Our DIBCAC re-assessment for the certification we need to remain a C3PAO came at a busy time for Kieri. From November 2024 through February 2025, we nearly doubled in size, from 15 full-time employees to nearly 30 full-time employees with Read More
Tag: CMMC
CMMC 101 – Final Rule Version
The DoD released a “CMMC 101” overview which does a good job of describing the CMMC program at a high level. If you need to review CMMC with your company executives, this might be the best presentation to use. Of Read More
32CFR Final Rule Published – CMMC goes live!
On October 15, 2024, the Federal Register was updated with the CMMC Final Rule (32CFR). This rule will be fully effective on December 15, 2024. Link to Federal Register for CMMC This link goes to the U.S. Government’s Federal Register Read More
Review of CMMC Registered Practitioner Training
This post was originally written in September 2020. It was updated in July 2024. In September 2020, I took the Cyber-AB’s Registered Practitioner training course. We aren’t allowed to reproduce the content, so you won’t learn any secrets from me, Read More
How to become a CMMC assessor or auditor
The latest information about how to become a CMMC auditor or certifier. Registrations are open for assessors, C3PAOs, and CMMC practitioners…
How to get a CMMC Audit or Assessment
You’re in the right place if the US Government or your prime contractor told you that you need to get a CMMC certification. What is CMMC? CMMC is an initialization for the term “Cybersecurity Maturity Model Certification”. This term was Read More
CMMC JSVA program – what you need to know
Some tidbits about CMMC’s Joint Surveillance Voluntary Assessment (JSVA) program that you might not know: JSVA program is intended to train C3PAOs and CMMC Assessors 1) The DoD is essentially using the JSVA program to train and vet our private Read More
CMMC assessment? Don’t let pride take you down
Getting CMMC assessed? Some advice.. Listen to your assessor If we say that your evidence isn’t related to the requirement being inspected, or especially the critical words “I think you have misinterpreted this requirement”, instead of getting mad, take a Read More
CMMC Rule links to text (with December 26 content)!
Here are links to the text of the CMMC Proposed Rule: 32 CFR (CMMC Program) Downloadable PDF of Federal Register text (this version has page numbers): https://public-inspection.federalregister.gov/2023-27280.pdf Federal Register home page for CMMC and comments: https://www.federalregister.gov/documents/2023/12/26/2023-27280/cybersecurity-maturity-model-certification-cmmc-program Docket Information (the rule Read More
Why so few Defense contractors are compliant
𝐇𝐨𝐰 𝐥𝐨𝐧𝐠 𝐝𝐨𝐞𝐬 𝐢𝐭 𝐭𝐚𝐤𝐞 𝐚 𝐜𝐨𝐦𝐩𝐚𝐧𝐲 𝐭𝐨 𝐠𝐨 𝐛𝐚𝐧𝐤𝐫𝐮𝐩𝐭 𝐢𝐭 𝐰𝐡𝐞𝐧 𝐜𝐚𝐧’𝐭 𝐰𝐢𝐧 𝐰𝐨𝐫𝐤? One year? Two? Three? Let me tell you a story about how a system of perverse incentives caused our current cybersecurity situation in the Defense Read More
Podcast – increasing the likelihood of passing CMMC assessments
This podcast by Omnistruct features Amira Armond, John Riley, and George Usi. Recorded in May-June 2023. They discuss the basics of CMMC, the “hardest” requirement (FIPS of course), the aspects that contractors have the most difficulty with, and the status Read More
CMMC Breaking News – July 25, 2023
Today we had two big events in #CMMC and US Federal Contractor Cybersecurity. The Rule for CMMC moved to the Office of Management and Budget. That means a timer has started, 90 days or less, for the review to complete. Expect the Read More
3.13.11 FIPS 140-2 Validated Cryptography
It is time, finally, to talk about the #1 “Other than Satisfied” requirement in 800-171, per historic DIBCAC assessments. 😱 💥 💥 𝐅𝐈𝐏𝐒 140-2 𝐕𝐚𝐥𝐢𝐝𝐚𝐭𝐞𝐝 𝐌𝐨𝐝𝐮𝐥𝐞𝐬 💥 💥 😱 Listen up – I’m going to tell you how to succeed Read More
3.5.3 Multifactor Authentication
Multifactor Authentication: #2 of the top 10 “Other than Satisfied Requirements” for 800-171 assessments by DIBCAC. 𝐔𝐬𝐞 𝐦𝐮𝐥𝐭𝐢𝐟𝐚𝐜𝐭𝐨𝐫 𝐚𝐮𝐭𝐡𝐞𝐧𝐭𝐢𝐜𝐚𝐭𝐢𝐨𝐧 𝐟𝐨𝐫 𝐥𝐨𝐜𝐚𝐥 𝐚𝐧𝐝 𝐧𝐞𝐭𝐰𝐨𝐫𝐤 𝐚𝐜𝐜𝐞𝐬𝐬 𝐭𝐨 𝐩𝐫𝐢𝐯𝐢𝐥𝐞𝐠𝐞𝐝 𝐚𝐜𝐜𝐨𝐮𝐧𝐭𝐬 𝐚𝐧𝐝 𝐟𝐨𝐫 𝐧𝐞𝐭𝐰𝐨𝐫𝐤 𝐚𝐜𝐜𝐞𝐬𝐬 𝐭𝐨 𝐧𝐨𝐧-𝐩𝐫𝐢𝐯𝐢𝐥𝐞𝐠𝐞𝐝 𝐚𝐜𝐜𝐨𝐮𝐧𝐭𝐬. My theory is that most of Read More
What are Spot Checks for?
