Recent Articles
- CMMC Compliance FAQs – Organizations seeking certification
- What is FCI in CMMC and how does it affect scope?
- CMMC Assessment Timeline – How Long Does the Certification Process Take?
- Assessing the Assessor – What can you expect as an OSC?
- CMMC 101 – Final Rule Version
- 32CFR Final Rule Published – CMMC goes live!
- Podcast – CMMC Scoping with Climbing Mt CMMC
- Review of CMMC Registered Practitioner Training
- NCDMM one of first companies to get “110” JSVA
- How to become a CMMC assessor or auditor
Resources to get started with CMMC
Check the menu above for dozens of articles about CMMC, how to prepare your company, and how to become an assessor yourself.
Below are the top 10 links / resources for CMMC and 800-171, ranging from official to informal.
| Resource | Description |
| CMMC Final Rule (32CFR) | This is the U.S. Government Federal Register page for the CMMC Final Rule (32CFR). This is where you can read the regulation which establishes and sets requirements for CMMC. This is the final version of the regulation. |
| CMMC Proposed Rule (48CFR) | This is the U.S. Government Federal Register page for the CMMC Proposed Rule (48CFR). This regulation will be used to apply contract clauses and instructions to contract officers which require contractors to have specific CMMC levels before they can be awarded a DoD contract. This regulation will be updated and re-released before becoming effective, probably in Spring 2024. |
| Official DoD homepage for CMMC | The Department of Defense owns the CMMC program. The Department of Defense is the organization that requires cybersecurity and (in the future) CMMC certification for their contractors. Here is where you can find an FAQ, and more importantly, the official documents published by the DoD which identify their expectations for cybersecurity. |
| Official homepage of the CMMC Accreditation Body | The CMMC Accreditation Body, recently rebranded to “Cyber-AB”, is a private-sector organization which has the responsibility to manage and accredit CMMC assessment companies. The Cyber-AB is mandated to follow the ISO 17011 standard to be an accreditation body. If you want to be a CMMC professional, this organization offers certification and marketplace listings. |
| Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) | This page on the Defense Contract Management Agency’s (DCMA) website has several great resources for defense contractors in the final stages of preparation for 800-171 or CMMC assessment. In particular, the self-assessment database and pre-assessment packages provide insight into the assessment process. |
| CMMC FAQs (Official DoD guidance about 800-171 and DFARS) | This website is an official DoD website, even though it doesn’t look like it. The page has an FAQ document which has some of the best technical clarifications for what the DoD expects their contractors to do for cybersecurity. It is written for existing DFARS 252.204-7012 and NIST SP 800-171 compliance requirements, but these overlap CMMC requirements almost perfectly. This page is expected to become obsolete as the CMMC program becomes more final. |
| NIST SP 800-171 DoD Assessment Methodology | This document gives instructions for performing a NIST SP 800-171 self-assessment and scoring the self assessment so that the results can be entered into SPRS. CMMC uses this document to identify which practices cannot be failed in order to pass a CMMC assessment (the 5-point practices). The document also gives advice about Not Applicable practices. This is the instruction referenced by DFARS 252.204-7019 / DFARS 252.204-7020. |
| Security policy templates, training, and tools | This is a page on cmmcaudit.org (this website), with links to other good cybersecurity resources that will help you get ready. |
| Glossary of CMMC terms and key players | This page gives simple descriptions of many terms and resources related to CMMC. Very helpful to read through when you are starting out. |
| Cooey (CUI) Center of Excellence | This is a Discord server which focuses on CMMC, CUI, 800-171 compliance, and other topics of interest to defense contracting cybersecurity. Most of the top level people in CMMC contribute in this forum. Best source of peer-to-peer information available. |
| C3PAO Stakeholder Forum | This is the website of the C3PAO Stakeholder Forum, an industry group of CMMC assessment companies. The Positions page has articles with recommendations for how to assess CMMC, as well as high-level recommendations for the program as a whole. |
| DFARS 252.204-7012 Discussion | This cmmcaudit.org page is relevant for all companies who are currently contractors for the DoD. It explains existing requirements for cybersecurity, which happen to look a lot like the new requirements for CMMC. |
| Index of all articles on this site | This page has all articles on the site. Remember that CMMC has changed over time, and articles written before 2022 may be outdated. |
How CMMC is supposed to work
All federal contractors are required to protect Federal Contract Information (FCI) using basic cybersecurity described in the FAR 52.204-21. Today, all federal contractors with an active contract have signed an agreement to implement 15 safeguarding requirements as described in the FAR.
Since ~2017, the U.S. Department of Defense (DoD) has required its defense contractors to implement security requirements from NIST Special Publication 800-171 if they handle controlled unclassified information (CUI) on behalf of a contract. Today, each defense contractor with an active contract has signed an agreement to implement 110 security requirements for protection of CUI, as described in the NIST publication.
