Our DIBCAC re-assessment for the certification we need to remain a C3PAO came at a busy time for Kieri. From November 2024 through February 2025, we nearly doubled in size, from 15 full-time employees to nearly 30 full-time employees with Read More
Category: Latest CMMC news
CMMC 101 – Final Rule Version
The DoD released a “CMMC 101” overview which does a good job of describing the CMMC program at a high level. If you need to review CMMC with your company executives, this might be the best presentation to use. Of Read More
32CFR Final Rule Published – CMMC goes live!
On October 15, 2024, the Federal Register was updated with the CMMC Final Rule (32CFR). This rule will be fully effective on December 15, 2024. Link to Federal Register for CMMC This link goes to the U.S. Government’s Federal Register Read More
Podcast – CMMC Scoping with Climbing Mt CMMC
Amira Armond from Kieri Solutions – Authorized C3PAO, and Bobby Guerra from Axiom.tech talk about CMMC scoping. Topics discussed: This podcast by Climbing Mount CMMC is oriented toward education for Managed Services Providers who support clients in the Defense Industrial Read More
Review of CMMC Registered Practitioner Training
This post was originally written in September 2020. It was updated in July 2024. In September 2020, I took the Cyber-AB’s Registered Practitioner training course. We aren’t allowed to reproduce the content, so you won’t learn any secrets from me, Read More
NCDMM one of first companies to get “110” JSVA
What it is like to be CMMC assessed by Kieri Solutions? Want to learn about the great work that National Center for Defense Manufacturing & Machining (NCDMM) is doing with over 200 Alliance Partners? Check out this interview with Jason Read More
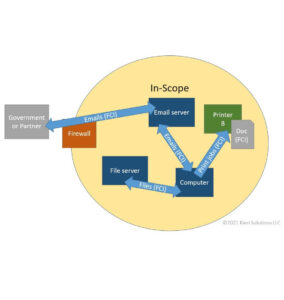
Top 5 misconceptions about building a CMMC Level 2 network
Almost every defense contractor makes one or more of these design errors when they start building their CMMC Level 3 network
CMMC Final Rule moves to OIRA review
Exciting morning in Defense Contractor land! The CMMC Final Rule (32 CFR) has moved to its last phase before publication. It is in OIRA review (Office of Information and Regulatory Affairs – the technical editors/reviewers for government regulations). All the Read More
DoD estimates CMMC paperwork burden
“OSCs must retain artifacts used as evidence for the assessment for the duration of the validity period of the certificate of assessment, and at minimum, for six years from the date of certification assessment as addressed in 32 CFR 170.17(c)(4). Read More
How to get a CMMC Audit or Assessment
You’re in the right place if the US Government or your prime contractor told you that you need to get a CMMC certification. What is CMMC? CMMC is an initialization for the term “Cybersecurity Maturity Model Certification”. This term was Read More
C3PAO Shopping Guide
The National Defense Information Sharing & Analysis Center (ND-ISAC) is pleased to announce the release of a “C3PAO Shopping Guide for Small & Medium-Sized Businesses.” The guide was created through a team effort among participants in ND-ISAC’s Small & Medium-Sized Business Read More
CMMC JSVA program – what you need to know
Some tidbits about CMMC’s Joint Surveillance Voluntary Assessment (JSVA) program that you might not know: JSVA program is intended to train C3PAOs and CMMC Assessors 1) The DoD is essentially using the JSVA program to train and vet our private Read More
When do you need a new assessment? What can change?
Information systems are constantly changing. Especially if they are functional, production systems, supporting real use. Workstations and servers break. Technology becomes obsolete. New solutions are implemented in response to changing functional requirements. One thing we don’t know, in the CMMC Read More
What is “Certified” as the result of assessment??
What exactly is “certified” when you go through a CMMC or Joint Surveillance assessment, or when you self-assess your environment and report it to the DoD? What does it mean when you want to bid on contracts using this certification? Read More
CISA Proposed Rule – Mandatory Reporting of Cyber Incidents
CISA releases proposed rule for mandatory reporting of cyber incidents by Critical Infrastructure and State, Local, Territorial Governments. To my understanding, this will affect all DoD contractors with DFARS 252.204-7012 in their contracts, as well as most Federal Contractors. For Read More
CMMC assessment? Don’t let pride take you down
Getting CMMC assessed? Some advice.. Listen to your assessor If we say that your evidence isn’t related to the requirement being inspected, or especially the critical words “I think you have misinterpreted this requirement”, instead of getting mad, take a Read More
How to submit a NIST SP 800-171 self assessment to SPRS
Answers to common questions about how to submit your NIST SP 800-171 self assessment to SPRS. Register an account, how to handle multiple…
FedRAMP “Equivalent” Memo released
Must read for anyone with DFARS 252.204-7012 in their contract! FedRAMP equivalent is defined for DFARS 252.204-7012 Summary: FedRAMP Equivalency, as used in DFARS 252.204-7012, means that the cloud provider has been third-party-validated, with a full audit, by a FedRAMP Read More
CMMC Level 2 Self-Assessment Analysis
Our sponsor, Kieri Solutions, has released an in-depth review and analysis of CMMC Level 2 Self-Assessments according to the CMMC Proposed Rule. Not official guidance for CMMC Proposed Rule This paper is for educational purposes and is not authoritative in Read More
Webinar – CMMC Proposed Rule Review
Our sponsor, Kieri Solutions, produced this webinar to review the hottest topics of the CMMC Proposed Rule. Thanks to Vincent Scott, Brian Hubbard, Jil Wright, and Amira Armond (all Certified CMMC Assessors and Instructors) for providing insightful review and commentary! Read More
CMMC Rule links to text (with December 26 content)!
