🎵 It’s the most wonderful time of the year 🎵
In the United States, we are entering the holiday season. If you are the CMMC lead for your company, this is a great time to perform all those long detailed compliance tasks that you don’t normally have time for.
Wait. You wanted to take vacation instead? You have a life and family? Hahaha! That isn’t how IT or cybersecurity works! Joking aside, yes we should strive for work-life balance, and none of these compliance tasks are user-impacting, so you can schedule them for anytime.
But if you ARE working over the holidays, this can be a great time to put your head down and get through some uninterrupted compliance work.
Author: Amira Armond, the president of Kieri Solutions – an authorized CMMC Third Party Assessment Organization (C3PAO) providing CMMC assessments, CMMC consulting, and Compliance Documentation packages designed for small/medium business.
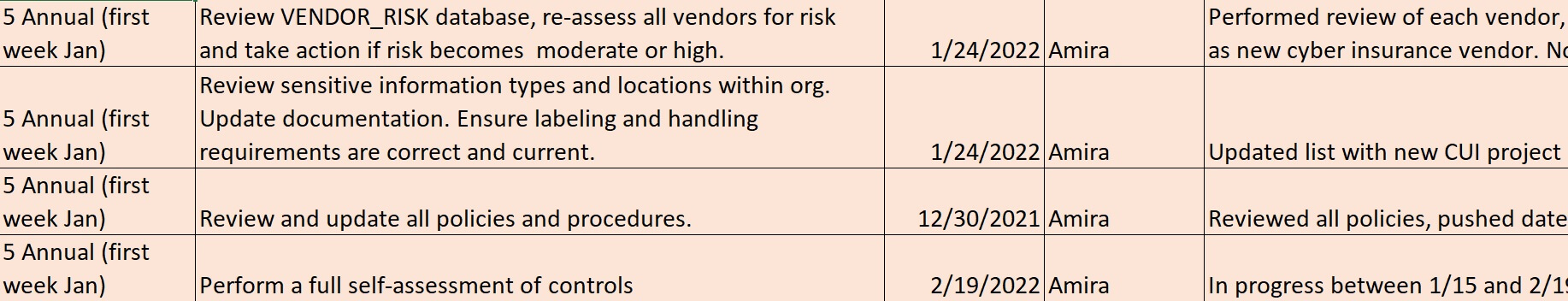
So, which CMMC compliance tasks are ideal for the holiday slow down?
Catalog CUI locations and systems
A smart defense contactor will designate specific locations and systems for sensitive information such as Controlled Unclassified Information (CUI). This should be done ahead of time and communicated firmly to all users.
In my experience, if a company doesn’t get ahead of their users by firmly identifying allowed locations and systems for CUI, the users will figure out their own way. For example, in my company, we have one standard way that we transmit assessment data between ourselves and our clients. Every user is trained on this method as part of onboarding. While mistakes are made, they are typically minor and correctable.
If you don’t proactively control your CUI locations and systems, your users will come up with their own methods to store and share it. This is how a company ends up with unencrypted CUI in their email, WebEx chats, Dropbox, personal OneDrive, and personal Gmail accounts. At that point you’ve got a disaster on your hands and it is really hard to fix.
This task assumes you’ve already got control of your CUI locations and systems. We are just maintaining cybersecurity at this point. Your documentation (such as your System Security Plan or Data Management docs) should include a list of where CUI is allowed to exist. Highly mature organizations will track the type of CUI, the purpose of the CUI in each location, as well as the responsible person for the data.
What could reconciliation look like? You could update this table in your SSP, if you are a small business. Larger businesses may have a separate list where they track their CUI locations and systems.
| Location | CUI Type | Purpose | Responsible Party |
| /Projects/B2 | CTI/EXPT | Part descriptions for B2 bombers | Anne (Aerospace Project Manager) |
| Laptop local storage | Multiple | Local copies of files as they are opened/worked on | Individual laptop owners |
| /Projects/M360 | CTI/EXPT | M60A1 maintenance schematics | Jim (Marines Project Manager) |
| MFR_DB | CTI | Part lists, specifications, and logistics to build products | Frank (database administrator) |
If CUI is found outside the list of locations, it means you need to either update your list or you need to get it cleaned up and sanitized.
