As promised, the Cybersecurity Maturity Model Certification (CMMC) version 1.0 was released to the public on January 31, 2020.
The document should be stable at this point. Cybersecurity leads for defense contractors need to read through it as soon as possible and begin closing the gaps in their organization’s cyber-security practices.
Links to CMMC v1.0 documents:
Link to CMMC version 1.0 document: https://www.acq.osd.mil/cmmc/docs/CMMC_Model_Main_20200203.pdf
Link to CMMC briefing PDF: https://www.acq.osd.mil/cmmc/docs/CMMC_v1.0_Public_Briefing_20200131_v2.pdf
Link to official website for CMMC Model v1.0: https://www.acq.osd.mil/cmmc/index.html
Early analysis of CMMC version 1.0:
Standard disclaimer: I’m a professional who works in cybersecurity defense and compliance. I’m not a representative of the DoD, CMMC Accreditation Body, or any other official group. This article has my thoughts and opinions, take everything with a grain of salt.
What is the scope of the CMMC?
Scope is discussed, but not fully clarified. “When implementing CMMC, a DIB (Defense Industrial Base, AKA DoD Contractor) contractor can achieve a specific CMMC level for its entire enterprise network or for particular segment(s) or enclave(s), depending upon where the information to be protected is handled and stored.”
This still doesn’t directly address the question of whether the whole organization is audited at a low level when a segment of the organization is audited at a higher level. Example: WidgitsUSA has a segmented network for handling CUI. The segmented network is compliant with Level 3 CMMC. The regular WidgitsUSA network occasionally gets emails from the government with non-CUI information.
Does the regular WidgitsUSA network need to be certified at CMMC level 2 since they get occasional non-CUI emails, such as contract mods? I’m not sure…
Could WidgitsUSA get level 3 CMMC certification just on their segmented network, then go forth and bid on projects of levels 1-3? It sounds like yes.
It looks like the answers will need to be given by the CMMC Accreditation Body.
Maturity level is part of each control
Maturity is the term of the day.
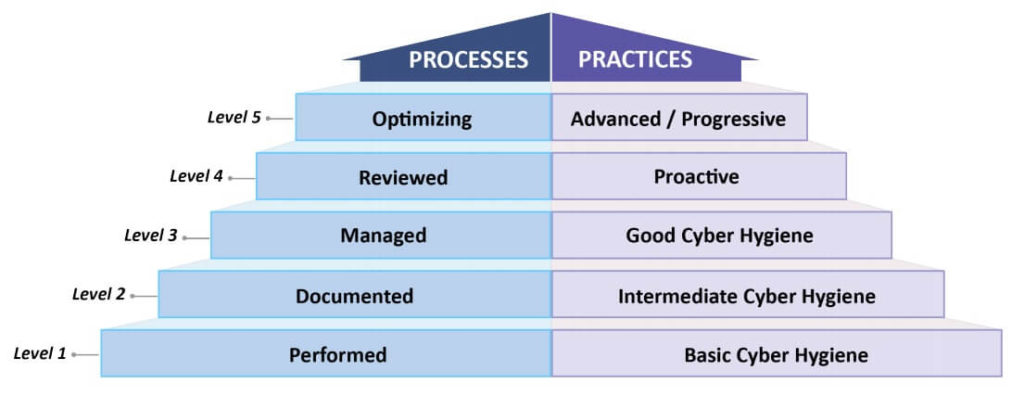
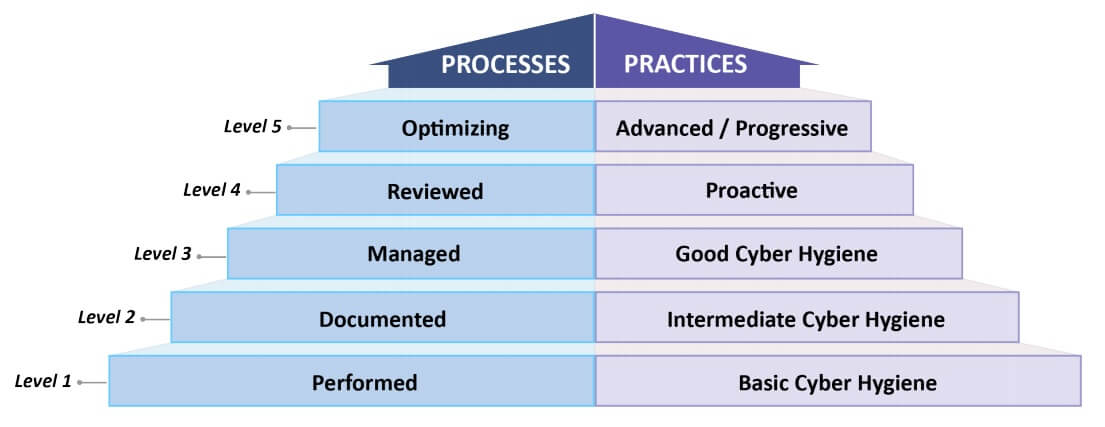
CMMC Levels and Descriptions, from CMMC Model v1.0 document
Four pages of the main CMMC document and eight pages of the appendix are devoted to maturity level explanations. These maturity levels are a third dimension on top of the controls.
For example, 17 practices are introduced at Level 1 of the CMMC. These same 17 practices apply to all higher levels 2-5 as well. But there is a difference in the process maturity level required at each level.
Let’s take one CMMC practice. PE.1.132 “Escort visitors and monitor visitor activity.” How would this practice change at various maturity levels?
At L1, maturity level “Performed”, I would expect to see visitors escorted in an ad-hoc fashion. I wouldn’t expect documentation, policies, training, or improvement around the process.
