On my mind this week has been the CMMC “procedure” maturity requirements at Level 2+.
The process maturity aspect of CMMC is widely overlooked and underestimated by companies preparing for certification. For example, I often hear people say that CMMC Level 3 has +20 requirements compared to NIST SP 800-171’s “110” requirements. This is inaccurate!. CMMC Level 3 adds another 51 “process” requirements in addition to the +20 technical practices, for a total of 181 assessed requirements. In terms of assessment labor, my best guess is that these process requirements add at least 50% to the level of effort involved.
But that is overall maturity. And as you will see, the .998 requirements for “procedures” may be fully half of your preparation labor by themselves.
CMMC source material for procedures
In the CMMC Assessment Guide for Level 3, there are seventeen requirements for procedures – one for each cybersecurity domain. They are numbered XX.2.998 where XX refers to the abbreviation for the cybersecurity domain. For example, AC.2.998 is the requirement for procedures for Access Control.
The assessment guide gives the following process description, assessment objectives (note that the assessment objectives all refer to “procedure”), and discussion.
Document the CMMC practices to implement the <CYBERSECURITY DOMAIN> policy.
[a] the procedures to implement the practices are documented and followed to implement the policy for the <CYBERSECURITY DOMAIN>;
[b] the procedures specify the activities required to carry out the <CYBERSECURITY DOMAIN> policy; and
[c] procedures are reviewed and updated periodically to ensure they meet <CYBERSECURITY DOMAIN> policy.
Documented practices improve an organization’s level of confidence in the ability of responsible individuals to execute the practice in a repeatable manner. Organizations mature their practices first by documenting them, then by performing them as documented, in other words, “Say what you do; do what you say.”
A procedure is defined as a specified way of carrying out an activity or process. Documenting procedures outlines the activities involved in satisfying the practice. The format of a documented practice can vary, from a handwritten desk procedure to a formal organizational standard operating procedure that is managed and controlled.”
CMMC Assessment Guide for Level 3, version 1.10, published by Department of Defense.
What do the authors of the CMMC model say about Procedures?
Carnegie Mellon University’s Software Engineering Institute (SEI) and Johns Hopkins’ Advanced Physics Lab (APL) worked with the Department of Defense to author the CMMC model. The SEI has published a few blogs and webinars to give some further explanation about the CMMC model.
SEI Podcast Series “Documenting Process for CMMC” released July 2020
Source: https://resources.sei.cmu.edu/library/asset-view.cfm?assetid=644419
Summary notes (my notes and interpretations, watch the video for the exact explanation used):
- The .998 requires that all practices are documented up to the level you are certifying to.
- The goal is for each activity to be repeatable, which builds the foundation for continuous improvement.
- The level of detail of the documented practices can and will vary from organization to organization. Some small organizations will use handwritten desk procedures, while larger organizations may have formal Standard Operating Procedures (SOPs). The choice between them is up to the organization – depending on what is best for them.
- So if you have a small company, can you have simple procedures? Yes. As long as the documented procedures define the practice in such a way that the activities are repeatable, then that would work. We would expect the complexity of the documentation to grow as the organization grows. A smaller organization would have very simple documentation while a Fortune 500 company would have managed SOPs that are used throughout the enterprise.
- So do I need to document ALL the CMMC practices? Yes – up to the level being assessed.
- How you document procedures will vary. Some organizations might use an “IT Security Policy” and document them there, while others might document them in the System Security Plan, while other organizations have very specific SOPs for each individual topic.
- Do we need to write to the book – organize the documents for each cybersecurity domain? No – the organization of your documents should be in a way that is most effective for your company.
- What about updating practices? There isn’t a “real defined requirement in the CMMC to update them”, but if the process is being followed, it should naturally be updated over time as improvements are identified.
- The assessors should verify that the procedures are being used by the organization, not just that they exist.
How do people interpret the .998s?
The typical interpretation: “What?”
As I mentioned before, almost every company I’ve reviewed for CMMC readiness is completely unprepared for the .998s – they haven’t even been on the agenda so far. So the typical interpretation is “what? that was a requirement?”
An example of what this looks like: The assessor is provided a mish-mash set of policies, standards, training, and procedures which are written to address the 800-171 requirements that specifically require documentation, such as a publication review procedure. Documentation of other practices, especially ones that are performed once, like verifying that a new product has been FIPS 140-2 validated, are completely absent.
The adept response: “List things to be done”
The more adept response (from CMMC-focused senior cybersecurity specialists) tends to be: “I’ll re-state each of the CMMC practice requirements in our company documentation.”
