Author: V. Amira Armond (CISSP, CISA, PMP, MBA) is a computer systems architect, cyber-security consultant, and owner of Kieri Solutions LLC (a C3PAO applicant).
Regan Edens is the Chairman of the CMMC-AB Standards Management Committee and is the founder of DTC Global.
Hello all,
There has been a lot of confusion across the Defense Industrial Base (DIB, AKA Defense Contractors) about whether clouds will be included in CMMC assessments. This is because the CMMC model does not mention clouds at all. Cloud requirements are only described in the previously-existing DFARS clause 252.204-7012.
As a result, contractors getting ready for CMMC have the following questions:
- Will the requirement in DFARS 252.204-7012 (paragraph D, regarding cloud providers) exist after CMMC is rolled out?
- Are clouds in-scope during a CMMC assessment?
- Will CMMC and FedRAMP have reciprocity?
- How do we decide if a cloud is “FedRAMP moderate equivalent”?
- What is the difference between DFARS 7012 compliant and FedRAMP Moderate?
- If we use a compliant cloud, can we just mark all security requirements related to that cloud “Not Applicable”, or just say “it is FedRAMP authorized” during an assessment?
Please note: This conversation applies to CMMC Level 3 and above. While some parts of the conversation are relevant to CMMC Level 1 and 2, many parts do not. If you do not handle Controlled Unclassified Information, most of this interview should not affect you.
Interview with Regan Edens (CMMC-AB) and Amira Armond (CMMCaudit.org)
Regan Edens (Chairman of the CMMC Accreditation Body (CMMC-AB) Standards Management Committee) stepped up to provide clarification on how CMMC interacts with cloud requirements and DFARS 252.204-7012. He also addressed the CMMC-AB’s responsibility to roll out CMMC to the private sector, which means that the CMMC-AB is authorized to explain and clarify these topics.
This interview was recorded on December 18, 2020. Thanks to Regan Edens and the CMMC-AB for this information!
Below the video will be summarized questions and answers, and links to documents that were referenced during the conversation. There are also very important references from the DFARS Cyber FAQ document at the end of this article.
DoD guidance referenced during the interview
DFARS 252.204-7012 (and related clauses)
Summarized Q&A from interview
Disclaimer: The below Questions and Answers text is summarized by me (Amira Armond) so that you don’t have to watch the entire interview if you don’t have time. If anything is misquoted it is entirely my fault and not reflective on the CMMC-AB. Please watch the video for the authoritative version.
Is DFARS 252.204-7012 even going to exist when CMMC rolls out?
Amira: The DFARS clause 252.204-7012 Paragraph D is where the requirements for use of cloud providers is discussed. Is DFARS 252.204-7012 even going to exist when CMMC rolls out?
Regan: Absolutely. 7012, 7019, 7020, and 7021 co-exist. They are not independent. 7021 does not replicate the requirements in 7012. If 7021 looked very similar to 7012 with what it addresses, I would think that 7021 could stand alone, but it doesn’t.
The 7012 clause requires the contractor to provide “adequate security”, which is cited specifically in 32 Code of Federal Regulations part 2002. This document provides the foundation of the program originally described in the Executive Order [for protection of CUI] by President Obama which gives requirements for DIB to handle CUI, establishes the CUI registry, and gives authority to NARA. This [32 CFR 2002] references the 800-171 requirements.
[Amira: The DoD Acquisitions DFARS Cyber FAQ includes cloud evaluation as part of 800-171 assessment – see Q127.]
Regan: I’m not as familiar with how the [DFARS Rule] process works. I’m not sure if it is possible to take an old clause and a new clause and combine them later, or if you need to keep them separate.
Will clouds be evaluated as part of CMMC certification?
Amira: Will evaluating DFARS 7012 compliance [specifically Paragraph D for clouds] be part of the CMMC [level 3] assessment process? Is there proof that cloud compliance to 7012 will be part of assessments (such as the CMMC provisional assessments)?
Regan: Yes, because the DFARS 7021 clause as written can’t stand alone, we have to account for the DFARS 7012, 7019, 7020, and 7021 clauses together. These require access for outside assessors, recording results in SPRS.