𝐂𝐌𝐌𝐂 𝐀𝐬𝐬𝐞𝐬𝐬𝐦𝐞𝐧𝐭 𝐒𝐩𝐨𝐭 𝐂𝐡𝐞𝐜𝐤𝐬 “𝘐𝘧 𝘤𝘰𝘯𝘵𝘳𝘢𝘤𝘵𝘰𝘳’𝘴 𝘳𝘪𝘴𝘬-𝘣𝘢𝘴𝘦𝘥 𝘴𝘦𝘤𝘶𝘳𝘪𝘵𝘺 𝘱𝘰𝘭𝘪𝘤𝘪𝘦𝘴, 𝘱𝘳𝘰𝘤𝘦𝘥𝘶𝘳𝘦𝘴, 𝘢𝘯𝘥 𝘱𝘳𝘢𝘤𝘵𝘪𝘤𝘦𝘴 𝘥𝘰𝘤𝘶𝘮𝘦𝘯𝘵𝘢𝘵𝘪𝘰𝘯 𝘰𝘳 𝘰𝘵𝘩𝘦𝘳 𝘧𝘪𝘯𝘥𝘪𝘯𝘨𝘴 𝘳𝘢𝘪𝘴𝘦 𝘲𝘶𝘦𝘴𝘵𝘪𝘰𝘯𝘴 𝘢𝘣𝘰𝘶𝘵 𝘵𝘩𝘦𝘴𝘦 𝘢𝘴𝘴𝘦𝘵𝘴, 𝘵𝘩𝘦 𝘢𝘴𝘴𝘦𝘴𝘴𝘰𝘳 𝘤𝘢𝘯 𝘤𝘰𝘯𝘥𝘶𝘤𝘵 𝘢 𝘭𝘪𝘮𝘪𝘵𝘦𝘥 𝘴𝘱𝘰𝘵 𝘤𝘩𝘦𝘤𝘬 𝘵𝘰 𝘪𝘥𝘦𝘯𝘵𝘪𝘧𝘺 𝘳𝘪𝘴𝘬𝘴. 𝘛𝘩𝘦 𝘭𝘪𝘮𝘪𝘵𝘦𝘥 𝘴𝘱𝘰𝘵 𝘤𝘩𝘦𝘤𝘬(𝘴) 𝘴𝘩𝘢𝘭𝘭 𝘯𝘰𝘵 𝘮𝘢𝘵𝘦𝘳𝘪𝘢𝘭𝘭𝘺 𝘪𝘯𝘤𝘳𝘦𝘢𝘴𝘦 𝘵𝘩𝘦 Read More
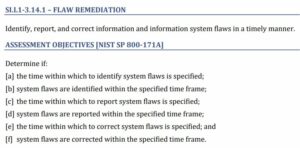
3.14.1 Identify, report, correct system flaws
Continuing the Top 10 “Other than Satisfied Requirements” for 800-171 assessments by DIBCAC. “𝐈𝐝𝐞𝐧𝐭𝐢𝐟𝐲, 𝐫𝐞𝐩𝐨𝐫𝐭, 𝐚𝐧𝐝 𝐜𝐨𝐫𝐫𝐞𝐜𝐭 𝐢𝐧𝐟𝐨𝐫𝐦𝐚𝐭𝐢𝐨𝐧 𝐚𝐧𝐝 𝐢𝐧𝐟𝐨𝐫𝐦𝐚𝐭𝐢𝐨𝐧 𝐬𝐲𝐬𝐭𝐞𝐦 𝐟𝐥𝐚𝐰𝐬 𝐢𝐧 𝐚 𝐭𝐢𝐦𝐞𝐥𝐲 𝐦𝐚𝐧𝐧𝐞𝐫.” This is the third most “Other than Satisfied” requirement. 3.14.1 is both misunderstood and Read More
3.11.1 Periodically assess the risk to organizational operations
3.11.1 𝐏𝐞𝐫𝐢𝐨𝐝𝐢𝐜𝐚𝐥𝐥𝐲 𝐚𝐬𝐬𝐞𝐬𝐬 𝐫𝐢𝐬𝐤…This is the fourth-most “Other than satisfied” #CMMC requirement. Periodically assess the risk to organizational operations (including mission, functions, image, or reputation), organizational assets, and individuals, resulting from the operation of organizational systems and the associated processing, storage, or Read More
3.11.2 Scan for Vulnerabilities
Scan for vulnerabilities….This the fifth-most “Other than satisfied” #CMMC requirement with an 18% fail rate. 3.11.2 𝐒𝐜𝐚𝐧 𝐟𝐨𝐫 𝐯𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐢𝐞𝐬 𝐢𝐧 𝐨𝐫𝐠𝐚𝐧𝐢𝐳𝐚𝐭𝐢𝐨𝐧𝐚𝐥 𝐬𝐲𝐬𝐭𝐞𝐦𝐬 𝐚𝐧𝐝 𝐚𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐩𝐞𝐫𝐢𝐨𝐝𝐢𝐜𝐚𝐥𝐥𝐲 𝐚𝐧𝐝 𝐰𝐡𝐞𝐧 𝐧𝐞𝐰 𝐯𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐢𝐞𝐬 𝐚𝐟𝐟𝐞𝐜𝐭𝐢𝐧𝐠 𝐭𝐡𝐨𝐬𝐞 𝐬𝐲𝐬𝐭𝐞𝐦𝐬 𝐚𝐧𝐝 𝐚𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐚𝐫𝐞 𝐢𝐝𝐞𝐧𝐭𝐢𝐟𝐢𝐞𝐝. “𝒐𝒓𝒈𝒂𝒏𝒊𝒛𝒂𝒕𝒊𝒐𝒏𝒂𝒍 𝒔𝒚𝒔𝒕𝒆𝒎𝒔”…This is an example of Read More
3.3.3 Review and Update Logged Events