How do you find CUI in your environment?
Large companies have access to expensive tools which can automatically search for, catalogue, and control data. If you can afford the tools and staff to operate them, I’ve heard good things about them.
For the smaller companies, searching for strings of likely data should do it. For example, you can search for “controlled by:” or “EXPT” or “distribution statement” to find properly labeled CUI.
Pro Tip
It can be very helpful to provide customized document, email, PowerPoint, and software code templates to your users which contain pre-written labels for the CUI types your company handles. Then if one of your users needs to create a document with CUI in it, they can simply copy the template rather than trying to figure out complex labeling requirements on their own.
Full review of CMMC policies (annual)
Assessors expect your policies to be reviewed and updated at least once a year. That is the official assessor definition of “periodically”.
Ideally, you review your policies line by line and make sure they are still correct for your situation and requirements.
How policies can cause you to fail a CMMC requirement
Failure cause #1: You have documents which contradict each other. If PolicyA says that vulnerability scans must be performed every 15 days, and PolicyB says that vulnerability scans must be performed every 30 days, an assessor is likely to fail the requirement related to defining the frequency of your vulnerability scans, especially if you are following the less secure PolicyB.
Failure cause #2: Your implementation meets CMMC minimum requirements, but your policy says you will be more aggressive. For example, you can pass CMMC with account lock threshold of 10 failed attempts. If one of your systems is set to 7 failed attempts before lock, but your policy says 3, assessors will hold you accountable to your own policy. Note: Formal exceptions to policy will normally help you fix this situation.
As you review your policies, make sure to update the version, date, or revision history (even if you don’t change anything). If you don’t change anything, make a note that you reviewed the policy for accuracy and it is approved as-is. Yeah this is dumb, but assessors want to see a date on your policies within the last year.
Also generate evidence that the policy is still authorized by executive leadership. This can be done in many ways. Having leadership re-sign the latest version. Having the CEO re-upload to an all-hands location. Having the president send an email saying they authorize the policy. Etc.
Review your bigger procedures (annual)
Ideally your company is updating your detailed procedure documents as you use them each day or week or month. You should encourage your staff to update procedures as they perform the procedure. But some procedures don’t get reviewed as often.
The big procedures that often get ignored for updates are your Incident Response procedure (expected by CMMC), your Disaster Recovery Plan (not expected by CMMC but a really good idea), and the miscellaneous back-office procedures for things like how to do maintenance, how to approve new accounts, etc. (expected by CMMC).
Make sure that all of your important procedures have been read-through for accuracy at least once a year. Like policies, it is a good idea to update the versions, dates, or revision history, even if you didn’t make a change.
Re-assess your supply chain (annual)
This topic may be a complete surprise to some folks, because evaluating the security of your supply chain is an “NFO control” – such a basic security measure that the federal government assumes that defense contractors are doing it without an explicit requirement.
As part of our vendor risk program at Kieri Solutions, we review our vendors for trustworthiness and compare that to how badly they could hurt our company if they went rogue.
For example, if our DNS hosting went offline, we would suffer a huge work impact because our clients would not be able to email us. So we review the risk that our DNS host will cooperate with an adversary, go bankrupt, or get taken offline. Is their board of directors, CEO, or their operational staff based out of a country we might go to war with? Does the Department of Defense trust them as a vendor? Was the company recently acquired and their leadership changed? Have they had major outages in the past?
We do this as a formal annual process and track the risk of our vendors. If a vendor starts becoming high risk, our policy is to move away from them.
Full update of your CMMC System Security Plan (annual)
Pull out your System Security Plan and review it from start to finish. Hopefully it is fully up to date (your Change Management workflow includes updating the SSP after making changes, right?), but if not, this is the time to fix it.
Tips for a high quality system security plan
– You should discuss how CUI is transported into, through, and out of your organization.