An example of what this looks like: The assessor is provided policies, procedures, and checklists which have somewhat vague but actionable statements addressing each CMMC practice. “All personnel shall receive annual insider threat training which describes indicators of compromise.” and “Verify system has account lockout thresholds set for no more than 5 failed logon attempts.” In cases where an activity is repeated often over time (such as checking logs for malicious activity), then it would have step-by-step instructions.
The hardcore response: “A non-technical person can follow this procedure”
The last option is the surefire one, but also the hardest to accomplish: Have step-by-step procedures which address every single assessment objective within the CMMC.
An example of what this looks like:
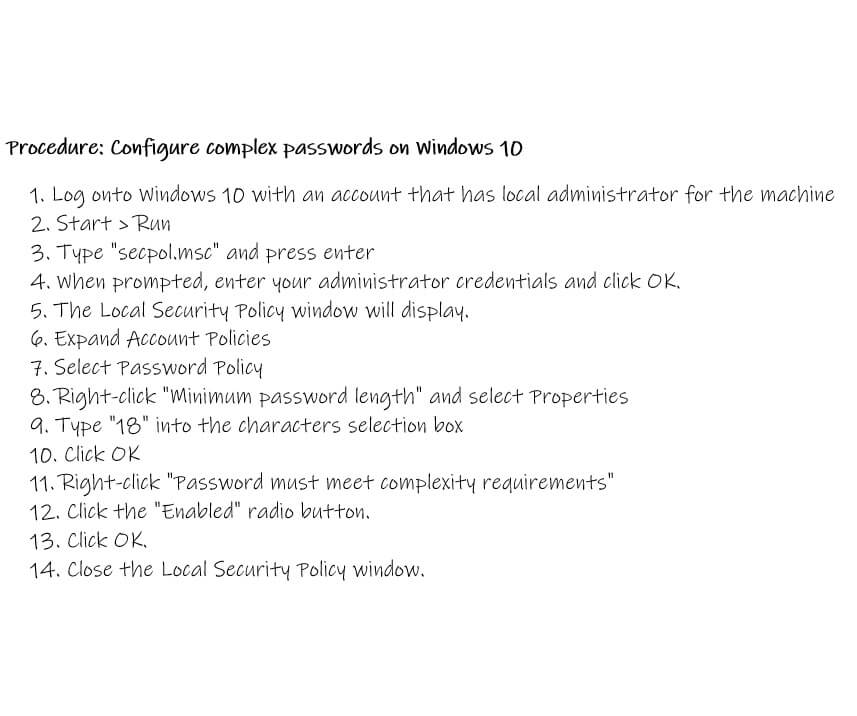
Procedure: Configure complex passwords on Windows 10
- Log onto Windows 10 with an account that has local administrator for the machine
- Start > Run
- Type “secpol.msc” and press enter
- When prompted, enter your administrator credentials and click OK.
- The Local Security Policy window will display.
- Expand Account Policies
- Select Password Policy
- Right-click “Minimum password length” and select Properties
- Type “18” into the characters selection box
- Click OK
- Right-click “Password must meet complexity requirements”
- Click the “Enabled” radio button.
- Click OK.
- Close the Local Security Policy window.
This would be repeated for each other type of system, such as Windows Server, each cloud vendor, your firewall, your switches, your Linux servers, Macbooks… you get the idea. Just this one requirement could result in several pages worth of procedures that need to be maintained over time.
An alternate possibility is to search out Knowledge Base articles for each vendor and capture links to them. References may take less time to set up initially, but won’t be customizable for your environment, and certainly won’t cooperate with continual improvement efforts.
What level of procedure documentation has worked?
At the time of this writing, only two companies have passed a CMMC Level 3 assessment: Redspin and Kratos – both were required to get an assessment in order to become an Authorized CMMC Assessment Organization.
Kratos has been quiet about their assessment experience, but Redspin has published a series of webinars discussing their CMMC journey. Their most recent Lessons Learned video has some information relevant to this discussion.
Here are my notes from the webinar (starting at timestamp 6:00):
- What does a completed set of policies and procedures mean? In each policy, you have identified roles and responsibilities and they flow down to the procedures.
- Redspin’s CISO Thomas Graham describes not only having control statements such as “as an organization we are going to require multi-factor authentication on all of our logons”, but going a step further with “functional level procedures which show how it is enabled and enforced for any new user that we bring on as well as current users”.
- Tony Buenger said that the procedures need to be detailed enough that they show the step-by-step tasks to accomplish the end result. And that you can hand the procedures to a colleague (who doesn’t normally perform the activity) and have them accomplish the activity.
