Author: V. Amira Armond (CISSP, CISA, PMP, MBA) is a computer systems architect, cyber-security consultant, and owner of Kieri Solutions LLC.
Kieri Solutions LLC is in progress to become a CMMC assessment organization and has several Registered Practitioners and Certified Assessor candidates on staff. Amira is also the chief editor for cmmcaudit.org, a public resource for news and informational articles about the Cybersecurity Maturity Model Certification.
This article is an in-depth review of the CMMC Level 2 Requirement RM.2.142 on the topic of vulnerability scanning. I break out frequently asked questions and reference other requirements that are related to vulnerability scanning.
This requirement also applies to current DFARS 252.204-7012 and NIST SP 800-171 organizations that hold CUI. The 800-171 requirement ID is 3.11.2
Throughout this article I’m going to refer to the official source of guidance: the CMMC Model Appendices. You can find this document, and other official CMMC documents on the DoD Acquisition website:
https://www.acq.osd.mil/cmmc/draft.html
Everything else in this article is an opinion, and fallible. Always refer to official guidance for the best answer.
RM.2.142
Scan for vulnerabilities in organizational systems and applications periodically and when new vulnerabilities affecting those systems and applications are identified.
The NIST SP 800-171 DoD Self-Assessment methodology assigns it a value of -5 if unimplemented, which puts it on-par with Multi-Factor Authentication and other high-impact requirements.
This is the only requirement in CMMC level 1-3 that directly requires vulnerability scanning capabilities. However, this requirement has an outsized impact on businesses due to the cost and effort involved in performing periodic vulnerability scans.
Which systems should you scan for vulnerabilities?
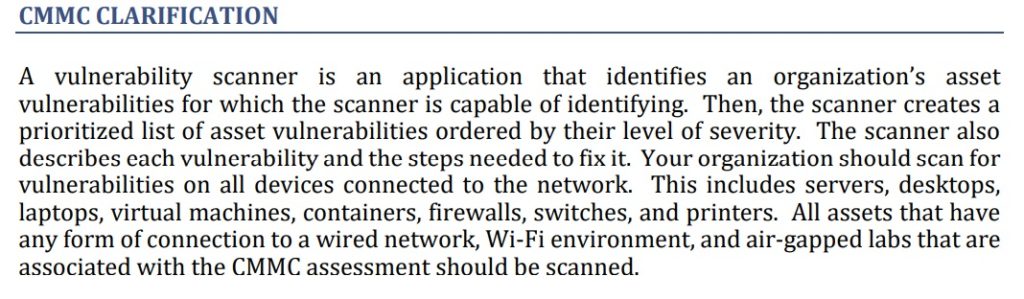
CMMC Appendices version 1.02 released March 18, 2020. Page B-165.
The CMMC Appendix says “Your organization should scan for vulnerabilities on all devices connected to the network. This includes servers, desktops, laptops, virtual machines, containers, firewalls, switches, and printers. All assets that have any form of connection to a wired network, Wi-Fi environment, and air-gapped labs that are associated with the CMMC assessment should be scanned.”
From a practical standpoint, this means you should configure your vulnerability scanner to attempt to connect to every network address that can communicate inside your network. If you have a small network that uses 192.168.1.0 / 24 , then attempt to scan every address between 192.168.1.1 and 192.168.1.253. If you have a large network with several subnets, attempt to scan all the IP ranges within those subnets.
Doing this is helpful because it will ensure you don’t forget less-obvious network devices like switches and printers.
Scanning can identify unauthorized devices or help manage your inventory
Network scanning the entire address range in your network will also help you identify the devices that are communicating on the network, which you might not know about.
In large networks, these scans are vital to control access. ( AC.1.001) Typically an enterprise vulnerability scanner will keep databases of all IP addresses, computer names, and/or MAC addresses that were seen. Many enterprise scanners will let you manage this database as an inventory, tagging discovered devices as authorized or unknown, for example.
What is a CMMC-compliant vulnerability scanner?

CMMC Appendices version 1.02 released March 18, 2020. Page B-166.
The appendix describes enterprise quality vulnerability scanners which keep a database of previous scans and can schedule automated scanning.
What about devices you can’t scan? Remote workers?
The appendix says “You could replicate the critical asset in a test environment and perform vulnerability scans against the replicated asset”. It is unfortunate that the Appendix does not give recommendations for what to do for remote devices that cannot be reached most of the time. ( Both NIST SP 800-171 and CMMC assume an on-premises approach and don’t track current remote-work standards very well).
I can see the potential for using a “representative device” which matches the configuration of remote devices for vulnerability scanning. This is basically what the appendix describes.
