“OSCs must retain artifacts used as evidence for the assessment for the duration of the validity period of the certificate of assessment, and at minimum, for six years from the date of certification assessment as addressed in 32 CFR 170.17(c)(4). Read More
Tag: CMMC assessment
How to get a CMMC Audit or Assessment
You’re in the right place if the US Government or your prime contractor told you that you need to get a CMMC certification. What is CMMC? CMMC is an initialization for the term “Cybersecurity Maturity Model Certification”. This term was Read More
Policy templates and tools for CMMC and 800-171
This page has links and reviews of available templates and tools relating to the CMMC and NIST SP 800-171 **Updated April 3, 2024** Please help others in the community by leaving a comment with resource links! Policies Templates Kieri Compliance Read More
CMMC assessment? Don’t let pride take you down
Getting CMMC assessed? Some advice.. Listen to your assessor If we say that your evidence isn’t related to the requirement being inspected, or especially the critical words “I think you have misinterpreted this requirement”, instead of getting mad, take a Read More
CMMC Level 2 Self-Assessment Analysis
Our sponsor, Kieri Solutions, has released an in-depth review and analysis of CMMC Level 2 Self-Assessments according to the CMMC Proposed Rule. Not official guidance for CMMC Proposed Rule This paper is for educational purposes and is not authoritative in Read More
Joint Surveillance Assessment – what is it like?
This is an interview with Jose Rojas (TTC) and Ozzie Saeed (IntelliGRC) about their experience being assessed by Kieri Solutions, an Authorized C3PAO, as part of the Joint Surveillance Voluntary assessment program. Other than the obvious congratulations to both of Read More
What does “monitor” mean in CMMC?
Logan Therrien and Amira Armond from Kieri Solutions (an Authorized C3PAO) discuss the concept of monitoring and how it is evaluated by CMMC assessors. Several assessment objectives in CMMC Level 2 require monitoring. 🔍 the physical facility where organizational systems Read More
Podcast – increasing the likelihood of passing CMMC assessments
This podcast by Omnistruct features Amira Armond, John Riley, and George Usi. Recorded in May-June 2023. They discuss the basics of CMMC, the “hardest” requirement (FIPS of course), the aspects that contractors have the most difficulty with, and the status Read More