– You should describe the system environment as though you are explaining it to a brand new IT person. This means at least one paragraph on each of these topics (as applicable): firewall, internet access, facility security, local area network, each cloud you use, desktops, mobile devices, directory, antivirus, email, backups, remote access, supporting services like managed service providers, and audit logging. The descriptions should try to answer common questions that an outsider might have, such as “how is this device protected against malware” or “how do you keep unauthorized people out of your facility?”
– For each CMMC requirement, you talk about (as applicable): Supporting policies (hopefully with the section #), procedures used to implement the practice, where to find records that it is performed over time, who is responsible for doing the requirement, and how it is implemented technically (including where to find the configuration or setting). Ideally, you are making it clear to an outside reader (your assessor) what to examine to see if you are performing each objective.
Pro tip: I’ve never seen a company present a high quality SSP inside a spreadsheet. It is extremely difficult to provide the level of detail necessary within a spreadsheet format. NIST provides a free SSP template in Word format which is a good starting place. The KCD template set (costs money) includes a Word format SSP template which is partially pre-written and has examples for CMMC.
Not sure how to start? This article has training on how to write a quality SSP from scratch.
Perform high-quality CMMC self-assessment (annual)
This last task is the big one. Expect to spend at least a week on it, no matter how small your company.
Before you start, you should have a plan for how you want to assess each objective. Ideally, your SSP identifies each thing you need to examine for evidence and identifies who to interview. The most mature cybersecurity departments will also have written steps to test each objective that makes sense to test (normally assessors don’t test objectives that require you to “define” something). The test should fail if the objective is performed incorrectly.
Example of a test for “authorized users are identified”
Export a list of user accounts from the directory. Randomly select a sample of 10 active accounts which were created in the last year. For each account, verify that an Access Request was submitted and approved by the CISO prior to account creation.
Pro tip: Use an outsider for your self-assessment
It can be very beneficial to pull in an “outsider” for your self assessment. This can still be someone who works for your company, but they should not be intimately familiar with your system security plan, policies, or procedures. Encourage them to validate every sentence in your system security plan. For example, if the SSP says “Our Maintenance Policy, section 4.2, describes the requirement for performing patching on schedule.”, your outsider should actually look up that policy and see if the words in the policy address the literal objective being reviewed. An outsider is much more likely to find problems where you think you addressed an objective, but you actually talked around it, or assumed that a reader would have additional information in their head.
No “partially implemented” allowed
Be realistic in your self-assessment. In a real assessment, you don’t get credit for “partially implemented”. Each requirement is either MET, NOT MET, or NOT APPLICABLE.
You also don’t get credit if you forgot to perform one of the objectives in a requirement. Yes, it is silly to require that you write down your definition of password complexity if you already have your systems configured to require alphabetic, numbers, uppercase, and special characters. However, forgetting to document your “identifies” and “defines” will cause you to fail the entire requirement in a real assessment. Feel the heat now so that when the real assessment occurs, you avoid getting roasted.
Once you complete your self-assessment, date-stamp your assessment results and save them. This is important evidence for your real assessment.
There are a lot more maintenance tasks to do throughout the year. For example, I hope you are reviewing your audit logs for unauthorized activity no matter what month it is! The above list of tasks are the ones that we only perform once a year.
I hope you found this useful!
If you get lonely as you work through these tasks, come join me in the Cooey Center of Excellence and we can commiserate about compliance together.
(Shameless plug) It was easy for me to write this article because these annual tasks and procedures are already part of our Kieri Compliance Documentation. The KCD is designed to be as efficient and plain-language as possible. Battle tested: We used these documents to pass our CMMC assessment (performed by the DoD) as a CMMC Third Party Assessment Organization (C3PAO).
If you are seeking a CMMC documentation package designed for businesses or enclaves with less than 1000 users, ask for a demo!
Author: Amira Armond, the president of Kieri Solutions – an authorized CMMC Third Party Assessment Organization (C3PAO) providing CMMC assessments, CMMC consulting, and Compliance Documentation packages designed for small/medium business.