Can I use a vulnerability scanner for CA.3.162 “Security assessment of enterprise software that has been developed internally”?

CMMC Appendices version 1.02 released March 18, 2020. Page B-166.
Not a good idea. Vulnerability scanners generally only have definitions for well known COTS products. You could scan the COTS products that your software uses (such as the database system) and it might find vulnerabilities in well-known software libraries installed on the operating system level, but a vulnerability scanner wouldn’t find most problems with internally developed software.
What is the level of effort for vulnerability scanning?

CMMC Appendices version 1.02 released March 18, 2020. Page B-166.
The effort involved in performing vulnerability scans is highly dependent upon…
- The quality of your scanner. Can you set it up and have it just send you reports once a week or once a month? Do you have a cheap scanner that you need to manually set up each time?
- Do you need to scan “representative systems” or can you reach all in-scope systems with your scanner? Maintaining and baselining representative systems is time consuming.
- Initial configuration: You need to get a good quality vulnerability scan, which normally means that you are using “credentialed” scan options. This often means that you need to set up agents or management connections between each device and your scanner.
- Is your vulnerability scanner securable to CMMC level 3 standards? Once you add the vulnerability scanner to your network, now you need to apply all the secure configurations on it too, or justify why you haven’t.
How much do vulnerability scanners cost?
Unfortunately, in my experience, vulnerability scanners are VERY EXPENSIVE, especially on a small scale, and especially for on-premises systems.
There are several cloud based vulnerability scan solutions, but I don’t know of any FedRAMP Moderate / DFARS 252.204-7012 compliant scanning clouds. Some cybersecurity professionals will argue that vulnerability scanning clouds don’t need FedRAMP because they don’t literally store your CUI in the cloud. I have a hard time with this idea because vulnerability scanning agents have (by definition) root access to your systems which do have CUI in them. So that vulnerability scanning cloud could rifle through or export your data if they are compromised. More information (and quote from DCMA on the topic) in this article: CMMC, CUI, and Cloud Vendors – do you need FedRAMP?
I’ve seen a wide range of costs for vulnerability scanners, but none are cheap.
The low end is $2500 per year for a “consultant” license which allows you to load a vulnerability scanner on a laptop and perform ad-hoc scans, typically of a single subnet.
The medium is $10,000 per year for an on-premises solution.
Please comment below with your experiences on vendors and costs! The community really needs some recommendations on this topic.
Community discussion on vulnerability scanning solutions
These recommendations are copied from a LinkedIn discussion in mid December 2020. They might save you a lot of work in your search for a solution. Note: I (Amira Armond) have not verified that they are CMMC level 3 or FedRAMP compliant am not endorsing any of them for this requirement.
Here is the link to the discussion on LinkedIn. Worth reading!
Direct link: Vulnerability scan discussion on LinkedIn
Christopher Goodrich (CISSP, ISSEP, ISSMP, HCISPP) on the topic of whether credentialed scans are expected under this requirement: “Under 171, uncredentialed scans would likely be compliant, but not for CMMC (assuming we are talking about all practices up to and including Level 5. Reasoning: this is a maturity thing. Since it’s essentially no harder to run a credentialed scan, it comes down to the preparedness of the organization. Even at level 3, a credentialed scan may overwhelm the capabilities of the security team in place (lots of other factors here play into this scenario).” “Having said that it is implied by level five and the maturity model that it models itself off of that credentialed scans is the next step in optimization.”
Christopher Goodrich (CISSP, ISSEP, ISSMP, HCISPP) on the topic of whether a “representative system” can be used for vulnerability scanning remote worker laptops: “It also depends upon your configuration management program as well as your implementation of least privilege. If you disallow your workers admin rights on the desktop then you may be able to get by with it. If you implement a hybrid approach and allow users to install software on their machines than no, you can’t get by with it. So a representative machine Will only work if you completely disallow a user the ability to modify the machines base configuration and have defined that configuration.”
Vulnerability scanning solutions (discussion):
Charles Lybrand: Rapid7 InsightVM
James Goepel: “I’ve used OpenVAS in the past as well. It is a good, free tool, although getting it running can be a complex process. Greenbone has kept OpenVAS open source for a number of years. While that doesn’t guarantee that it will stay open source, there is a large enough community that it will likely persist in some form or other. While OpenVAS is very useful, I didn’t find it that intuitive. Small businesses will struggle to configure it on their own. The VM that Hans mentioned helps streamline some of the installation issues, but again, the configuration part can be tough. Nessus is nice too, and has the backing of a pretty significant player in the cybersecurity and ITAM worlds. AT&T AlienVault also has a tool that is built around OpenVAS called OSSIM (https://cybersecurity.att.com/products/ossim). It includes additional capabilities, like a SIEM tool, asset detection, and more. I haven’t played with that enough, but it is on my (very long) list of “to dos”.”
