3.11.1 𝐏𝐞𝐫𝐢𝐨𝐝𝐢𝐜𝐚𝐥𝐥𝐲 𝐚𝐬𝐬𝐞𝐬𝐬 𝐫𝐢𝐬𝐤…
This is the fourth-most “Other than satisfied” #CMMC requirement.
Periodically assess the risk to organizational operations (including mission, functions, image, or reputation), organizational assets, and individuals, resulting from the operation of organizational systems and the associated processing, storage, or transmission of CUI.
Not hard to do, but often misunderstood.
Let’s break it down.
𝐏𝐞𝐫𝐢𝐨𝐝𝐢𝐜𝐚𝐥𝐥𝐲 = at least once a year
𝐚𝐬𝐬𝐞𝐬𝐬 𝐭𝐡𝐞 𝐫𝐢𝐬𝐤 = the assessor expectation for assessing risk is higher than these three words describe. Refer to NIST Special Publication 800-30 and NIST SP 800-39.
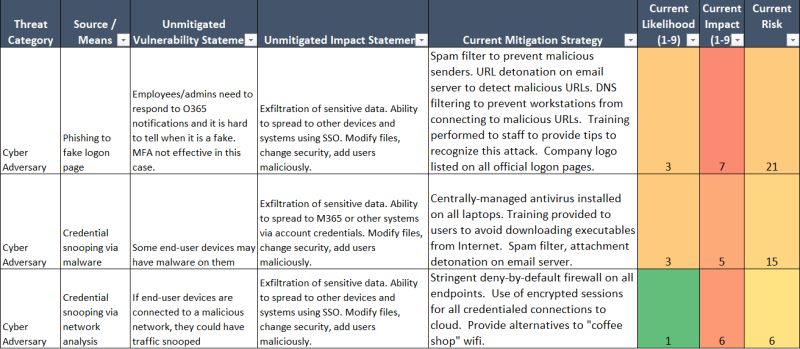
The key components of assessing risk are:
👷 📑 identify your critical assets and functions (such as your CUI)
😈 what threats exist for those assets?
🔪 how would the threats attack those assets?
🔌 what makes the asset vulnerable to the threat?
💀 if there was no mitigation in place to prevent the threat, what impact would occur?
👮 what are you doing to mitigate the threat now?
⏳ how likely is the threat to occur (with current mitigations)?
💸 what impact (with current mitigations)?
✖️ what is the resulting risk #?
🚔 what do you propose to mitigate further (or risk accept)?
📅 if you did this proposed mitigation, what is the new likelihood?
😊 if you did this proposed mitigation, what is the new impact?
✖️ new risk #
𝐭𝐡𝐞 𝐟𝐫𝐞𝐪𝐮𝐞𝐧𝐜𝐲 𝐢𝐬 𝐝𝐞𝐟𝐢𝐧𝐞𝐝 = write down how often you do risk assessments! (see ‘periodically’ above)
𝐨𝐫𝐠𝐚𝐧𝐢𝐳𝐚𝐭𝐢𝐨𝐧𝐚𝐥 𝐨𝐩𝐞𝐫𝐚𝐭𝐢𝐨𝐧𝐬 (𝐢𝐧𝐜𝐥𝐮𝐝𝐢𝐧𝐠 𝐦𝐢𝐬𝐬𝐢𝐨𝐧, 𝐟𝐮𝐧𝐜𝐭𝐢𝐨𝐧𝐬, 𝐢𝐦𝐚𝐠𝐞, 𝐨𝐫 𝐫𝐞𝐩𝐮𝐭𝐚𝐭𝐢𝐨𝐧), 𝐨𝐫𝐠𝐚𝐧𝐢𝐳𝐚𝐭𝐢𝐨𝐧𝐚𝐥 𝐚𝐬𝐬𝐞𝐭𝐬, 𝐚𝐧𝐝 𝐢𝐧𝐝𝐢𝐯𝐢𝐝𝐮𝐚𝐥𝐬 = NIST is kind enough to give you a list of assets to consider.
𝐫𝐞𝐬𝐮𝐥𝐭𝐢𝐧𝐠 𝐟𝐫𝐨𝐦 𝐭𝐡𝐞 𝐨𝐩𝐞𝐫𝐚𝐭𝐢𝐨𝐧 𝐨𝐟 𝐚𝐧 𝐨𝐫𝐠𝐚𝐧𝐢𝐳𝐚𝐭𝐢𝐨𝐧𝐚𝐥 𝐬𝐲𝐬𝐭𝐞𝐦 𝐭𝐡𝐚𝐭 𝐩𝐫𝐨𝐜𝐞𝐬𝐬𝐞𝐬, 𝐬𝐭𝐨𝐫𝐞𝐬, 𝐨𝐫 𝐭𝐫𝐚𝐧𝐬𝐦𝐢𝐭𝐬 𝐂𝐔𝐈 = the risk assessment has to include in-scope information system.
𝐓𝐡𝐞 𝒈𝒐𝒂𝒍 𝐨𝐟 𝐫𝐞𝐪𝐮𝐢𝐫𝐞𝐦𝐞𝐧𝐭 3.11.1 𝐢𝐬 𝐭𝐨 𝐠𝐞𝐭 𝐜𝐨𝐦𝐩𝐚𝐧𝐢𝐞𝐬 𝐭𝐨
1) consider what risks their organization and their CUI faces;
2) decide which risks cannot be accepted
3) apply mitigations to reduce risk.
But an assessor will generally only require evidence that you’ve considered what risk your organization and CUI faces (the first part).
𝐎𝐭𝐡𝐞𝐫 𝐭𝐡𝐢𝐧𝐠𝐬 𝐭𝐡𝐚𝐭 𝐛𝐞𝐧𝐞𝐟𝐢𝐭 𝐟𝐫𝐨𝐦 𝐫𝐢𝐬𝐤 𝐚𝐬𝐬𝐞𝐬𝐬𝐦𝐞𝐧𝐭𝐬:
Contractor Risk Managed Assets. Specialized Assets. Plan of Action. DFARS 252.204-7012 (b)(3). If you don’t know why I reference these, you should find out!
Shameless plug: The Kieri Compliance Documentation (Google it if curious) includes detailed instructions and a partially pre-filled-in template for Risk Assessment. We identified 28 risks that affect almost all small businesses and pre-filled them in to get you started.