This is #6 in the series of most common failed requirements as assessed by the DoD’s Cyber Assessment Center. This requirement is another example of misunderstanding == failing (alongside the other top 10 requirements). Most people do not understand what Read More
3.3.4 Audit Logging Process Failure
Continuing the Top 10 Failed Requirements for 800-171! Onward to #7: 3.3.4 “𝐀𝐥𝐞𝐫𝐭 𝐢𝐧 𝐭𝐡𝐞 𝐞𝐯𝐞𝐧𝐭 𝐨𝐟 𝐚𝐧 𝐚𝐮𝐝𝐢𝐭 𝐥𝐨𝐠𝐠𝐢𝐧𝐠 𝐩𝐫𝐨𝐜𝐞𝐬𝐬 𝐟𝐚𝐢𝐥𝐮𝐫𝐞.” Sit with me while I tell a story… 𝘈𝘯 𝘰𝘳𝘨𝘢𝘯𝘪𝘻𝘢𝘵𝘪𝘰𝘯 𝘥𝘪𝘴𝘤𝘰𝘷𝘦𝘳𝘴 𝘵𝘩𝘢𝘵 𝘵𝘩𝘦𝘺 𝘸𝘦𝘳𝘦 𝘣𝘳𝘦𝘢𝘤𝘩𝘦𝘥 𝘣𝘦𝘤𝘢𝘶𝘴𝘦 𝘨𝘰𝘷𝘦𝘳𝘯𝘮𝘦𝘯𝘵 𝘴𝘦𝘤𝘳𝘦𝘵𝘴 Read More
3.3.5 Correlate Audit Processes
NIST SP 800-171 3.3.5 𝐂𝐨𝐫𝐫𝐞𝐥𝐚𝐭𝐞 𝐚𝐮𝐝𝐢𝐭 𝐫𝐞𝐜𝐨𝐫𝐝 𝐫𝐞𝐯𝐢𝐞𝐰, 𝐚𝐧𝐚𝐥𝐲𝐬𝐢𝐬, 𝐚𝐧𝐝 𝐫𝐞𝐩𝐨𝐫𝐭𝐢𝐧𝐠 𝐩𝐫𝐨𝐜𝐞𝐬𝐬𝐞𝐬 𝐟𝐨𝐫 𝐢𝐧𝐯𝐞𝐬𝐭𝐢𝐠𝐚𝐭𝐢𝐨𝐧 𝐚𝐧𝐝 𝐫𝐞𝐬𝐩𝐨𝐧𝐬𝐞 𝐭𝐨 𝐢𝐧𝐝𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐨𝐟 𝐮𝐧𝐥𝐚𝐰𝐟𝐮𝐥, 𝐮𝐧𝐚𝐮𝐭𝐡𝐨𝐫𝐢𝐳𝐞𝐝, 𝐬𝐮𝐬𝐩𝐢𝐜𝐢𝐨𝐮𝐬, 𝐨𝐫 𝐮𝐧𝐮𝐬𝐮𝐚𝐥 𝐚𝐜𝐭𝐢𝐯𝐢𝐭𝐲. This is the 8th most likely requirement to be “other than satisfied” by defense contractors, according Read More
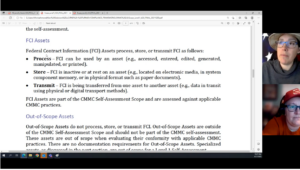
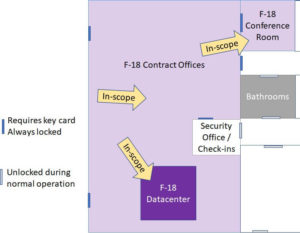
CMMC Scoping for Level 2
This video is provided by Amira Armond and Jil Wright (CMMC Provisional Assessors and Provisional Instructors) from Kieri Solutions, an Authorized C3PAO. Topics discussed in the video are: This content is way more than the CCP course blueprint covers and more in-depth than what is Read More
CMMC Scoping for Level 1
This video is provided by Amira Armond and Jil Wright (CMMC Provisional Assessors and Provisional Instructors) from Kieri Solutions, an Authorized C3PAO. Topics included are: Enjoy, and don’t forget to subscribe to our YouTube channel for lots of other CMMC Read More
3.6.3 Test the Organizational Incident Response Capability
