
This article is provided by Kieri Solutions, an Authorized CMMC Third Party Assessment Organization, offering CMMC assessment services. Thanks to them for sharing some of the secret sauce!
This article is meant to provide short explanations on topics that are commonly misunderstood (and not performed correctly) by defense contractors. It will be updated over time. We’ve done a LOT of research on the CMMC and have decades of experience managing secure military networks, but this is a free article and the answers are summaries, so it is not guaranteed to be 100% correct for you. Talk to a cyber security expert, lawyer, or your contracting officer to be sure.
If you want to add to the question list, please comment below!
Q: What is CMMC or what is FCI / CUI?
Whoa, this article is going to be too advanced for you.
Go read these articles first:
CMMC glossary of terms and definitions
Then come back and read through this article.
Q: Does my company even have FCI?
If you are a prime or subcontractor working on a government contract, any non-public communications related to that contract are probably FCI. If you are a subcontractor to a DoD contract, any non-public communications between you and your upstream contractor about products or services are probably FCI.
FCI is not limited to communications between the Government and yourself. It also applies to communications between companies that are performing a contract.
The exception is a purely Commercial Off-The-Shelf (COTS) product or service. Selling chairs or bolts is not considered FCI as long as there aren’t details about the use (such as “this bolt is used for the F16 landing gear”). If you customize your product or service at all for the government, it is no longer COTS.
Reference: What is FCI in CMMC and how does it affect scope?
Q: Does my company even have CUI?
Controlled Unclassified Information (CUI) is information about specific sensitive topics. The National Archives is responsible for identifying which topics are sensitive enough that the information counts as CUI.
For your company to have Controlled Unclassified Information, you must meet these conditions:
1. You have an official agreement (contract, purchase order, etc) with the United States Federal Government or you support an organization that has an agreement
AND
2. The organization / government provides CUI to you as part of the agreement, or B) You create the CUI on behalf of the agreement
Tip: Just because your company is developing cool technology on a topic that is normally controlled (like weapons systems), does not mean that it is automatically CUI. You need to be performing work as part of active agreement with the Government.
Reference: DFARS 252.204-7012 – Part 1, CDI and Covered Info Systems
Q: What CMMC Level will I need to get?
We expect a new DFARS rule to come out in May 2023 which provides an exact answer to this question.
In the meantime, if you have DFARS 252.204-7012 in your contracts, and there is any chance that you will receive CUI as part of your work for the Department of Defense, you will almost certainly need to comply with CMMC Level 2.
Q: Which of my data needs to be protected under CMMC?
This is harder. CUI and FCI are considered in-scope when they are generated or received as part of performance on a contract.
The government or your partners SHOULD be labeling any CUI when they send it to you…
Tip: Reach out to your contract officer and ask them what their procedure for labeling CUI is. Or ask your partner.
If you create the CUI yourself, as part of a contract, then you need to identify and label it yourself.
Here is a useful graphic showing the protection requirements based on the types of data you have
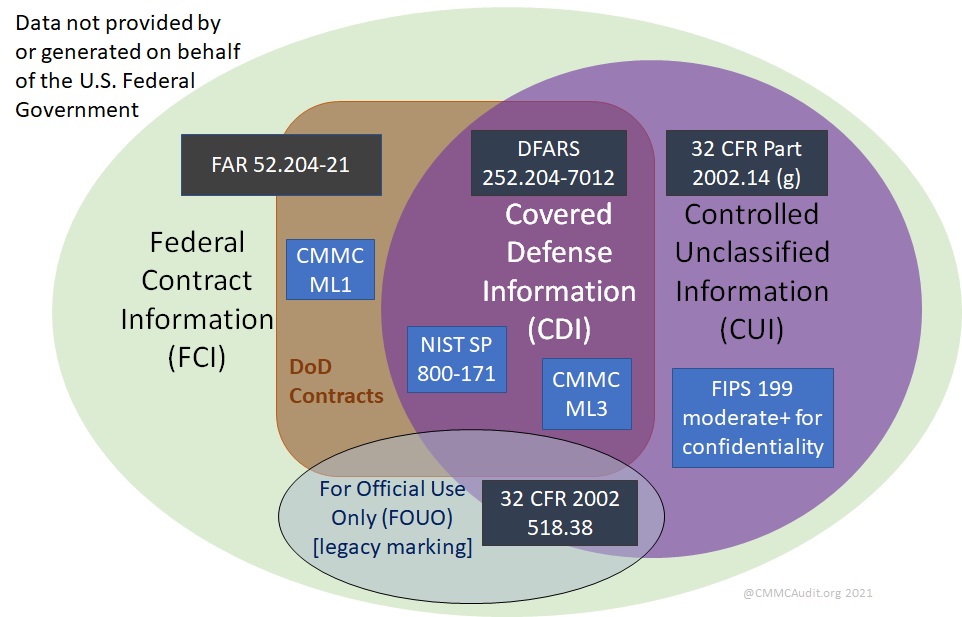
Reference: DoD guidance for CUI
Q: Is it OK to email CUI?