3.13.11 FIPS 140-2 Validated Cryptography
It is time, finally, to talk about the #1 “Other than Satisfied” requirement in 800-171, per historic DIBCAC assessments. 😱 💥 💥 𝐅𝐈𝐏𝐒 140-2 𝐕𝐚𝐥𝐢𝐝𝐚𝐭𝐞𝐝 𝐌𝐨𝐝𝐮𝐥𝐞𝐬 💥 💥 😱 Listen up – I’m going to tell you how to succeed Read More
What are Spot Checks for?
𝐂𝐌𝐌𝐂 𝐀𝐬𝐬𝐞𝐬𝐬𝐦𝐞𝐧𝐭 𝐒𝐩𝐨𝐭 𝐂𝐡𝐞𝐜𝐤𝐬 “𝘐𝘧 𝘤𝘰𝘯𝘵𝘳𝘢𝘤𝘵𝘰𝘳’𝘴 𝘳𝘪𝘴𝘬-𝘣𝘢𝘴𝘦𝘥 𝘴𝘦𝘤𝘶𝘳𝘪𝘵𝘺 𝘱𝘰𝘭𝘪𝘤𝘪𝘦𝘴, 𝘱𝘳𝘰𝘤𝘦𝘥𝘶𝘳𝘦𝘴, 𝘢𝘯𝘥 𝘱𝘳𝘢𝘤𝘵𝘪𝘤𝘦𝘴 𝘥𝘰𝘤𝘶𝘮𝘦𝘯𝘵𝘢𝘵𝘪𝘰𝘯 𝘰𝘳 𝘰𝘵𝘩𝘦𝘳 𝘧𝘪𝘯𝘥𝘪𝘯𝘨𝘴 𝘳𝘢𝘪𝘴𝘦 𝘲𝘶𝘦𝘴𝘵𝘪𝘰𝘯𝘴 𝘢𝘣𝘰𝘶𝘵 𝘵𝘩𝘦𝘴𝘦 𝘢𝘴𝘴𝘦𝘵𝘴, 𝘵𝘩𝘦 𝘢𝘴𝘴𝘦𝘴𝘴𝘰𝘳 𝘤𝘢𝘯 𝘤𝘰𝘯𝘥𝘶𝘤𝘵 𝘢 𝘭𝘪𝘮𝘪𝘵𝘦𝘥 𝘴𝘱𝘰𝘵 𝘤𝘩𝘦𝘤𝘬 𝘵𝘰 𝘪𝘥𝘦𝘯𝘵𝘪𝘧𝘺 𝘳𝘪𝘴𝘬𝘴. 𝘛𝘩𝘦 𝘭𝘪𝘮𝘪𝘵𝘦𝘥 𝘴𝘱𝘰𝘵 𝘤𝘩𝘦𝘤𝘬(𝘴) 𝘴𝘩𝘢𝘭𝘭 𝘯𝘰𝘵 𝘮𝘢𝘵𝘦𝘳𝘪𝘢𝘭𝘭𝘺 𝘪𝘯𝘤𝘳𝘦𝘢𝘴𝘦 𝘵𝘩𝘦 Read More
3.11.1 Periodically assess the risk to organizational operations
3.11.1 𝐏𝐞𝐫𝐢𝐨𝐝𝐢𝐜𝐚𝐥𝐥𝐲 𝐚𝐬𝐬𝐞𝐬𝐬 𝐫𝐢𝐬𝐤…This is the fourth-most “Other than satisfied” #CMMC requirement. Periodically assess the risk to organizational operations (including mission, functions, image, or reputation), organizational assets, and individuals, resulting from the operation of organizational systems and the associated processing, storage, or Read More
3.11.2 Scan for Vulnerabilities
Scan for vulnerabilities….This the fifth-most “Other than satisfied” #CMMC requirement with an 18% fail rate. 3.11.2 𝐒𝐜𝐚𝐧 𝐟𝐨𝐫 𝐯𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐢𝐞𝐬 𝐢𝐧 𝐨𝐫𝐠𝐚𝐧𝐢𝐳𝐚𝐭𝐢𝐨𝐧𝐚𝐥 𝐬𝐲𝐬𝐭𝐞𝐦𝐬 𝐚𝐧𝐝 𝐚𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐩𝐞𝐫𝐢𝐨𝐝𝐢𝐜𝐚𝐥𝐥𝐲 𝐚𝐧𝐝 𝐰𝐡𝐞𝐧 𝐧𝐞𝐰 𝐯𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐢𝐞𝐬 𝐚𝐟𝐟𝐞𝐜𝐭𝐢𝐧𝐠 𝐭𝐡𝐨𝐬𝐞 𝐬𝐲𝐬𝐭𝐞𝐦𝐬 𝐚𝐧𝐝 𝐚𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐚𝐫𝐞 𝐢𝐝𝐞𝐧𝐭𝐢𝐟𝐢𝐞𝐝. “𝒐𝒓𝒈𝒂𝒏𝒊𝒛𝒂𝒕𝒊𝒐𝒏𝒂𝒍 𝒔𝒚𝒔𝒕𝒆𝒎𝒔”…This is an example of Read More
3.3.3 Review and Update Logged Events
This is #6 in the series of most common failed requirements as assessed by the DoD’s Cyber Assessment Center. This requirement is another example of misunderstanding == failing (alongside the other top 10 requirements). Most people do not understand what Read More
3.3.5 Correlate Audit Processes
NIST SP 800-171 3.3.5 𝐂𝐨𝐫𝐫𝐞𝐥𝐚𝐭𝐞 𝐚𝐮𝐝𝐢𝐭 𝐫𝐞𝐜𝐨𝐫𝐝 𝐫𝐞𝐯𝐢𝐞𝐰, 𝐚𝐧𝐚𝐥𝐲𝐬𝐢𝐬, 𝐚𝐧𝐝 𝐫𝐞𝐩𝐨𝐫𝐭𝐢𝐧𝐠 𝐩𝐫𝐨𝐜𝐞𝐬𝐬𝐞𝐬 𝐟𝐨𝐫 𝐢𝐧𝐯𝐞𝐬𝐭𝐢𝐠𝐚𝐭𝐢𝐨𝐧 𝐚𝐧𝐝 𝐫𝐞𝐬𝐩𝐨𝐧𝐬𝐞 𝐭𝐨 𝐢𝐧𝐝𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐨𝐟 𝐮𝐧𝐥𝐚𝐰𝐟𝐮𝐥, 𝐮𝐧𝐚𝐮𝐭𝐡𝐨𝐫𝐢𝐳𝐞𝐝, 𝐬𝐮𝐬𝐩𝐢𝐜𝐢𝐨𝐮𝐬, 𝐨𝐫 𝐮𝐧𝐮𝐬𝐮𝐚𝐥 𝐚𝐜𝐭𝐢𝐯𝐢𝐭𝐲. This is the 8th most likely requirement to be “other than satisfied” by defense contractors, according Read More
CMMC Scoping for Level 2