Amira: Excellent, I think that means that FedRAMP is still on the table. Regarding your quote “OSC’s that use those cloud service products that contain CUI, could only do so with GCCHigh or with another CSP/Cloud SaaS tool in DISA Level 4 or Higher environment…” I’m not really familiar with DISA Level 4…
Regan: OK, to clarify, because I don’t want to confuse people: DISA Level 4 is equivalent to FedRAMP Moderate. DISA Level 5 is equivalent to FedRAMP High. What this means is that FedRAMP Moderate is important for Cloud Service Providers (CSPs), because they need to meet the requirements. The number one concern we have for [defense contractors using CSPs] is “Do they know that? … Do external service providers know that they need to meet these requirements? Many of them don’t.”
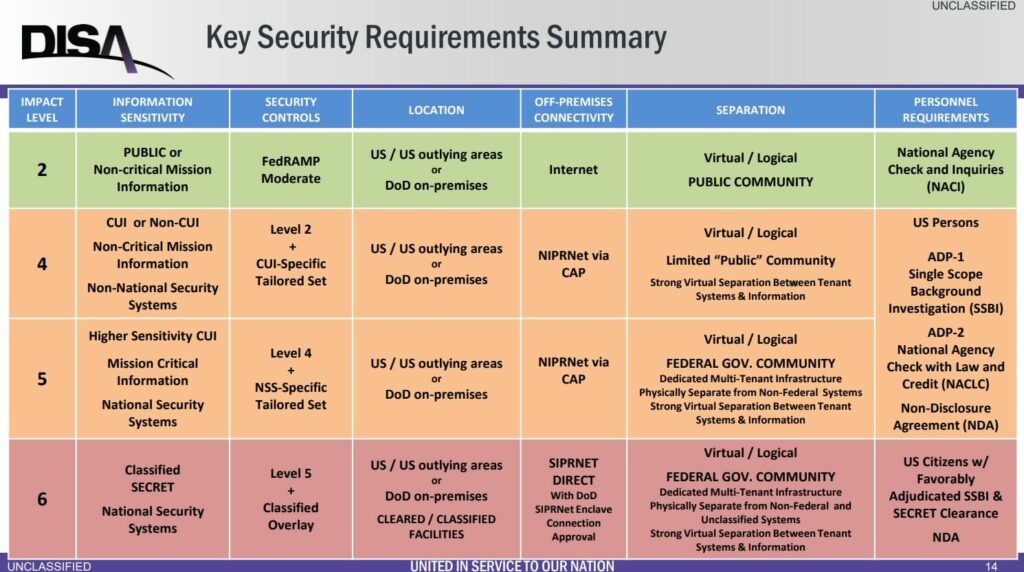
Clarification: This is the impact level summary table for cloud providers. From Cloud Computing Security Requirements Guide, released May 2018. Author = Ron Rice, DISA Cyber Standards Branch.
Amira: This is a big topic for me. I do regular training that cloud providers meeting FedRAMP Moderate is nice, but there are those requirements for incident reporting and forensics access in DFARS 7012. There is no central database that lists those cloud vendors who are FedRAMP authorized AND perform the additional requirements in 7012 paragraph D, so we have to ask the vendor and get their answer.
Regan: Right, because they are required to be FedRAMP Moderate AND meet the requirements under DFARS 7012 [paragraph D].
FedRAMP does not cover all CMMC Level 3 requirements by itself
Regan: So now [the defense contractor] has FedRAMP moderate clouds, and is working on their POAM. When it is time for the CMMC certification, your POAM needs to be 100% complete. When we are talking about reciprocity between CMMC and FedRAMP, there are significant differences between CMMC Level 3 and FedRAMP moderate.
Amira: You are getting to the point of my concern. I’ve heard in a few cases that the cloud provider, the external service provider, the MSP, the MSSP, all need to be CMMC Level 3. For the cloud providers, there are new requirements added by CMMC that do not exist in FedRAMP. When we use these providers, how do we prove that they are CMMC compliant? Does the cloud provider need to get an assessment of just the differential practices? Do I need to drag in a cloud provider employee to discuss their security during my company’s assessment?