In short, if you are using regular email messages to send or receive CUI, you are doing it wrong.
You should be doing this: “Employ FIPS-validated cryptography when used to protect the confidentiality of CUI.”
That means that when you are sending CUI or storing CUI, it needs to be encrypted. Regular emails are NOT encrypted.
There are solutions which can encrypt your emails in a secure manner, but they don’t encrypt by default, and users often refuse to use them. You need to work with your system administrators to design a solution that works for you.
Q: How do I correctly send and receive CUI?
Very simply, you need to 1) Make sure that you are sending it to an authorized person (double-check that name), and 2) use an encrypted transport of some sort.
Here are some good options for encrypted transport:
- Use encrypted emails
- Employ a secure file share.
- Use AMRDEC SAFE safe.apps.mil to send one-off files (needs a CAC to send, unless recipient creates a request for you).
Tip: Have a conversation with your Government counterparts and your partners to make a plan for how everyone will send CUI.
Q: Is my cloud vendor OK for CMMC Level 2 ?
Cloud vendors are in-scope for CMMC level 2 assessments.
Go check the FedRAMP Marketplace. Search for your vendor’s name. Not in the list? You may have a big problem…
Don’t stop yet. Even if they were in the list, you need to check with your vendor and ask if they are DFARS compliant, and ask if your license is for that FedRAMP cloud.
Tip: If you didn’t specifically ask for their government solution (and pay more money), you probably aren’t on it.
Reference: CUI and Cloud Vendors – do you need FedRAMP?
Q: How do I tell if cloud security is “equivalent to FedRAMP”?
In DFARS 252.204-7012, the paragraph about cloud provider security states “the Contractor shall require and ensure that the cloud service provider meets security requirements equivalent to […] FedRAMP Moderate baseline…”
The DoD Procurement Cyber FAQs states:
Q115: The DFARS states “the Contractor shall require and ensure that the cloud service
provider meets security requirements equivalent to those established by the Government for
the Federal Risk and Authorization Management Program (FedRAMP) Moderate baseline”. If
the cloud provider is not FedRAMP certified, how can a contractor ensure that the cloud
provider meets security requirements equivalent to FedRAMP Moderate?
A115: The contractor can ensure that the cloud provider meets security requirements
equivalent to FedRAMP “Moderate” in the same way the contractor would normally ensure
any services or product being contracted for will meet his requirements. For example, a
cloud service provider (CSP) may choose to provide evidence that it meets the security
requirements equivalent to FedRAMP “Moderate” by providing a body of evidence (BOE)
that attests to and describes how the CSP meets the FedRAMP Moderate baseline security
requirements
(https://www.fedramp.gov/assets/resources/documents/FedRAMP_Moderate_Security_Co
ntrols.xlsx). Examples of items that could be included in such a BOE are a System Security
Plan (SSP) (https://www.fedramp.gov/assets/resources/templates/FedRAMP-SSPModerate-Baseline-Template.docx) that describes the system environment, system
responsibilities, and the current status of the Moderate baseline controls required for the
system, and a Customer Implementation Summary/Customer Responsibility Matrix
(CIS/CRM) (https://www.fedramp.gov/updated-customer-implementation-summary-cisand-customer-responsibility-matrix-crm-templates/) that summarizes how each control is
met and which party is responsible for maintaining that control. Although non-FedRAMP
providers may use different formats, the FedRAMP templates available at the provided links
are representative of the kind of information/evidence that could be provided.
Additionally, per DFARS clause 252.204-7012(b)(3), companies need to apply other
information security measures, if required. When using external cloud services, FedRAMP
moderate generally addresses the security requirements of information categorized as CUI
Basic and most CUI Specified. However, some types of CUI/covered defense information
have additional requirements that have to be addressed. For example, some data such as
export control/ITAR information may require the data be processed and stored in the US
and be administered by US persons. This may dictate what type of FedRAMP moderate
cloud service can be used, as most FedRAMP ‘commercial’ services do not insure data is
stored/processed in the US and by US persons. For this reason, a vendor may say a
‘Government’ version or service is required – it depends on whether the CUI/covered
defense information has specific processing/storage requirements.
