This article is provided by our sponsor, Kieri Solutions, an authorized CMMC Third Party Assessment Organization (C3PAO). Kieri Solutions provides assessment services, high-quality CMMC consulting, and an easy to use compliance documentation package geared toward small and medium businesses.
CMMC assessments are expensive! Don’t volunteer for assessment if you won’t pass. This article describes 11 topics which affect your readiness for CMMC assessment, and strategies and tips to overcome each problem.
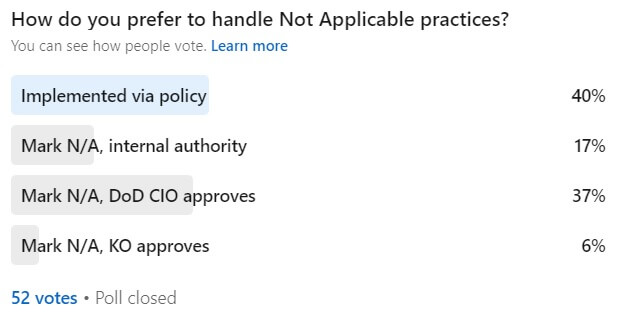
1. Not Applicable practices:
Does your System Security Plan identify the practices that you consider Not Applicable, and has a designated authority approved those non-applicables? (Reference: CMMC practice CA.L2-3.12.4 [d] )
Who is the designated authority? If you have a contract with DFARS 252.204-7012 in it, that authority might be the DoD Chief Information Officer (CIO).
“B) The Contractor shall submit requests to vary from NIST SP 800-171 in writing to the Contracting Officer, for consideration by the DoD CIO. The Contractor need not implement any security requirement adjudicated by an authorized representative of the DoD CIO to be nonapplicable or to have an alternative, but equally effective, security measure that may be implemented in its place.
(C) If the DoD CIO has previously adjudicated the contractor’s requests indicating that a requirement is not applicable or that an alternative security measure is equally effective, a copy of that approval shall be provided to the Contracting Officer when requesting its recognition under this contract.”
DoD CIO’s email to submit requests to vary (or not applicable) is… osd.dibcsia@mail.mil
2. Does your System Security Plan describe how you are IMPLEMENTING each security requirement?
Reference: CA.L2-3.12.4 “[e] the method of security requirement implementation is described and documented in the system security plan;”
Many companies do this wrong! They have been given BAD ADVICE to hide the details of their implementation. Or they use a prep company that auto-generates their SSP using vague statements because it is cheap to auto-generate SSPs. This is a bad idea!
What does describing implementation look like?
“We implement screen lock on our Windows 2016 servers using the Group Policy “Server2016_LocalSecurityConfigs”. The specific setting is “Lock screen timeout = 15 minutes” We have verified through testing that screens will revert to a locked status and hide previously visible information with this timing.
We implement screen lock on our CentOS servers by…”
What does NOT describing implementation look like?
“Access to the system and viewing of data is prevented by initiating a session lock.”
“Screen locks are implemented.”
My rule of thumb during my company’s CMMC assessment (to become an Authorized C3PAO) was that I wanted the SSP to have all the answers. I expected myself and my staff to be sleep deprived, stressed out, and intimidated. I did not want to rely on being brilliant during the interview. By putting full details of implementation in the SSP, I knew that no matter how tired we were, we could reference the SSP to find the answer.