Regan: Let’s parse this out because it is important. So regarding CSPs, or external service providers (such as a datacenter), that has CUI. Do they meet requirements? The answer is – Unless the external service provider meets the DFARS 7012 requirements right now (they should have been meeting these requirements for three years, because this is what DFARS 7012 says), and for FCI, there is a subcontractor requirement for protection of FCI when you share it with other parties…. when a cloud system is contaminated with CUI [because customers have put it on the system], this system needs to meet FedRAMP Moderate or equivalent requirements. This is non-negotiable. Another non-negotiable item is that your SLA or contract with the cloud vendor needs to say that they are willing to meet the requirements [described in DFARS 7012]. The records also need to give enough evidence to convince the assessor that you believe that [your company and the cloud provider] are meeting security requirements and that the confidentiality of CUI is protected.
For some, there is a chicken and egg problem. If a small company is using a big company as a vendor, and the big company isn’t paying attention to these requirements, the small company will probably need to stop using that big company as a vendor unless the big company comes back and provides enough documentation to show that they are meeting the requirements.
Shared responsibilities
Regan: Oh by the way, the cloud provider will be saying that the client needs to meet shared responsibilities in the relationship. There is a point where the cloud provider’s responsibilities end and the client’s responsibilities begin.
Amira: I have to say, this is something that drives me crazy. There are so many companies out there that put their solutions on AWS GovCloud but don’t follow basic security (such as access control, no firewalls) within their own company. They say they are FedRAMP because their cloud host is FedRAMP, but it isn’t true.
Regan: Totally agree. There is no magic certificate you can put on your wall that because your cloud host is FedRAMP, that means your product or solution is FedRAMP too. You need to understand the shared responsibilities and identify which are performed by the cloud host and which are performed by the client.
Proving that your cloud provider meets CMMC requirements
Amira: OK, so let’s move forward to when you are actually getting assessed. The DCMA is standing in your office saying “Prove to me that your cloud meets the requirements”. In other assessment methodologies [such as SOC-2], for external companies, you would trust the assessment reports issued by other assessors, or you would send your own assessors to go onsite and audit that company. You don’t just trust the external company when they say that they are compliant. Is that something that defense contractors will need to do with cloud providers to bridge this gap [between FedRAMP controls and CMMC practices], or will we be able to trust a cloud provider’s documentation on what they do or don’t do?
Regan: Because there is a legal liability related to the presentation of document stating that they do something, the risk to companies [for false advertising] is much greater than simply telling the truth and saying their product doesn’t do it. So while it is possible that documentation could misrepresent the reality, in my opinion that [the majority of vendors will tell the truth].
The ratio of CUI throughout the DIB is [triangle shaped, with the narrow point at the top]. The amount of CUI held is greatest at the low levels. Because of this, it doesn’t make sense to force all defense contractors [potentially over a million organizations involved] to individually pull in their cloud providers to assist during an assessment. I believe that the [external providers] with a responsibility to produce that documentation will do so with vigilance due to the risk involved in getting it wrong.
Amira: This makes sense. I think it is a judgement call on your [the CMMC-AB’s] side to determine the depth of the assessment and how it is run. For example, FIPS. We [defense contractors] are already using vendor documentation to identify the products and modules that are used for FIPS cryptography, and follow that down [to the specific certificates]. We aren’t assessing whether the vendor is telling the truth about what modules are used within their products.
Regan: The relationship between the CSP [and the client] is the CSP is hosting the client within their [secure] environment. But that doesn’t mean that the client is meeting requirements.
Amira: The Cloud Shared Responsibility Model.
Regan: The DIB contractor needs to ensure that when their CUI is in a cloud environment, that it is FedRAMP Moderate or equivalent, and that there is reasonable expectation that the CSP documentation is coming, or that the contractor is confident that the cloud provider is actually doing what they need to do. The DIB contractor will need to make the choice of changing vendors if they can’t confirm this. It is better to do this earlier if you need to do this. It is better to ask that question now rather than ask it right before an assessment and [be in emergency mode re-architecting your business] because of the incongruence of that relationship.