- Thomas Graham recommended having your CEO attempt to follow the procedures. If they can perform the procedures, then it shows that the procedures are detailed enough.
The bottom line: What will pass an assessment?
If you listen to SEI, they make it sound like the procedure documentation can be much easier based on the size of the company. “Hand-written desk procedure” versus formal “Standard Operating Procedure”.
There is a problem with this expectation: a hand written desk procedure may need 20+ steps just like a SOP may need 20+ steps. The only real difference is that one has a header, footer, and fancy title with version control. If a company needs to write extremely detailed step-by-step procedures for each system and requirement, the amount of effort is almost exactly the same between a handwritten procedure and a formal procedure.
This “handwritten desk procedure” took almost the same amount of effort to write as a formal SOP would….
I wonder if SEI anticipated that the .998 requirements could be interpreted to be so involved.
The CMMC assessment guide does not say “step by step” in it (reference the “Sources” topic above). But procedures are generally understood to be something that is followed in order.
Bottom line: I don’t know what the perfect answer is. The most extreme answer is the safest, in terms of passing an assessment. The most extreme answer is also the precedent for CMMC, since it worked for Redspin.
I personally don’t think having every CMMC Level 2+ company write and maintain books of procedure is the best use of our defense economy’s dollars and cybersecurity labor. Is it really a value add to document a step by step procedure for how to assign a temporary password to a user and have them change it for every system you use? Or should you go the middle route, hire a halfway skilled helpdesk person, put in your policy that it is important to do this, and then follow up to make sure it happens?
It may be the case that this question is answered during Provisional Assessor training, or in the curriculum for CMMC Certified Assessors. But that information is not public and is not available for organizations preparing for certification unless they have access to a Provisional Assessor. This seems like an important enough topic that we should ask for more information.
Discussion – what is the right answer?
Do we really need step by step procedures that a non-technical person can follow?
Should procedures be written for things that are configured once and stay good over time, such as enabling multi-factor authentication for your cloud provider? Or only things that are manually and regularly performed, such as a new computer build checklist?
What about requirements that require years of experience and judgement, such as performing a risk assessment – should companies attempt to write a procedure for this? How would that even work? Are you allowed to say “Step 1: Read the book “How to perform a Risk Assessment for CISOs”, Step 2: Perform risk assessment following the book instructions.” ?
What do you think? Please comment!
Please sign up for our newsletter to get notifications about articles and news about CMMC.
V. Amira Armond (CISSP, CISA, PMP, MBA) is a computer systems architect, cyber-security consultant, and owner of the C3PAO candidate Kieri Solutions LLC. She specializes in CMMC preparation and DFARS 252.204-7012 compliance, and designing secure and resilient enterprise systems for private sector and the DoD. She is the chief editor for cmmcaudit.org, a public resource for news and informational articles about the Cybersecurity Maturity Model Certification.
Thank you for your hard work and another great topic.
What is the goal. The goal of the maturity model is to a clear expectation (policy) from a accountable stakeholder that address the security control. Then there needs to be a behavior (procedure) which aligns to that policy.
Also if the role has some level of expectation on competency then you don’t need to have it as a lower level. You need to be able to show it is consistent when repeated.
Procedures do, indeed, need to be detailed enough so that if the person performing them suddenly left, then another could step in and perform the procedure without prior knowledge about how to do the task. Having said that, there are nuances and automation advantages that can take much of the grunt work out of even writing the procedures. What I mean by this is best illustrated by an example. Take that handwritten procedure for implementing a good password hygiene for WIndows 10. That is an excellent procedure, it is well formed, and will pass an assessment. So is one that looks like this:
1. Login using a local administrator account
2. go to [insert file share here]
3. double click [filename].reg
In doing it this way, not only would you be documenting the proper steps to follow for implementing the password complexity requirements, but you could pack a TON of other common system configurations into that .reg file and satisfy multiple CMMC/171 controls and reuse the same procedure for all of them.
Our philosophy, as informed by our ISO 27001 certification experience, is to create procedure documentation that could be following by a new hire that has a responsibility to complete that procedure. So depending on the technical nature of the procedure, the instructions could be very detailed. And, of course, we have a requirement to review all our documentation yearly.
Great post.
I think about in terms of the science fair project (or a massive university research project) the procedures are written in a way that allow someone to get the same results every time (though we suffer from replicability study shortage
I would suggest that you include a change to document the periodic updating of your procedures.
Comes in handy as evidence for your .997
The other thing to note is DIBCAC has said that the mixing up of policy, procedures and plans has been a stumbling block for C3PAOs.
They do not get past the document review.