Scan for vulnerabilities….
This the fifth-most “Other than satisfied” #CMMC requirement with an 18% fail rate.
3.11.2 𝐒𝐜𝐚𝐧 𝐟𝐨𝐫 𝐯𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐢𝐞𝐬 𝐢𝐧 𝐨𝐫𝐠𝐚𝐧𝐢𝐳𝐚𝐭𝐢𝐨𝐧𝐚𝐥 𝐬𝐲𝐬𝐭𝐞𝐦𝐬 𝐚𝐧𝐝 𝐚𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐩𝐞𝐫𝐢𝐨𝐝𝐢𝐜𝐚𝐥𝐥𝐲 𝐚𝐧𝐝 𝐰𝐡𝐞𝐧 𝐧𝐞𝐰 𝐯𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐢𝐞𝐬 𝐚𝐟𝐟𝐞𝐜𝐭𝐢𝐧𝐠 𝐭𝐡𝐨𝐬𝐞 𝐬𝐲𝐬𝐭𝐞𝐦𝐬 𝐚𝐧𝐝 𝐚𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐚𝐫𝐞 𝐢𝐝𝐞𝐧𝐭𝐢𝐟𝐢𝐞𝐝.
“𝒐𝒓𝒈𝒂𝒏𝒊𝒛𝒂𝒕𝒊𝒐𝒏𝒂𝒍 𝒔𝒚𝒔𝒕𝒆𝒎𝒔”…
This is an example of a broadly-applicable requirement – something that is expected to be applied 𝘩𝘰𝘭𝘪𝘴𝘵𝘪𝘤𝘢𝘭𝘭𝘺 from boundary to boundary, not just to assets that have CUI.
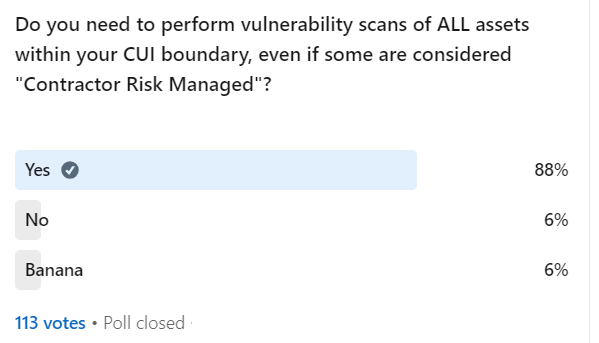
Many assessors will expect you to perform vulnerability scans of the entire network where you have CUI, not just the “CUI Assets”. This means that your CRMA 💻 are fair game for vulnerability scans if they can affect the security of your CUI. (I’ll ask in poll)
If you only scan convenient systems, such as the ones at the office, while ignoring the laptops on the road, you will probably fail.
“𝒂𝒑𝒑𝒍𝒊𝒄𝒂𝒕𝒊𝒐𝒏𝒔”…
To me, the primary use case for “applications” is software that can be connected to via a listening network port. I’m thinking of web servers, database servers, file servers. These are high-risk for compromise due to vulnerabilities because they can be attacked from the network.
I’m guessing that applications are called out separately from systems because scanning network-enabled applications for vulnerabilities is a different process than enumerating software versions in a system.
For example, scanning a Linux operating system may not detect flaws in the WordPress website hosted by the server. Thus both are required separately because NIST doesn’t want anyone to forget to scan the website or database.
Most simple software like Microsoft Office, Chrome, and Adobe Acrobat would be vulnerability scanned as part of the organizational system it is installed on.
“𝒑𝒆𝒓𝒊𝒐𝒅𝒊𝒄𝒂𝒍𝒍𝒚”…
This just means “at least once per year”.
“𝒘𝒉𝒆𝒏 𝒏𝒆𝒘 𝒗𝒖𝒍𝒏𝒆𝒓𝒂𝒃𝒊𝒍𝒊𝒕𝒊𝒆𝒔 𝒂𝒓𝒆 𝒊𝒅𝒆𝒏𝒕𝒊𝒇𝒊𝒆𝒅”…
This is a pain point which probably causes the most failures. You need to be able to demonstrate running a vulnerability scan against your environment in response to a newly discovered vulnerability.
For example, anyone remember Log4Shell, affecting Apache log library Log4j, which is used by a ton of different applications?
If your network existed in 2021, an assessor might ask you for the vulnerability scan you performed in response to Log4Shell. 😱
You didn’t run one? Doom!
⏰ Perform continuous vulnerability scans? If you are automatically performing vulnerability scans within a day or two of each vulnerability detection, it is my opinion that you are exceeding the expectation for this requirement.