Does the CMMC-AB have authority to make these clarifications?
Amira: This is great information, but are you allowed to give it? Does the CMMC-AB have the authority to make these clarifications?
Regan: This is a difficult question to answer, so I’ll start with qualifications.
- Everything I say can be changed in the drop of a hat because a decision or policy could be created which gives written guidance and direction which is consistent with what the DoD chooses. This is the DoD’s program, it is their regulation, and ultimately it is their responsiblity to understand and accept the risk of any decision that they make.
- The CMMC-AB’s role is to support the DoD and implement the ability to execute and manage these capabilities across the DIB. There is very little written guidance in the vast majority of these topics. The majority of written guidance is squarely in the DFARS Cyber FAQ in the procurement toolbox. I encourage everyone to read those questions and understand the recent updates. Those updates are an authoritative source.
Amira: They pull the DFARS 7012 requirements into the 800-171, yes.
Regan: That’s right. So everything that it [the DFARS Cyber FAQ] says is the authoritative source for everything I’ve said. On the human side, in my role as Chairman of the Standards Committee, we need to bring clarity and consistency, ” to bring consumability” to the standards. My job is to bring clarity, based on authoritative resources and my exchange of information with the DoD, to topics that have an absence of guidance.
So you ask “do you have the authority?” – that is part of our mission, to provide clarity, consistency, and consumability. But the authority ends with the fact that we are literally building this in flight and at the end of the day, a subtle change of a word or series of words, or an update to the FAQ, could [invalidate] anything I say. And that is certainly the DoD’s purview. And I would say that it a bonus. It shouldn’t be about what someone said, but what was written. My preference is always to defer to written guidance.
The AB and our committees are working with industry (such as cloud vendors, other organizations) to give them guidance when there is a lack. Then we take the feedback they provide us and continue the conversation with the DoD Acquisition office. This is a difficult path to walk.
The stakes haven’t been as high with just DFARS 7012, but now they are. Especially with [the recent] Solarwinds incident affecting national security. So as enforcement increases, the stakes are higher, and people dive from very general topics to specific details. The ecosystem still needs to mature and we still need to grind out consistency and definitions and clarity and guidance. Where we are now, we do need to start stepping up, begin the dialogue, engage the DIB, and talk about what we do know. And what we do know is a lot more than what we don’t know.
So I think that the areas of uncertainty within the DoD policy, that may change, are fine and good. I always encourage the DIB and industries that are in support of the DIB, to focus on what they know. We know 800-171 and the requirements associated with that: the DFARS 7012 and the DFARS Cyber FAQ. And the vast majority of that will apply to CMMC.
Follow-up, additional DFARS Cyber FAQ References
Regan nominated these DFARS Cyber FAQ questions and answers as relevant to the conversation. They are quoted below.
Topic: Contractor using cloud solution to store covered defense information (DFARS provision 252.204-7008 and DFARS clause 252.204-7012 apply)
Q110: How can a contractor ensure that the cloud service provider can comply with requirements for cyber incident reporting, malicious software, media preservation and protection, access to additional information and equipment necessary for forensic analysis, and cyber incident damage assessment (i.e., paragraphs (c) through (g) of DFARS clause 252.204-7012?
A110: While the (c)-(g) requirements are contractual requirements you must meet (e.g., reporting of cyber incidents), if you are using a cloud service, you’ll need to insure the cloud service provides you the necessary information/support to meet those requirements (e.g., report a cyber incident affecting your DoD CUI to you in a timely manner, so you can report the cyber incident to DoD within 72 hours of discovery). Each provider approaches these differently, with some providers explicitly stating they support the requirements (or not) while others may note that the customer can supplement their services to meet the requirements.
Q113: Can you clarify what is meant by ‘equivalent’ to FedRAMP, so that companies will know what cloud services they can use and the relationship to NIST 800-171 in order to assess what the cloud service provides and what the company may need to furnish to meet the required cybersecurity controls.
