the third most “Other than Satisfied” requirement. 3.14.1 is both misunderstood and very hard to implement. Both problems cause failures. 𝐖𝐡𝐲 𝐢𝐬 3.14.1 𝐦𝐢𝐬𝐮𝐧𝐝𝐞𝐫𝐬𝐭𝐨𝐨𝐝? Most people read the Read More
3.11.1 Periodically assess the risk to organizational operations
3.11.1 𝐏𝐞𝐫𝐢𝐨𝐝𝐢𝐜𝐚𝐥𝐥𝐲 𝐚𝐬𝐬𝐞𝐬𝐬 𝐫𝐢𝐬𝐤…This is the fourth-most “Other than satisfied” #CMMC requirement. Periodically assess the risk to organizational operations (including mission, functions, image, or reputation), organizational assets, and individuals, resulting from the operation of organizational systems and the associated processing, storage, or transmission of CUI. Not hard to do, but often misunderstood. Let’s break it down. 𝐏𝐞𝐫𝐢𝐨𝐝𝐢𝐜𝐚𝐥𝐥𝐲 Read More
3.11.2 Scan for Vulnerabilities
Scan for vulnerabilities….This the fifth-most “Other than satisfied” #CMMC requirement with an 18% fail rate. 3.11.2 𝐒𝐜𝐚𝐧 𝐟𝐨𝐫 𝐯𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐢𝐞𝐬 𝐢𝐧 𝐨𝐫𝐠𝐚𝐧𝐢𝐳𝐚𝐭𝐢𝐨𝐧𝐚𝐥 𝐬𝐲𝐬𝐭𝐞𝐦𝐬 𝐚𝐧𝐝 𝐚𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐩𝐞𝐫𝐢𝐨𝐝𝐢𝐜𝐚𝐥𝐥𝐲 𝐚𝐧𝐝 𝐰𝐡𝐞𝐧 𝐧𝐞𝐰 𝐯𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐢𝐞𝐬 𝐚𝐟𝐟𝐞𝐜𝐭𝐢𝐧𝐠 𝐭𝐡𝐨𝐬𝐞 𝐬𝐲𝐬𝐭𝐞𝐦𝐬 𝐚𝐧𝐝 𝐚𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐚𝐫𝐞 𝐢𝐝𝐞𝐧𝐭𝐢𝐟𝐢𝐞𝐝. “𝒐𝒓𝒈𝒂𝒏𝒊𝒛𝒂𝒕𝒊𝒐𝒏𝒂𝒍 𝒔𝒚𝒔𝒕𝒆𝒎𝒔”…This is an example of a broadly-applicable requirement – something that is expected to be applied 𝘩𝘰𝘭𝘪𝘴𝘵𝘪𝘤𝘢𝘭𝘭𝘺 from boundary to Read More
3.3.3 Review and Update Logged Events
This is #6 in the series of most common failed requirements as assessed by the DoD’s Cyber Assessment Center. This requirement is another example of misunderstanding == failing (alongside the other top 10 requirements). Most people do not understand what is expected for 3.3.3. To “review and update logged events”, you must consider 𝐰𝐡𝐢𝐜𝐡 𝐞𝐯𝐞𝐧𝐭𝐬 Read More
3.3.4 Audit Logging Process Failure
Continuing the Top 10 Failed Requirements for 800-171! Onward to #7: 3.3.4 “𝐀𝐥𝐞𝐫𝐭 𝐢𝐧 𝐭𝐡𝐞 𝐞𝐯𝐞𝐧𝐭 𝐨𝐟 𝐚𝐧 𝐚𝐮𝐝𝐢𝐭 𝐥𝐨𝐠𝐠𝐢𝐧𝐠 𝐩𝐫𝐨𝐜𝐞𝐬𝐬 𝐟𝐚𝐢𝐥𝐮𝐫𝐞.” Sit with me while I tell a story… 𝘈𝘯 𝘰𝘳𝘨𝘢𝘯𝘪𝘻𝘢𝘵𝘪𝘰𝘯 𝘥𝘪𝘴𝘤𝘰𝘷𝘦𝘳𝘴 𝘵𝘩𝘢𝘵 𝘵𝘩𝘦𝘺 𝘸𝘦𝘳𝘦 𝘣𝘳𝘦𝘢𝘤𝘩𝘦𝘥 𝘣𝘦𝘤𝘢𝘶𝘴𝘦 𝘨𝘰𝘷𝘦𝘳𝘯𝘮𝘦𝘯𝘵 𝘴𝘦𝘤𝘳𝘦𝘵𝘴 𝘢𝘳𝘦 𝘣𝘦𝘪𝘯𝘨 𝘴𝘰𝘭𝘥 𝘰𝘯 𝘵𝘩𝘦 𝘥𝘢𝘳𝘬 𝘸𝘦𝘣. 𝘋𝘊3 𝘪𝘯𝘤𝘪𝘥𝘦𝘯𝘵 𝘳𝘦𝘴𝘱𝘰𝘯𝘴𝘦 𝘵𝘦𝘢𝘮𝘴 𝘢𝘳𝘦 𝘤𝘢𝘭𝘭𝘦𝘥; 𝘵𝘩𝘦𝘺 𝘴𝘵𝘢𝘳𝘵 Read More
3.3.5 Correlate Audit Processes
NIST SP 800-171 3.3.5 𝐂𝐨𝐫𝐫𝐞𝐥𝐚𝐭𝐞 𝐚𝐮𝐝𝐢𝐭 𝐫𝐞𝐜𝐨𝐫𝐝 𝐫𝐞𝐯𝐢𝐞𝐰, 𝐚𝐧𝐚𝐥𝐲𝐬𝐢𝐬, 𝐚𝐧𝐝 𝐫𝐞𝐩𝐨𝐫𝐭𝐢𝐧𝐠 𝐩𝐫𝐨𝐜𝐞𝐬𝐬𝐞𝐬 𝐟𝐨𝐫 𝐢𝐧𝐯𝐞𝐬𝐭𝐢𝐠𝐚𝐭𝐢𝐨𝐧 𝐚𝐧𝐝 𝐫𝐞𝐬𝐩𝐨𝐧𝐬𝐞 𝐭𝐨 𝐢𝐧𝐝𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐨𝐟 𝐮𝐧𝐥𝐚𝐰𝐟𝐮𝐥, 𝐮𝐧𝐚𝐮𝐭𝐡𝐨𝐫𝐢𝐳𝐞𝐝, 𝐬𝐮𝐬𝐩𝐢𝐜𝐢𝐨𝐮𝐬, 𝐨𝐫 𝐮𝐧𝐮𝐬𝐮𝐚𝐥 𝐚𝐜𝐭𝐢𝐯𝐢𝐭𝐲. This is the 8th most likely requirement to be “other than satisfied” by defense contractors, according to the DoD’s Cybersecurity Assessment Center. The problem is that this requirement can be read Read More