At L2, maturity level “Documented”, I would expect to see visitors escorted, a policy that discusses how visitors should be handled, and training for most employees. I wouldn’t expect oversight or 100% policy compliance at this level. There may be some visitors who aren’t being signed in or escorted due to lack of training or lack of staffing.
At L3, maturity level “Managed”, I want to see planning, oversight, and a strong attempt to reach 100% policy compliance. The security officer should be comparing reality versus the documentation and looking for problems. The staff should be on-board with the policy and processes, and helping to make it happen. For example, all staff, if questioned, should know how to respond if they see an un-escorted visitor. The security officer will probably be assigning visitor badges to distinguish between “legitimate” visitors and visitors who are bypassing security.
Level 4 and 5 are defending against Advanced Persistent Threats (APTs)
At L4 and above, the CMMC is concerned about adversaries (APTs) specifically targeting the organization. This adds risks such as badge stealing or duplication, or insider threat from legitimate visitors.
At L4, maturity level “Reviewed”, I want to see records that show the visitor policy / process has been reviewed for effectiveness in the last year. The security manager should be testing the processes and finding issues such as lack of training, an exterior door was unlocked which allowed maintenance staff to enter without signing in, or a visitor was allowed to leave with their visitor badge. The security manager should be able to show how they fixed or are working to fix the issues.
At L5, maturity level “Optimizing”, I want to see best-in-class procedures and tools used to achieve the practice, with the assumption that the organization is under high threat from sophisticated adversaries. Monitoring at this level might involve security cameras for all sensitive spaces (especially manufacturing floors) with security guards watching those cameras 24×7. Visitors might need to be pre-approved and go through background checks before arrival. There might be entrance and exit searches.
Several important CMMC topics are split out from the main document
What I considered the main body of the CMMC – the tables of controls – has been split into an appendix document.
The appendices can be found here: https://www.acq.osd.mil/cmmc/docs/CMMC_Model_Appendices_20200203.pdf
Process Maturity discussion
Appendix B.2 has an 8 page discussion about maturity and what it means at CMMC level 1, 2, 3, 4, and 5.
For level 3, it discusses organizations having a plan to achieve each domain’s activities.
“The organization establishes and maintains a plan for achieving the [DOMAIN NAME] activities. The plan should include strategic level objectives that can be used to inform senior leadership of the status of the organization as it relates to [DOMAIN NAME]. The plan can be a stand-alone document, embedded in a more comprehensive document, or distributed among multiple documents. The plan should be maintained and followed.”
“The organization defines the needed resources and the plan is resourced accordingly.”
This sounds very similar to the status quo for DFARS 7012 / NIST SP 800-171 – organizations don’t need to be 100% compliant with all controls, but they do need to show that they are working on them with a System Security Plan and Plan of Action & Milestones.
Obviously this won’t be for sure until the CMMC Accreditation Body releases their guidance, but to me it sounds like a gentling of the requirements for CMMC. A good change, since it is almost impossible for real companies (ones with legacy systems) to fully achieve every technical control.
The part about resourcing the plan accordingly is significant. Per Appendix B.2, the strategic plan should have a budget, establish funding needs, resolve funding gaps, assign competent staff, and identify tools necessary to achieve the requirement.
Individual CMMC practice / control guidance
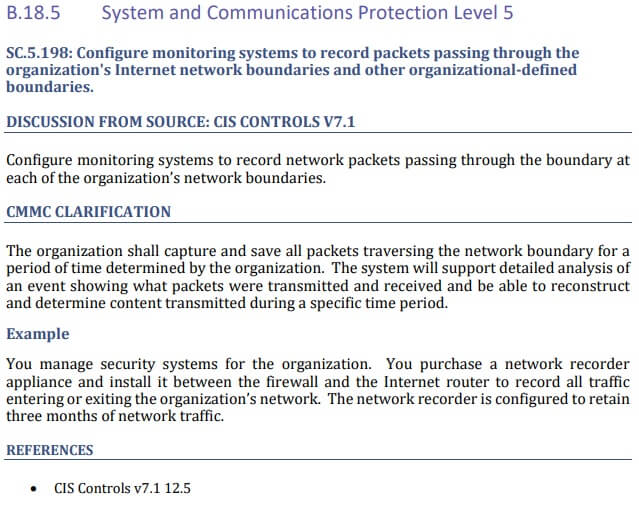
Screenshot of Appendix B.18.5 from the CMMC v1.0 appendix document.
The screenshot above shows the CMMC’s expanded guidance for practice SC.5.198. This is a Level 5 practice. The guidance includes text from other compliance frameworks, specifically what technical implementations the CMMC is looking for, a simple to understand example, and reference to other compliance frameworks where this control appears.
Starting at Appendix B.3, the appendices document provides expanded guidance for individual CMMC practices. Each practice is given 1-2 pages of additional clarification. This includes technical details and at least one example for each practice.
The CMMC version 1.0 document has expanded guidance for every practice, up to level 5. This is brand new material and a must read!
Next steps – now that CMMC v1.0 is released
The CMMC Accreditation Body still needs to
- Finish organizing and establish a Memorandum of Understanding with the DoD.
- Hire staff to execute the mission.
- Identify scope requirements.
- Identify what a successful audit looks like.
- Release training for auditors.
- Accredit auditors.
The auditors need to…
- Train and get their staff accredited
- Possibly obtain security clearances
- Audit organizations and deliver their findings
The organizations need to..
- Improve their cyber-security practices and processes based on guidance from the CMMC version 1 document
- Get audited by an accredited auditor (and hopefully pass)
- Respond to new RFPs with their CMMC level
I hope this helps! Did you see anything I missed? Please comment with your thoughts below!
Amira Armond is the owner of Kieri Solutions, a cyber-security firm in Maryland.
Next article: How to become a CMMC auditor or certifier