A113: The DFARS clause 252.204-7012 (b)(2)(ii)(D) states that “the Contractor shall require and ensure that the cloud service provider meets security requirements equivalent to those established by the Government for the Federal Risk and Authorization Management Program (FedRAMP) Moderate baseline (https://www.fedramp.gov/resources/documents/).” This does not preclude nor require the contractor use a CSP service authorized/approved by the FedRAMP program – since in some instances such FedRAMP approved services may only allow use by government agencies – but simply requires that the contractor ensure that the cloud services contracted to process and store covered defense information meet the same set of requirements.
Q114: Why ‘equivalent to FedRAMP moderate’? Why is NIST SP 800-171 not sufficient in the case of a cloud service provider?
A114: FedRAMP “Moderate” requirements (rather than NIST SP 800-171) are specified for the following reasons:
-NIST SP 800-171 was not developed to accommodate the additional security requirements necessary to protect information when using an external Cloud Service Provider. The FedRAMP Moderate baseline was developed to include these additional requirements.
-Many of the modifications made to the NIST “Moderate” baseline confidentiality controls in developing NIST SP 800-171 – such as removing automation requirements – to accommodate the broad range in the size/complexity of nonfederal organizations internal IT systems, as well as the elimination of availability requirements, do not apply to external CSPs.
-The FedRAMP Moderate baseline cloud service is well established and offered by multiple CSPs
Q115: The DFARS states “the Contractor shall require and ensure that the cloud service provider meets security requirements equivalent to those established by the Government for the Federal Risk and Authorization Management Program (FedRAMP) Moderate baseline”. If the cloud provider is not FedRAMP certified, how can a contractor ensure that the cloud provider meets security requirements equivalent to FedRAMP Moderate?
A115: The contractor can ensure that the cloud provider meets security requirements equivalent to FedRAMP “Moderate” in the same way the contractor would normally ensure any services or product being contracted for will meet his requirements. In this case, the FedRAMP Moderate baseline is well established and understood by CSPs that provide such service to the USG. A solution would be to use a CSP service approved by FedRAMP at the “Moderate” level. Initially, CSPs were not allowing contractors on FedRAMP authorized systems, since it was a ‘US government’ authorization. So, if co-tenancy with USG users is not possible, it is acceptable to use a similar service that has not formally been approved by FedRAMP, if the CSP can demonstrate to the contractor that it is equivalent. However, this has not recently been an issue.
However, even as the number of FedRAMP offerings has increased, there are situations where some FedRAMP moderate offerings may be acceptable in some circumstances, but not in others.
Per DFARS clause 252.204-7012(b)(3), companies need to apply other information security measures, if required. When using external cloud services, FedRAMP moderate generally addresses the security requirements of information categorized as CUI Basic and most CUI Specified. However, some types of CUI/covered defense information have additional requirements that have to be addressed. For example, some data such as export control/ITAR information may require the data be processed and stored in the US and be administered by US persons. This may dictate what type of FedRAMP moderate cloud service can be used, as most FedRAMP ‘commercial’ services do not insure data is stored/processed in the US and by US persons. For this reason, a vendor may say a ‘Government’ version or service is required – it depends on whether the CUI/covered defense information has specific processing/storage requirements.
Note that some cloud providers will only ensure complete US sovereignty (e.g., all services are US-based and administered, even if the user is operating outside the US) with their FedRAMP ‘High’ offerings. Since FedRAMP High is not required to protect CUI in accordance with DFARS 252.204-7012 (such offerings are a by-product of DoD Cloud Security Requirements Guide Security Level 4 services made available to non-DoD users), companies should determine whether their particular situation requires use of a providers FedRAMP ‘High’ services to meet any US data sovereignty requirements.
Q116: If a company is using an external Cloud Service Provider (CSP) to provide processing and storage of covered defense information, (i.e., DFARS clause 252.204-7012 requires that the CSP meet requirements equivalent of to the FedRAMP Moderate baseline), depending on the service provided (i.e., IaaS, PaaS or SaaS), some of these FedRAMP requirements are allocated to the client. In this case, does the client (the company contracting with the CSP) have to meet FedRAMP “Moderate” requirements that are NOT mapped to the NIST SP 800-171 requirements per Appendix D of NIST SP 800-171?
