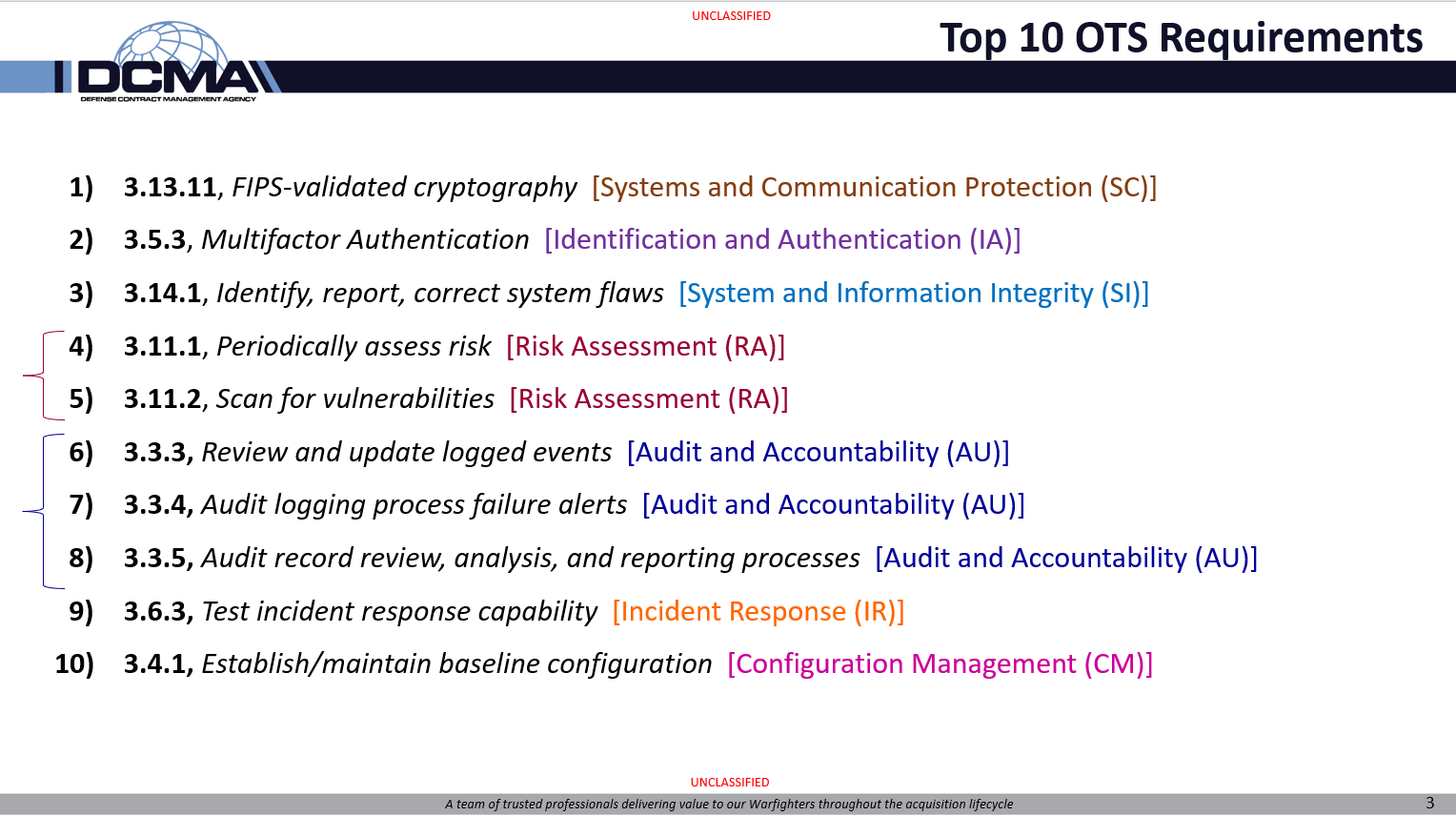
This is #6 in the series of most common failed requirements as assessed by the DoD’s Cyber Assessment Center.
This requirement is another example of misunderstanding == failing (alongside the other top 10 requirements). Most people do not understand what is expected for 3.3.3.
To “review and update logged events”, you must consider 𝐰𝐡𝐢𝐜𝐡 𝐞𝐯𝐞𝐧𝐭𝐬 𝘴𝘩𝘰𝘶𝘭𝘥 𝘣𝘦 logged.
Each of our IT systems perform lots of different activities that could be logged. By default, not all events are written to disk and stored. This is because audit logging costs money. Long term storage of logs costs money. A computer could slow down if it tries to log everything that it does (essentially doing 2x the work). A computer might even crash if it uses up all free space on the hard drive with logs. 💾 Anyone else have computers that logged themselves to death, or was it just me? 💾
The 3.3.3 requirement asks you to review the events that are logged and saved to disk by your IT systems. Are there events that should be logged, but aren’t? Are there events that you don’t need to know about, so you can turn logs off?
When the government performs this requirement in-house, they will often create a list of events that affect security. Things like:
– failed logon attempts
– password resets
– account creations
– changing permissions
– changing security settings
The IT department updates logging settings on each system to ensure that the events are logged.
Why would you 𝘳𝘦𝘷𝘪𝘦𝘸 𝘢𝘯𝘥 𝘶𝘱𝘥𝘢𝘵𝘦 the settings? This is done to improve your ability to detect threats. Ideally, you update your log settings proactively, but it is often done because you got your butt whipped by an incident and really wished you had more logging turned on, after the fact.
For example, if your company was attacked by an adversary who plugged in a thumb drive and installed bad software programs without detection, you could respond by modifying your settings to log these new events:
– adding external hard drives
– installing software
Show that you are doing 3.3.3 𝐑𝐞𝐯𝐢𝐞𝐰 𝐚𝐧𝐝 𝐮𝐩𝐝𝐚𝐭𝐞 𝐥𝐨𝐠𝐠𝐞𝐝 𝐞𝐯𝐞𝐧𝐭𝐬 by providing a work log or change ticket as proof that you modified logging settings to increase true detections or to reduce false alarms.
Already have all the logs configured and you’re happy with them? You can try making that argument; it will probably work? Or you can brainstorm some way to improve… that will definitely make your assessor happy.
Hope you are enjoying this content! Kieri Solutions (my company) performs CMMC and 800-171 assessments for defense contractors. We also have a great program to prepare companies for CMMC. Check us out!