Note that some cloud providers will only ensure complete US sovereignty (e.g., all services
are US-based and administered, even if the user is operating outside the US) with their
FedRAMP ‘High’ offerings. Since FedRAMP High is not required to protect CUI in accordance
with DFARS 252.204-7012 (such offerings are a by-product of DoD Cloud Security
Requirements Guide Security Level 4 services made available to non-DoD users), companies
should determine whether their particular situation requires use of a providers FedRAMP
‘High’ services to meet any US data sovereignty requirements.
Q: How much will CMMC assessment cost?
Good question. Market forces will probably be in charge of this. You should ask Kieri Solutions (the Authorized C3PAO that sponsors cmmcaudit.org) for a free quote and see what they say! Contact: info@kieri.com
Q: Is there a CMMC easy button? Can I just outsource this?
If you outsource any of your cybersecurity for CMMC, you will still need to prove that the outsourced company is performing each CMMC requirement. This is easiest done if the other company has their own CMMC certificate at an equivalent or higher level.
The best easy button is avoiding dealing with CUI. Even if your employees handle sensitive information, you might be able to avoid the problem by … 1) Using a partner’s network (which is CMMC-ready), 2) Use a government network.
Cloud vendors who advertise that their solution meets CMMC requirements normally just mean technical items like FIPS-validated cryptography. For example, even though Microsoft GCC High can handle many technical requirements, they aren’t going to automatically make your laptops secure or do background checks on your staff. No easy button there.
Reference: Where is the Easy Button for CMMC? Why MSPs may be the solution.
Q: Are mobile phones allowed at level 2?
I recommend getting an in-depth evaluation from a cybersecurity consultant for this question.
To know the answer, you need to go through ALL the CMMC requirements and evaluate them against your mobile phones. Can you secure your phones, or do they lack the ability for some requirements?
Q: Is public WI-FI allowed at level 2?
I don’t know of anyone who has failed an audit because their employees used hotel WI-FI. But it is not recommended, and most organizations prohibit public hotspots.
Using zero-trust architecture, smart software firewalls, and VPNs are ways to help protect your employee’s laptops when they travel.
The best practice for traveling workers is to issue them cellular hotspot devices. Yes this costs money.
There is precedent for allowing workers to use their home WI-FI, but you will want to couple this with cyber-hygiene training and a remote work agreement.
Q: Should I buy a set of policies for CMMC?
Maybe? It is just money, after all.
A lot of the time, when a company buys a set of $$policies, they just download them and ignore them.
Your policies need to reflect your organization’s actual practices. It is worse to have a policy that says “All systems will be patched within 5 days” and not patch your system, than it is to have a policy that says “We don’t believe in patching” and not patch your system. This is tongue-in-cheek, because both of those would totally fail, but I hope you understand the idea. Not following your policies is a problem.
Bad policies require a doctorate degree to understand and are never looked at. Good policies are written in plain English, and are referenced often.
Check our resources page for links to free policy templates. The problem with the free templates available right now is that they don’t describe each practice for CMMC individually. This is a requirement for CMMC Maturity Level 2 and above.
Kieri Solutions offers a full set of documentation designed for CMMC Level 2 which specifically addresses each practice and help you build evidence. You can request a free demo to see it in action by emailing info@kieri.com
There are other paid vendors that sell policies written for the CMMC. No matter what, you need to budget some time to customize the policies to fit your exact business, and plan to bring in your high level executives to support and enforce the policies.
Q: Should I sign up for a Compliance Platform?
Please be really careful about this. When you enter data into a cloud-based Compliance Platform (a website that lets you automatically create your CMMC compliance documents), you are putting your vulnerability data into that cloud vendor. At the least, make sure they are located in the U.S.A and owned by U.S. Citizens. There have already been a few GRC platforms hosted by companies in China and Russia, advertising that they are a great place to store your CMMC readiness information. Strange thing to be offshored, since CMMC is for US defense contractors.
Reference: The first few paragraphs of this CMMC resources article
Q: Can I use a Managed Service Provider?
There isn’t much official information available on this topic. (If you know of some, please comment)
Even at level 1, you need to prove that your managed service provider does the level 1 requirements as they relate to your information system.
At level 2, it looks like there will be stringent requirements for provider companies. For example, they might be required to certify their information system at CMMC level 2 too.