This video is provided by Amira Armond and Jil Wright (CMMC Provisional Assessors and Provisional Instructors) from Kieri Solutions, an Authorized C3PAO. Topics discussed in the video are: This content is way more than the CCP course blueprint covers and more in-depth than what is Read More
CMMC Scoping for Level 1
This video is provided by Amira Armond and Jil Wright (CMMC Provisional Assessors and Provisional Instructors) from Kieri Solutions, an Authorized C3PAO. Topics included are: Enjoy, and don’t forget to subscribe to our YouTube channel for lots of other CMMC Read More
Excuses that won’t work for your CMMC assessment
Public Safety Announcement for #CMMC and DIBCAC assessments of 800-171 compliance. “My _________ is scheduled to occur in January and we haven’t reached January yet.” – said too many Organizations Seeking Certification Do not try to use this excuse to explain why Read More
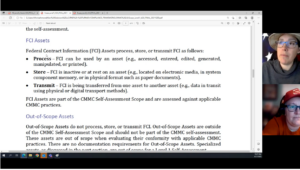
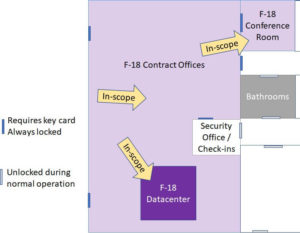
CMMC Scope – are you ready for an assessment?
This article gives examples and explanations of how to identify your CMMC scope to an assessor when you are planning…
CMMC Assessment Part 3 – Interview with Jeff Dalton
This is Part 3 of our CMMC Assessment series with Jeff Dalton (the lead trainer of the CMMC Provisional Assessors). Q&A about assessments!
CMMC-AB Jeff Dalton – the CMMC Assessment Process – Part 2
Second interview with Jeff Dalton (CMMC-AB) about the CMMC assessment process. Topics relevant to every defense contractor, non-technical.
CMMC-AB Jeff Dalton – the CMMC Assessment Process – Part 1
Interview with Jeff Dalton (CMMC-AB) about CMMC assessments. Who is authorized to perform assessments? When should you do a pre-assessment? Can you fix issues found during an assessment?
Introducing the CMMC Kill Chain – Zero to full compliance
Author: Tom Cornelius| Senior Partner at ComplianceForge | Founder & Contributor at Secure Controls Framework (SCF) Originally published on LinkedIn on October 19, 2020 The concept of creating a “CMMC Kill Chain” started off as a bit of a dare… kind Read More
When is a conformity assessment not a conformity assessment? (hint – it is CMMC)
Author: Tom Cornelius| Senior Partner at ComplianceForge | Founder & Contributor at Secure Controls Framework (SCF) Originally published on LinkedIn on August 13, 2020 This episode of Coffee Thoughts With Tom addresses CMMC as a conformity assessment, since conformity assessments are intended Read More