This was originally posted on LinkedIn. Check the original post and community discussion here! On to the next requirement! 3.6.3 𝐓𝐞𝐬𝐭 𝐭𝐡𝐞 𝐨𝐫𝐠𝐚𝐧𝐢𝐳𝐚𝐭𝐢𝐨𝐧𝐚𝐥 𝐢𝐧𝐜𝐢𝐝𝐞𝐧𝐭 𝐫𝐞𝐬𝐩𝐨𝐧𝐬𝐞 𝐜𝐚𝐩𝐚𝐛𝐢𝐥𝐢𝐭𝐲. This is post #5 in my series analyzing the top ten failed / misunderstood Read More
3.4.1 Establish / Maintain Baseline Configurations
This series reviews the top failed (misunderstood) 800-171 and CMMC requirements. Originally posted on LinkedIn – check the start of series here for community conversation and thoughts! 3.4.1 𝐄𝐬𝐭𝐚𝐛𝐥𝐢𝐬𝐡/𝐦𝐚𝐢𝐧𝐭𝐚𝐢𝐧 𝐛𝐚𝐬𝐞𝐥𝐢𝐧𝐞 𝐜𝐨𝐧𝐟𝐢𝐠𝐮𝐫𝐚𝐭𝐢𝐨𝐧𝐬 This one is both commonly misunderstood and difficult to implement, even though Read More
When is a FIPS Validated Module required?
This video from Amira Armond and Jillian Wright (both Kieri Solutions Provisional Assessors and Instructors), explains when FIPS 140-2 validated modules are required to be used by CMMC Level 2 / NIST SP 800-171. It also explains when FIPS is Read More
Lessons learned from two (three?) DIBCAC assessments
On behalf of CMMCAudit.org, I’m excited to share this interview with Jake Williams about his lessons learned from two DIBCAC assessments of DFARS 252.204-7012 and NIST SP 800-171 compliance. This video is packed with actionable information about what to expect during assessments. Read More
CMMC Scope – are you ready for an assessment?
This article gives examples and explanations of how to identify your CMMC scope to an assessor when you are planning…
Does CMMC enforce FedRAMP and other CUI protections?
Will CMMC assessors stick to just the CMMC requirements or will they review your compliance to CUI-specified handling and other regulations?
The underestimated .998’s – procedure requirements for CMMC
CMMC Level 3 wants procedures, AKA the 998 requirements, but what does that actually mean? And what is necessary to pass?