Editor notes
This article addresses CMMC practice SC.1.175, NIST SP 800-171 requirement 3.13.1, and FAR 52.204-21 – Item 10.
The text of the requirement is “Monitor, control, and protect organizational communications (i.e., information transmitted or received by organizational information systems) at the external boundaries and key internal boundaries of organizational systems.
This article is contributed by Reciprocity Labs. Thank you Reciprocity Labs!
Author: Jordan MacAvoy, VP of Marketing, Reciprocity Labs
What is SC.1.175?
SC.1.175 is a practice under the Systems and Communication Protection (SC) Domain within Level 1 of the Cybersecurity Maturity Model Certification (CMMC). The SC domain is concerned with securing network boundaries and communications. SC.1.175 narrows down the focus to monitoring, controlling, and protecting organizational communications.
According to the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF), boundary components are crucial avenues for protecting organizational communication. The framework, which was established solely for guiding organizations to greater information security, underscores the importance of SC.1.175.
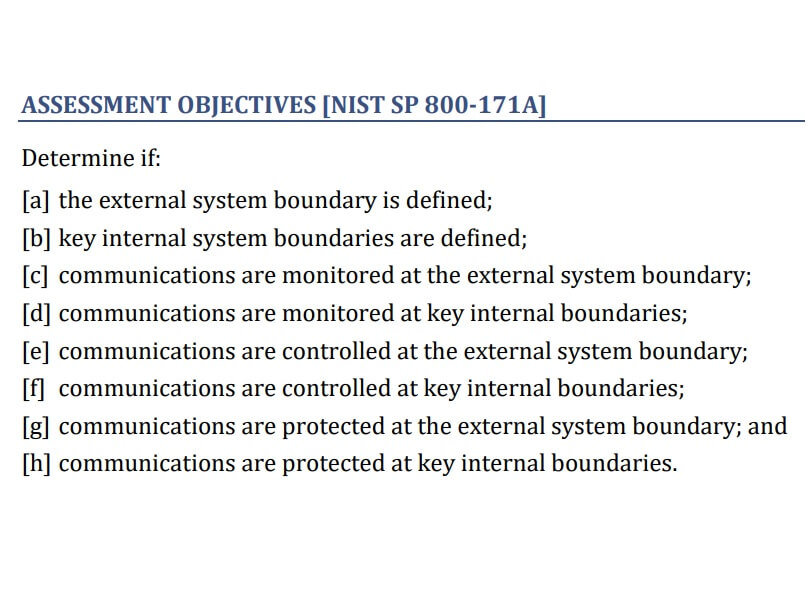
What are the SC.1.175 objectives?
The purpose of this practice is to protect your systems from intrusion. It monitors and controls communication within your network and between your network and others. Below is a breakdown of the four main objectives of SC.1.175
Define Boundaries
Your organization’s communication network has an external boundary that separates it from others such as the internet. It also has internal boundaries separating various levels of communication. Both types of boundaries should be clearly defined.
Monitor Communication
System audit logs and records indicate the communication pathways within the network. The SC.1.175 enforces the review of such documentation. Monitoring communication helps to identify unauthorized access that could pave way for malicious attacks.
Control Communication
Access to your organization’s network should be limited. Conversely, access to certain websites from your organization should be prohibited. Examples of such websites are gambling, adult content, and those with malicious intent.
Protect Communication
Data shared within your network should be protected at all costs. Not all traffic is good traffic; some can result in cyber-attacks. Protecting networks from intrusion is at the core of the SC.1.175 practice. It applies to communication with external networks and within the internal network.
How is SC.1.175 implemented?
CMMC compliance is arrived at after the implementation of each practice. The SC.1.175 is implemented when organizational communication is monitored, controlled, and protected. Implementation is comparable to securing an office; your organization has gates, badges, and key cards to restrict access to the property. Non-employees cannot walk in and out of the office as they please.
The same logic applies to your network. Traffic should not flow freely without verification or means of control. The system has boundaries that must be enforced and protected. How can your organization achieve this? By employing boundary components such as gateways, routers, firewalls, web proxies, malicious code analysis systems, and encrypted tunnels.
The boundaries do not only apply to external access. It is possible to segment the internal network and limit access to specific data. This ensures that only authorized employees can view sensitive information.
Web Proxy
When a user in your network initiates a web request, it goes to a proxy server. The proxy forwards the request on behalf of the user and reverts with a response. The proxy monitors requests and decides which ones to allow. Proxies can mask IP addresses, encrypt data, and filter traffic as per your requirement.
Firewall
A firewall protects your network externally and internally. It controls traffic flowing in and out of the system and protects valuable data in your company’s network. You can also use firewalls to monitor and control access to different parts of the company’s network. For example, you may limit access to specific areas based on employees’ need for access to different information. You may also want to protect sensitive data from malicious or disgruntled employees.
SC.1.175 assessment considerations
To prove compliance, you must assess the efficacy of the practice in your organization. Assessing SC.1.175 requires a review of boundaries and the measures in place to protect organizational communication. Below are potential areas for consideration when assessing compliance. You should check whether:
- You have firewalls, gateways, and/or cloud service boundaries in place to contain and protect regulated data in the system;
- You have routers, internal firewalls, or any other devices that segment the internal network and control the flow of data;
- You have data logs for monitoring the flow of communication;
- Suspicious traffic generates alerts;
- Only authorized connections are allowed beyond boundaries;
- Data flowing in and out of the system boundaries is protected through encryption, tunneling traffic, or other means.
Illustration of SC.1.175 in action
A system administrator at a small organization uses the router to monitor, protect, and control the company’s communication. She puts up a firewall on the router, allowing only traffic from authorized devices to exit the system boundary. She also blocks access to malicious sites, adult content, and gambling websites. She has effectively implemented SC.1.175 and protected her company’s systems from unauthorized access.
Key takeaways
SC.1.175 is a practice that helps organizations to protect their data from malicious attacks. It involves using hardware and software to create a barrier and protect all communication. A company may use firewalls or proxies to prevent unauthorized access. SC.1.175 not only deals with external boundaries but also communication within different internal system components. Adhering to the practice is required for CMMC compliance.
Jordan MacAvoy is the Vice President of Marketing at Reciprocity Labs and manages the company’s go to market strategy and execution. Prior to joining Reciprocity, Mr. MacAvoy served in executive roles at Fundbox, a Forbes Next Billion Dollar Company, and Intuit, via their acquisition of the SaaS marketing and communications solution, Demandforce. He brings to the team nearly two decades of marketing and business development experience helping to grow early-stage, venture-backed companies. Mr. MacAvoy is a graduate of Boston University.
We recommend these articles next:
CMMC Compliance FAQs – Organizations seeking certification