C3PAO CMMC Level 2 Assessments
On behalf of CMMCAudit.org, I’m excited to share this interview with Kyle Lai about his lessons learned from the CMMC Level 2 assessment performed by DCMA DIBCAC against his C3PAO: KLC Consulting. This video is packed with actionable information about how CMMC Level 2 assessments are performed. We compared and contrasted between the assessment that Read More
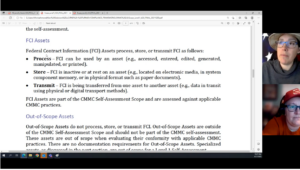
CMMC Scoping for Level 2
This video is provided by Amira Armond and Jil Wright (CMMC Provisional Assessors and Provisional Instructors) from Kieri Solutions, an Authorized C3PAO. Topics discussed in the video are: This content is way more than the CCP course blueprint covers and more in-depth than what is normally covered in CCA courses! If you haven’t seen it yet, go watch the CMMC Read More
CMMC Scoping for Level 1
This video is provided by Amira Armond and Jil Wright (CMMC Provisional Assessors and Provisional Instructors) from Kieri Solutions, an Authorized C3PAO. Topics included are: Enjoy, and don’t forget to subscribe to our YouTube channel for lots of other CMMC training content. Kieri Solutions is an Authorized C3PAO providing CMMC and 800-171 assessment and preparation Read More
3.6.3 Test the Organizational Incident Response Capability
This was originally posted on LinkedIn. Check the original post and community discussion here! On to the next requirement! 3.6.3 𝐓𝐞𝐬𝐭 𝐭𝐡𝐞 𝐨𝐫𝐠𝐚𝐧𝐢𝐳𝐚𝐭𝐢𝐨𝐧𝐚𝐥 𝐢𝐧𝐜𝐢𝐝𝐞𝐧𝐭 𝐫𝐞𝐬𝐩𝐨𝐧𝐬𝐞 𝐜𝐚𝐩𝐚𝐛𝐢𝐥𝐢𝐭𝐲. This is post #5 in my series analyzing the top ten failed / misunderstood NIST SP 800-171 and #CMMC requirements according to DIBCAC. Incident response testing is the 9th most “other Read More
3.4.1 Establish / Maintain Baseline Configurations
This series reviews the top failed (misunderstood) 800-171 and CMMC requirements. Originally posted on LinkedIn – check the start of series here for community conversation and thoughts! 3.4.1 𝐄𝐬𝐭𝐚𝐛𝐥𝐢𝐬𝐡/𝐦𝐚𝐢𝐧𝐭𝐚𝐢𝐧 𝐛𝐚𝐬𝐞𝐥𝐢𝐧𝐞 𝐜𝐨𝐧𝐟𝐢𝐠𝐮𝐫𝐚𝐭𝐢𝐨𝐧𝐬 This one is both commonly misunderstood and difficult to implement, even though it can be 100% a manual process. First, the requirement language is split into two Read More
Excuses that won’t work for your CMMC assessment
Public Safety Announcement for #CMMC and DIBCAC assessments of 800-171 compliance. “My _________ is scheduled to occur in January and we haven’t reached January yet.” – said too many Organizations Seeking Certification Do not try to use this excuse to explain why you lack evidence for performing an 800-171 requirement! Your assessor will not be sympathetic. What Read More