A116: No. The CSP has to meet all of the requirements equivalent to the FedRAMP Moderate Baseline, but if some of these (as is typical) are allocated to the client, the client does not need to meet FedRAMP requirements that are unrelated to the NIST SP 800-171 requirements. If the particular FedRAMP requirement (a control from NIST SP 800-53, Security and Privacy Controls for Federal Information Systems and Organizations) is not mapped to a NIST SP 800-171 requirement in Appendix D of NIST SP 800-171, it need not be applied by the client. When the FedRAMP control is mapped to a NIST SP 800-171 requirement, only the actual NIST SP 800-171 requirement need be implemented, which may be somewhat different than its mapped NIST 800-53 control. Note that in some circumstance controls that must be implemented by the CSP may require a reciprocal implementation by the client for the CSP’s control to be effective.
Q117: Is the contractor required to flow down DFARS clause 252.704-7012 when utilizing a cloud service provider? Is the contractor responsible for ensuring that cloud service providers comply with DFARS clause 252.204-7012?
A117: When a contractor uses an external cloud service provider to store, process or transmit any covered defense information for the contract, DFARS clause 252.204-7012 (b)(2)(ii)(D) applies. If the cloud service provider is considered a subcontractor for this contract effort and will be handling covered defense information, then DFARS clause 252.204-7012 would flow down, but this would not be typical. While the flow-down provision in 252.204-7012 does not apply if the CSP is not considered a subcontractor, the prime contractor is responsible to ensure that the CSP meets the requirements at 252.204-7012 (b)(2)(ii)(D).
Thank you for watching and reading!
I hope this interview and the notes help provide clarity and get your organization moving on the right path for CMMC Level 3 compliance.
Send me a connection on LinkedIn, sign up for our newsletter, and share this site with others! Please comment if you know more, or submit an article with an in-depth analysis on a topic.
Thanks again to the CMMC-AB for authorizing this interview and helping the ecosystem stay on track.
-Amira
V. Amira Armond (CISSP, CISA, PMP, MBA) is a computer systems architect, cyber-security consultant, and owner of Kieri Solutions LLC.
Kieri Solutions LLC is in progress to become a CMMC assessment organization and has several Registered Practitioners and Certified Assessor candidates on staff. Amira is also the chief editor for cmmcaudit.org, a public resource for news and informational articles about the Cybersecurity Maturity Model Certification.

I had an interesting conversation today with a cloud backup Service Provider about this exact issue. I watched and read your article this morning so it gave me a primer for my meeting this morning. The end result is, they have some business decisions to make as to whether go down the complete path. When Mr. Regan explained about the FEDRamp requirements in the DFARS 252.204-7012, 7020, 7021, and others, and then once the CMMC requirements are applied they will have to be CMMC-AB Level 3 Certified if the data contains CUI.
The end result wasn’t very promising but at least there is the conversation about it.
As both you and Mr. Regan said, there are going to be some hard business decisions to be made. This particular cloud backup service provider is not a small company. If they don’t make the grade it will affect a lot of small to mid-size DoD contractors.
So to sum up, a Cloud Service Provider who already provides a FedRAMP Moderate Service, needs to put the delta of controls in place on their boundary that is currently storing, processing and transmitting CUI in the cloud?
What about a CSP’s enterprise? The issue is scoping the boundary, especially when the prime contractor nor the government Agency never labels every e-mail, document, or file as CUI.
Regan: OK, to clarify, because I don’t want to confuse people: DISA Level 4 is equivalent to FedRAMP Moderate. DISA Level 5 is equivalent to FedRAMP High. What this means is that FedRAMP Moderate is important for Cloud Service Providers (CSPs), because they need to meet the requirements. The number one concern we have for [defense contractors using CSPs] is “Do they know that? … Do external service providers know that they need to meet these requirements? Many of them don’t.”
On this section above, you are LITERALLY confusing people. DISA sees reciprocity with Impact Level 2 with FedRAMP Moderate. IL4/5 are uplifts from FedRAMP Moderate. DISA can grant a reciprocity to IL4 from FedRAMP High upon review. There is a delta of controls on all cases except MOD –> IL2.