James Goepel: AT&T AlienVault’s OSSIM https://cybersecurity.att.com/products/ossim “It includes additional capabilities, like a SIEM tool, asset detection, and more.”
Hans Ismirnioglou (CISSP-ISSEP): Greenbone / OpenVAS. https://community.greenbone.net/t/setting-up-the-greenbone-security-manager-trial-gsm-trial-virtual-machine/6939
Hans Ismirnioglou (CISSP-ISSEP): “Nessus Essentials could work for a teeny tiny contractor” https://www.tenable.com/products/nessus/nessus-essentials
Saif Rahman: “Have you looked at Qualys Cloud? It’s on the GSA FedRAMP Marketplace (75+ Federal Authorization) and also available on Azure Government IL-4/5 Cloud. Qualys is also available for Azure Virtual Machine workloads on Gov and Commercial. Tenable.io (Cloud Scans and more) is “In-Process” and should be FedRAMP Moderate Authorized in January. We run a MDR on the Azure Government Cloud. All these solutions work for DoD/ACAS.”
Danielle Sims: “Neqter is a SIEM that has packaged OpenVAS into the platform. So if you need a SIEM and vulnerability scanning, check out Neqter. If you just need vulnerability scanning, check out Greenbone’s OpenVAS.”
What is this “credentialed scan” question?
Vulnerability scanners can test a computer for vulnerabilities from the outside-in and/or from the inside-out.
The outside-in scan simulates first-stage attacks that can be performed over a network. Things like man-in-the-middle, weak ciphers, and old versions of network protocols. Only IPs and ports that are open (not firewalled) can be tested in this way. This type of scan does not require any credentials or special permission other than the ability to open network ports to the target. A typical un-credentialed scan of a single workstation might show 1-5 vulnerabilities.
An inside-out scan is far more thorough. The vulnerability scanner establishes a privileged connection (root level) to the target and searches for indicators of vulnerabilities in the file system, programs list, registry, and operating system. For example, the scanner will make a list of all programs and their versions installed on the system, then look for known vulnerabilities that affect those software versions. A typical credentialed scan of a single workstation might show 40+ vulnerabilities.
Pro tip: How can you tell if you set up your credentialed vulnerability scan correctly? Your vulnerability report is huge!
This vulnerability scanning topic is not discussed by the CMMC model, so the answer will probably be up to your organization. An assessor today would probably be forced to go with the lowest bar, which is “there is no requirement for credentialed scans”. This may change as assessments are actually performed and precedents for a successful assessment are identified.
Note: The assessment guide for CMMC Level 3 does say “Vulnerability scanning includes: scanning for patch levels;…[multiple other things]”. Determining patch levels typically requires credentialed scans. The debate continues?
Other CMMC requirements related to vulnerability scanning
RM.2.143 : Remediate vulnerabilities in accordance with risk assessments.
All vulnerability scanners will provide a score that indicates the severity of the vulnerability. You can review this and decide whether the severity is accurate for your organization, as part of your risk assessment process. For example, if your system is air-gapped, you may decide that a vulnerability related to networking is much lower severity than what the vulnerability scanner says.
SI.1.210 : Identify, report, and correct information and information system flaws in a timely manner.
This level 1 requirement doesn’t require the use of vulnerability scanners, but if you use one, it will help your implementation of the “Identify” part of the requirement.
SI.2.214 : Monitor system security alerts and advisories and take action in response.
System security alerts come in many forms. An updated vulnerability database which identifies a new problem during scanning can count as a security alert. (This is one of the best ways to filter through the hundreds of new security alerts each week).
CM.2.064 : Establish and enforce security configuration settings for information technology products employed in organizational systems.
Not all vulnerabilities are fixed by installing a patch. Some vulnerabilities are “features” which are enabled by default for compatibility purposes. Vulnerability scanners can identify configuration problems which are exploitable by attackers. For example, vulnerability scanners would report insecure cipher suites in use on web servers. This is fixed by configuring your operating system to disable those suites.
Thank you for reading. Please comment with your thoughts! This is a community website so please chime in! Reviews of specific vulnerability scanners are desperately needed by the DIB community.
Author: V. Amira Armond (CISSP, CISA, PMP, MBA) is a computer systems architect, cyber-security consultant, and owner of Kieri Solutions LLC.
Kieri Solutions LLC is in progress to become a CMMC assessment organization and has several Registered Practitioners and Certified Assessor candidates on staff. Amira is also the chief editor for cmmcaudit.org, a public resource for news and informational articles about the Cybersecurity Maturity Model Certification.