Since Managed Service Providers typically have multiple unnamed staff and remote management capabilities into your network, it is very risky to use an MSP unless they are cybersecurity super-stars AND you have a contractual agreement with them to perform CMMC level 2 screening and security on their own people and network. You should also consider having the Managed Service Provider use YOUR laptops and servers to manage your environment, rather than using their own equipment. This reduces the risk that the Managed Service Provider will need a full assessment of their own information system.
Q: What about paying for a CMMC Level 2 system?
Two possibilities here:
- A technical solution (such as an email system) that says you just need to use them and you will be CMMC compliant.
Among professionals, this is considered blatant false advertising because there are no technical solutions which provide CMMC Level 1 , 2, or 3 compliance. A huge amount of CMMC compliance is manual processes performed by humans. Things like authorizing Debbie’s accounts and identifying the roles and permissions she should have. Performing risk assessments to determine a path forward when your manufacturing software is vulnerable but no patch is available. Monitoring physical facilities security.
2. Renting computers, servers, and MSP services in a package that is designed to replace your IT department entirely. This is actually a workable model for about 90% of the CMMC requirements. As long as the client is forced to perform the activities that are specific to them (such as requesting accounts and escorting visitors), this could work.
There is a concern about whether hosting lots of different clients in your (un-segmented) information system would pass an assessment. Whether you could get one CMMC level 2 assessment for a “model” information system in order to make segmenting affordable.
I have heard of at least two companies selling “Guaranteed CMMC Level 2” systems. This is an immediate turn-off for most professionals in the CMMC space because there are so many unknowns still that no one can be certain they will pass CMMC Level 2. What happens if the company doesn’t pass? Maybe the clients don’t need to pay? But that still means huge disruption to the client revenue and a huge hassle trying to change to a different network.
Until someone has successfully gotten a certification while hosting disparate customers, there isn’t any sure path forward.
Where is the Easy Button for CMMC? Why MSPs may be the solution.
Q: Can I use consultants?
Note: Before CMMC rolls out and DFARS 252.204-7012 is updated, there doesn’t seem to be any rule against using IT consultants. However, in the next few months, things are expected to change.
At level 1, your consultant needs to make sure their own information system meets level 1 requirements too.
For level 2, if a consultant needs to use their own information system to deal with your CUI (including sensitive network info), then you should verify that they meet CMMC level 2 requirements.
Because consultants are named persons, you should be able to avoid vendor risk by having consultants use your company’s information systems and processes. This means performing background screens, signing agreements, providing training, issuing accounts, and issuing a laptop as though they were an employee. By having consultants use your information system while working for you, they keep all CUI within the scope of your existing network.
Q: Can my employees use home computers to work?
No. Edited: Mostly no (see comments).
Even at CMMC level 1, the practices say that you need to control and limit the use of personal devices connecting to your network or information. The example describes not allowing employees to work on Federal Contract Information using personal devices. At level 1, if you require security measures on home computers (like antivirus, patches, passwords, and restricting use by random family and friends), you can probably get away with it. But at that point, are they still “home” computers?
For higher levels that deal with CUI, the answer is HECK NO!
If your employees need to work from home, you should ideally be issuing them a company laptop or set up virtual desktops, or both. Yes, this costs money.
Reference: CMMC Level 1 Assessment Guide
Q: Can my employees use personal phones for email?
The very first requirement of CMMC says that you need to “limit information system access to … authorized devices.”
If your email has Federal Contract Information (FCI) in it *hint: it does*, then connecting personal phones to email would add them to the list of devices that need to meet security requirements. At Level 1, this isn’t too hard, but you need to show that you authorized each phone before it connects to your email system.
This security requirement is one where your users will try to circumvent any policy or training you give them. I recommend using technical configurations to lock down access wherever possible.
Reference: CMMC Level 1 Assessment Guide
Q: When will the CMMC actually affect me?
There has been a lot of fear-mongering out there. If a salesperson threatens that you will lose your Government contracts after December 2020, they are using strong arm tactics and shouldn’t be trusted.
According to what the DoD and CMMC Accreditation Body has released publicly, the CMMC will be a gradual roll-out over 5 years (2026).
Starting around June 2023, new and renewing contracts will have the OPTION of including a CMMC level requirement in their Request for Proposals.
Like all government RFPs, they want to have some competition on their bids. So before releasing a CMMC requirement, the procurement officer is probably going to verify that at least two potential bidders have the certification. This means that procurement officers either need to wait for lots of companies to get certified, or give advance warning to potential bidders that the proposal will require CMMC.