In 2018-2019, the DoD determined that there was widespread non-compliance by their contractors regarding implementation of these contractual security requirements. As a result, the DoD introduced the Cybersecurity Maturity Model Certification (CMMC) as a verification and enforcement mechanism to ensure that contractors meet their cybersecurity requirements before they are awarded contracts.
The CMMC is a comprehensive framework designed to assess and enhance the cybersecurity posture of defense contractors. This model, pivotal in the defense sector, encompasses three levels of cybersecurity maturity and ensures that CUI is adequately protected when it is shared with contractors by the U.S. Government.
CMMC audits, conducted by certified CMMC assessors, evaluate an organization’s adherence to the required security controls. Through this rigorous assessment and certification process, organizations demonstrate their commitment to safeguarding sensitive information against ever-evolving cyber threats.
CMMC certification involves meeting specific compliance requirements at each CMMC level. Most defense contractors engaged in DoD contracts must undergo a CMMC assessment by a CMMC 3rd Party Assessment Organization (C3PAO), to verify their compliance with these requirements. The process includes an in-depth evaluation of information security practices and policies, ensuring that they align with NIST SP 800-171, using the CMMC framework’s guidelines.
A successful CMMC audit not only confirms compliance but also signifies a contractor’s readiness to handle sensitive defense-related information, reinforcing their role in national security. CMMC audit preparation and compliance services play a critical role in guiding contractors towards achieving and maintaining CMMC compliance.
DoD to contractors: Your cybersecurity is not good enough
The Cybersecurity Maturity Model Certification (CMMC) is an initiative lead by the the office of the DoD’s Chief Information Officer.
DoD contractors who handle Controlled Unclassified Information (CUI) are already required to self-certify compliance with the NIST SP 800-171 set of cybersecurity best practices. However, as pointed out by Ms. Katie Arrington during the CMMC Listening Tour in 2019, self-certification is not working. DoD contractors have been successfully targeted by cyber adversaries because they haven’t fully secured their networks.
To force DoD contractors to implement cybersecurity, the CMMC will require many DoD contractors to get an audit and certification from a third party auditor if they have CUI on their information systems.
We talk about 800-171 too!
Although this website is named “CMMC Audit”, almost all our articles are also relevant to NIST SP 800-171 and DFARS 252.204-7012 compliance. Check our NIST 800-171 menu above for specific information about these current requirements. Articles that discuss CMMC Level 2 or Controlled Unclassified Information will be helpful for your 800-171 journey today.
What you need to know about CMMC
CMMC enforcement timelines
Here is the estimated timeline for CMMC
- Mid 2022 – 20 C3PAOs have been “Authorized”, but cannot yet perform CMMC assessments.
- Mid 2022 – Mid 2023: A few C3PAOs are allowed to do “joint” assessments of 800-171 alongside the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC). So far the rate has been 1 completed per month. These are not CMMC assessments.
- Mid 2022 – 51 C3PAOs have been “Authorized”, but cannot yet perform CMMC assessments. About 100 CMMC Assessors have been certified.
- Late 2023 – New DFARS rule describing the CMMC program is published in draft – this is known as the 32 CFR CMMC rule.
- Mid 2024 – New DFARS rule with the contract clauses requiring CMMC is published in draft – this is known as the 48 CFR CMMC rule.
- Mid 2023 – late 2024 – The rate of Joint Surveillance Voluntary Assessments has ramped up to 3-5 per month. About 100 contractors have been assessed under this program
- October 2024 – 32 CFR CMMC Rule was published in final form and will go into effect around December 15, 2024. Early adopters will be able to be CMMC certified at this point. C3PAOs will be able to perform CMMC assessments on their own schedule.
- (Projected) May 2025 – 48 CFR CMMC Rule will be published in final form and go into effect in Summer 2025. After this point, contractors will need to meet CMMC requirements in order to be awarded a contract.
- (Projected) Mid 2025 – clauses requiring CMMC Level 2 self-assessment with a perfect ‘110’ score start being added to new/renewing contracts.
- (Projected) Late 2025 – clauses requiring CMMC Level 2 certification assessments start being added to a greater % of contracts over time.
- (Projected) Mid 2026 – most new/renewing contracts have switched from CMMC Level 2 self-assessment to CMMC Level 2 certification assessment requirement. Clauses requiring CMMC Level 3 certification assessments start being added to a few % of contracts.
- (Projected) Late 2026 / early 2027 – all DoD contracts require CMMC for award.
CMMC levels and requirements
The DoD recognizes that their contracts have different risk profiles, so each RFP will list a CMMC level requirement ranging from Level 1 (self-assessment) to Level 3 (DIBCAC assessment). Having proof of compliance at that level would be a requirement to win a contract or be accepted as a subcontractor.