Here are links to the text of the CMMC Proposed Rule: 32 CFR (CMMC Program) Downloadable PDF of Federal Register text (this version has page numbers): https://public-inspection.federalregister.gov/2023-27280.pdf Federal Register home page for CMMC and comments: https://www.federalregister.gov/documents/2023/12/26/2023-27280/cybersecurity-maturity-model-certification-cmmc-program Docket Information (the rule Read More
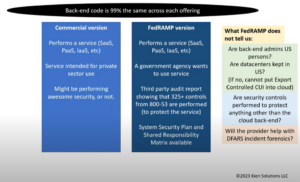
Is GCC-High required to pass CMMC?
Amira Armond (CMMC Instructor, Certified CMMC Assessor, President Kieri Solutions) answers the question “Is GCC-High required to pass a CMMC assessment?” This is actually an explanation of what the FedRAMP program is and is not. This video is meant for Read More
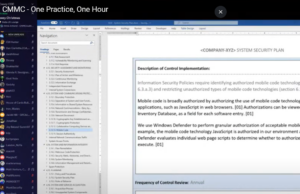
How the secret sauce is made – one practice, one hour
How does a defense contractor create a plan to perform each requirement in CMMC and NIST SP 800-171? Will you fail if you don’t write policy statements which regurgitate each requirement in a ‘shall” form? AKA “𝘚𝘢𝘧𝘦𝘨𝘶𝘢𝘳𝘥𝘪𝘯𝘨 𝘮𝘦𝘢𝘴𝘶𝘳𝘦𝘴 𝘧𝘰𝘳 𝘊𝘜𝘐 Read More
Joint Surveillance Assessment – what is it like?
This is an interview with Jose Rojas (TTC) and Ozzie Saeed (IntelliGRC) about their experience being assessed by Kieri Solutions, an Authorized C3PAO, as part of the Joint Surveillance Voluntary assessment program. Other than the obvious congratulations to both of Read More
CMMC News – October 2023 – the DFARS Rule
Rulemaking Timeline for CMMC DFARS Rule The proposed CMMC Rule has been submitted to the Office of Information and Regulatory Affairs. Several groups (mostly cybersecurity professionals) have met with DoD CIO and OIRA to give recommendations for the rule. Most Read More
What does “monitor” mean in CMMC?
Logan Therrien and Amira Armond from Kieri Solutions (an Authorized C3PAO) discuss the concept of monitoring and how it is evaluated by CMMC assessors. Several assessment objectives in CMMC Level 2 require monitoring. 🔍 the physical facility where organizational systems Read More
Why so few Defense contractors are compliant
𝐇𝐨𝐰 𝐥𝐨𝐧𝐠 𝐝𝐨𝐞𝐬 𝐢𝐭 𝐭𝐚𝐤𝐞 𝐚 𝐜𝐨𝐦𝐩𝐚𝐧𝐲 𝐭𝐨 𝐠𝐨 𝐛𝐚𝐧𝐤𝐫𝐮𝐩𝐭 𝐢𝐭 𝐰𝐡𝐞𝐧 𝐜𝐚𝐧’𝐭 𝐰𝐢𝐧 𝐰𝐨𝐫𝐤? One year? Two? Three? Let me tell you a story about how a system of perverse incentives caused our current cybersecurity situation in the Defense Read More
Podcast – increasing the likelihood of passing CMMC assessments
This podcast by Omnistruct features Amira Armond, John Riley, and George Usi. Recorded in May-June 2023. They discuss the basics of CMMC, the “hardest” requirement (FIPS of course), the aspects that contractors have the most difficulty with, and the status Read More
CMMC Breaking News – July 25, 2023
Today we had two big events in #CMMC and US Federal Contractor Cybersecurity. The Rule for CMMC moved to the Office of Management and Budget. That means a timer has started, 90 days or less, for the review to complete. Expect the Read More
3.13.11 FIPS 140-2 Validated Cryptography
It is time, finally, to talk about the #1 “Other than Satisfied” requirement in 800-171, per historic DIBCAC assessments. 😱 💥 💥 𝐅𝐈𝐏𝐒 140-2 𝐕𝐚𝐥𝐢𝐝𝐚𝐭𝐞𝐝 𝐌𝐨𝐝𝐮𝐥𝐞𝐬 💥 💥 😱 Listen up – I’m going to tell you how to succeed Read More