Short opinion: Almost all contractors will have a few years before they will want to bid on a CMMC-required contract. This is good, because for level 2, most companies will need a year or more to prepare.
Q: Will CMMC level 2 companies get priority assessments?
The CMMC-AB has stated that they will facilitate priority assessments for bidders on contracts that require CMMC. The CMMC level required by the contract doesn’t matter. So if a contract comes out for bid in 2023, companies bidding on it should be given assessment priority over companies that aren’t bidding until 2024 or 2025.
Q: Should I send my internal staff to CMMC training?
Mixed. You don’t need any certifications or titles from the CMMC-AB to help a company prepare for an assessment. Neither Registered Practitioner or the Certified Assessor tracks seem to be geared toward internal employees (they require association with consulting or assessment organizations). But having someone on your team who can give input on whether a practice is passing or failing is invaluable.
The Certified CMMC Professional (CCP) training is a good source of insight into what you need to do to make your company compliant. Many Managed Service Providers are sending their staff through this training. It includes both requirements for implementation as well as instructions on how to judge whether a requirement is performed or not. This is invaluable for internal staff.
Q: Can my employees discuss CUI over the phone?
Phone conversations that occur over Common Carrier and analog telephone lines (POTS) are not in-scope for DFARS 252.204-7012 or CMMC at this point. That means that an assessor should not ask you questions about your Common Carrier and POTS phone conversations during an assessment.
However, voice conversations that occur over data channels such as Microsoft Teams, WebEx, and some types of VOIP systems ARE in-scope and need to be protected. Voicemail systems can also be in-scope because they store the recording in data form.
The best answer for real security is that your employees shouldn’t discuss CUI over regular phonelines. You should probably train your staff to only discuss CUI using authorized programs or tools.
Reference: DFARS Cyber FAQ, question #103
This article was submitted by Kieri Solutions. Thanks to them for their insights!
I hope this article is helpful to you! If you want to add a question to the list, please comment!
Subscribe to our newsletter and connect with me on LinkedIn for timely news and articles like this!
V. Amira Armond (CISSP, CISA, PMP, MBA) is a computer systems architect, cyber-security consultant, and owner of Kieri Solutions LLC. She specializes in CMMC preparation and DFARS 252.204-7012 compliance, and designing secure and resilient enterprise systems for private sector and the DoD.
As a “Proposal development outsourcing firm” providing proposal writers who work with federal contractors to develop proposal packages for contracts like MAPS, etc., are they also required to get CMMC 2.0 Level 1 certification?
Hi, Interesting feed, thank you.
We´re discussing the supply chain and whether or not a map of a component of a product should be considered a CUI. Would appreciate feedback or information on where we can find further guidance.
Great read. I’m curious to know if you have an opinion as to what a reasonable expectation is for someone with a strong (30+ yr) Systems Integration / MSP background to reach an CA-3 assessor level? I’m about to begin the process and I can’t seem to find any specific information about needing to hold any level for a particular amount of time before moving onto the next step. I’m currently a Security+ and CySA+ holder, but I get the sense that the lack of DOD-specific experience could be a barrier to success. I look forward to reading more!
Ms. Armond – apologies.
Mr. Armond
Not wanting to argue the point about not being able to use BYOD, but can you please cite the controls that prohibit it?
It seems to me that AC.1.1003 applies at ML1, but it doesn’t rule out the use of BYOD – and would it cover the use of smart phones too?
Thank you sir.
Hello Cary,
Great question!
I think control AC.1.003 “Verify and control/limit connections to and use of external information systems.” is the one that applies to this discussion. The appendix says “Control and limit personal devices like laptops, tablets, and phones from accessing the company networks and information.” Keep in mind this advice is for level 1.
I come at this from the perspective of military networks, which is closely applicable to CMMC Level 3-4-5. It is less applicable to level 1 and 2. I would say that there is some leeway to allow personally-owned devices at level 1 and 2, but they need to be “controlled and limited”.
How does one control and limit devices? Using a BYOD policy, like you mentioned, which requires security measures. Once you start requiring that phones or laptops have PINs, updated operating systems, encryption, and malware scanning, do those devices really count as “home” devices anymore? Do you allow the children to use the same laptop as your employee does? If not, it doesn’t count as a home device anymore.
Hopefully the DoD will provide assessment guidelines and examples of audit failures soon, so that we understand what will fail an audit. That is the ultimate answer. In the meantime, we are just trying to make sure we are on the passing side of wherever that line is.
I’ve updated the FAQ slightly based on this conversation. Thanks!