The lower level (1) applies to DoD contractors who don’t deal with Controlled Unclassified Information (CUI). I expect most resellers will fit into this category. Other than purchase orders and possibly human resources information, they don’t hold government information on their corporate networks. The security requirements for these levels are much less stringent.
In the middle level (2), DoD contractors handle CUI. This is information like schematics for DoD equipment. Data which lets adversaries reverse-engineer or learn about military capabilities. For example, a shipyard might have maintenance plans for submarine equipment on a CUI network. This requires a level of protection very similar to the current NIST SP 800-171 recommendations.
At the highest level, (3), the CUI being protected is high stakes. These networks will be targeted by cyber adversaries. Examples of this information would be weapon test results or detailed manufacturing schematics. Securing your network up to level 3 is likely to be very expensive.
For more details about the CMMC as an overall program, see CMMC Basics – the Full Details
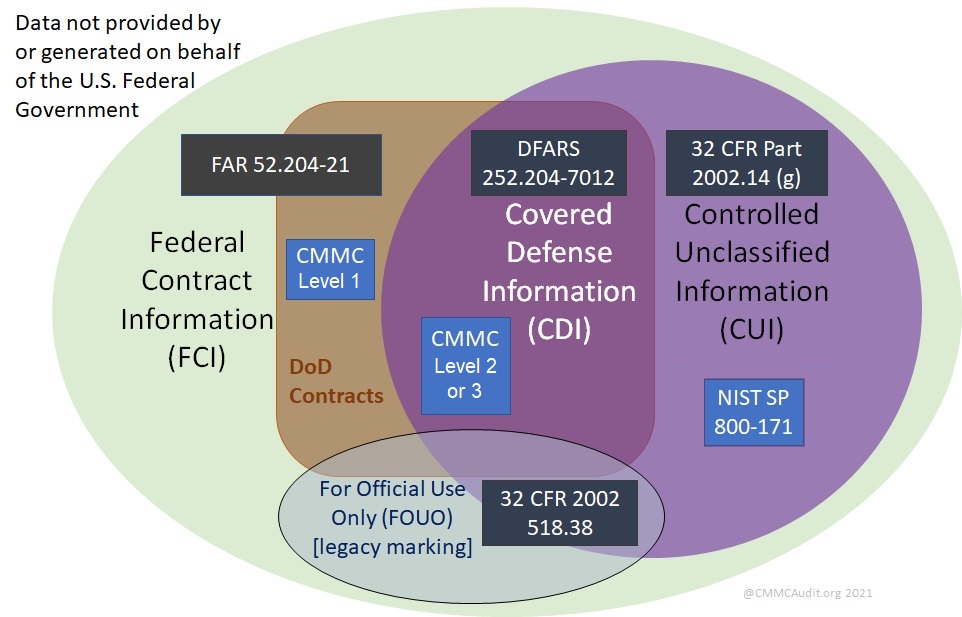
Does CMMC apply to your business?
This infographic describes different types of sensitive but unclassified Federal data and their related cybersecurity requirements.
How to prepare for a CMMC audit
To effectively prepare for a CMMC audit, begin with a comprehensive understanding of NIST 800-171 practices, the CMMC framework and its requirements. Familiarize yourself with the specific CMMC level applicable to your organization and the associated security controls. Prioritize the assessment and improvement of your cybersecurity maturity, focusing on the protection of controlled unclassified information (CUI). Collaborate with a qualified CMMC auditor or assessor for pre-audit preparations, ensuring your security measures are in line with NIST 800-171 and CMMC compliance standards.
Engage in regular security assessments and implement a robust information security system to address potential cyber threats. Utilize CMMC compliance services to guide and streamline your preparation process. Start with your CMMC documentation, including your policies, procedures, and system security plan and work through a self-assessment or gap analysis to find your vulnerabilities. It’s crucial to maintain an ongoing commitment to cybersecurity and compliance, adapting to evolving requirements and threats. Thorough preparation not only facilitates a successful CMMC audit but also reinforces your organization’s security posture, especially when dealing with sensitive defense contracts.
Are you just looking for a CMMC audit provider?
The sponsor of CMMC Audit (Kieri Solutions) is an Authorized CMMC Third Party Assessment Organization. Kieri Solutions is known for supporting defense contractors by publishing free training and advocating to the CMMC-AB and DoD on behalf of contractors. If you need CMMC assessment services, check them out!
Are you just looking for CMMC Consulting?
We encourage you to reach out to the sponsor of CMMCAudit.org, Kieri Solutions, if you like what you see on this website. At the least, they are happy to chat for 30 minutes and point you in the right direction. Having a CMMC assessor help guide you to understand the CMMC framework and provide you with a CMMC guide can drastically increase your chances of success.
CMMCaudit.org is not a representative of the Department of Defense, the CMMC Accreditation Body, or the CMMC Assessors and Instructors Certification Organization. This website is meant to be community resource for CMMC audit (or assessment!) preparation.