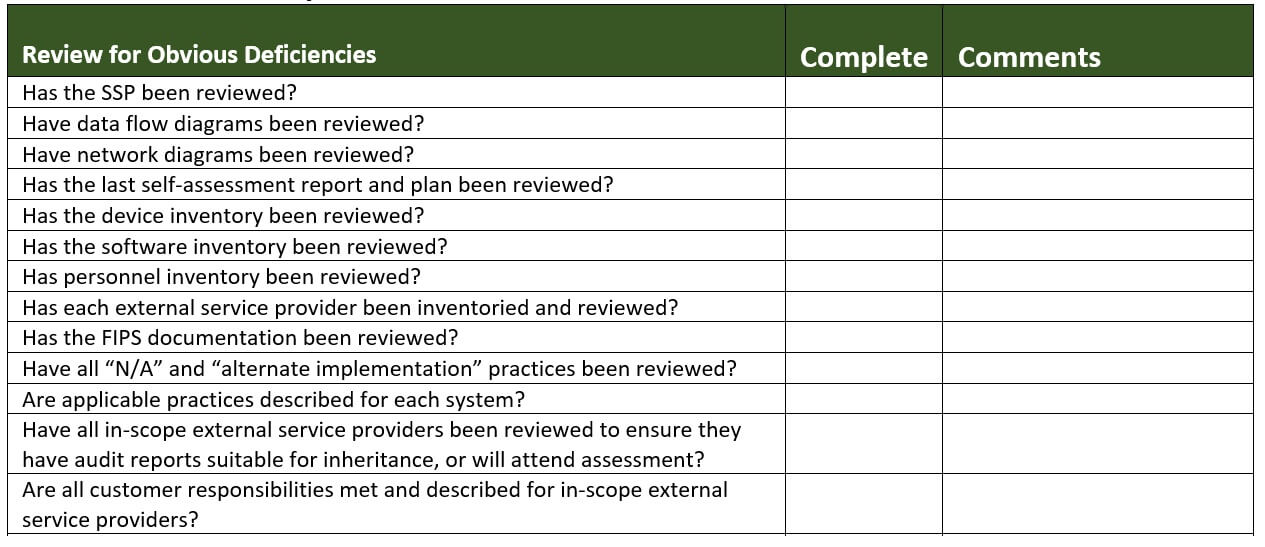
3. Do you know where your evidence is?
You should. In fact, you should have formally reviewed every piece of your evidence at least once BEFORE asking for assessment.
CA.L2-3.12.1 “[b] security controls are assessed with the defined frequency to determine if the controls are effective in their application.”
Another term for this requirement is “Doing a self-assessment”. Your expectations for evidence during your self-assessment should be as stringent as a third-party assessment! Self-assessments are safe spaces to fail. Don’t go easy on yourself during a self-assessment.
To do a high quality self-assessment, you need to know what you are examining, who you are interviewing, and what you are testing. Your evidence plan (all of these are sources of evidence) should be based primarily on what is written in the System Security Plan (SSP) for each practice.
If your SSP is written well, the implementation of each practice will be described thoroughly. At that point, assuming that you interpreted the assessment objectives correctly and described a good solution, your job as a self-assessor is simply to verify that each statement in the SSP is true.
Video: System Security Plan How-to for CMMC and 800-171
Ideally, your SSP identifies what/who can be examined, interviewed, and tested for each practice. If it does not, you should document what you examined, who you interviewed, and what you tested during the self-assessment. Yes. It takes work. This is how to do a quality self-assessment. The good news is that you can re-use this effort when monitoring controls on an ongoing basis (CA.L2-3.12.3) as well as your next self assessment.
What if you didn’t interpret some assessment objectives correctly? That is a problem with self-assessments. You won’t find out that your practice is NOT MET until you get a third-party assessment.
PRO TIP: “testing” is often as simple as checking live systems to ensure that security is active on them. To test yesterday’s example, we would have just checked to see that the Group Policy was applied to each in-scope server.
4. Data flow control is essential
Have you identified exactly how CUI enters, moves through, and leaves your in-scope environment?
This is essential for justifying your proposed scope to your C3PAO. It is also essential to identify which assets you need to secure.
An ideal environment has cut down the potential ways that CUI can flow to a minimum. I love to see the following:
– A standard way to send CUI to-and-from partners or clients.
– All the users, and partners and clients, are told/trained to use that method with a unified voice.
– Other common unapproved methods are blocked using technical means (such as blacklisting popular unapproved clouds (think personal subsciptions to OneDrive, DropBox, Google drive).
Are you thinking that this is too high an expectation because all of your users and projects pick their own method to move CUI? This is a red flag. If you arent controlling how CUI moves in a proactive way, you are not ready for assessment.
AC.L2-3.1.3 “[c] designated sources and destinations (e.g. networks, individuals, and devices) for CUI within the system and and between interconnected systems are identified;”
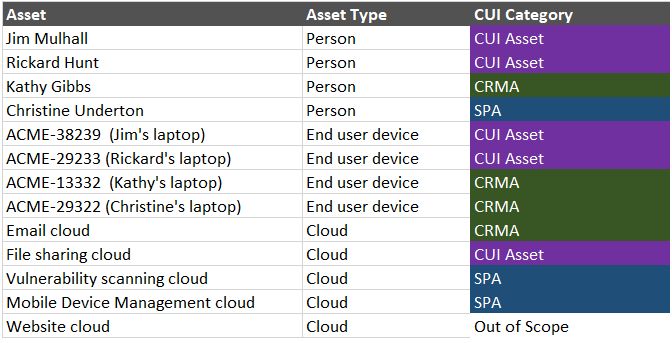
5. CMMC Asset Categories
Do you have a list of all your assets (at minimum by groups of like assets) which identifies each with their CMMC Asset Category?
“The contractor is required to document all asset categories that are part of the assessment scope in an asset inventory and provide a network diagram of the assessment scope to facilitate scoping discussions during pre-assessment activities.” – CMMC Assessment Scope, Level 2.
A common mistake is not having a detailed inventory ready. While I don’t think it is required to provide a list of 2000+ assets with each category carefully identified, you should be able to identify the categories based on rules, such as “all users in the CUI_user security group are considered CUI Assets”, then use those rules to identify individual assets in an inventory as needed.
I can hear the screams from here. “But why???” “That is a ton of work!” Actually, you were supposed to have everything identified individually as part of the CMMC Level 2 requirements for Access Control and Configuration Management. And I think most assessors will agree that if a system or account is connected to your in-scope network, you should have records to identify it. Just because an asset is a CRMA doesn’t mean you are allowed to skip Access Control.
CM.L2-3.4.1 “[d] a system inventory is established;”
AC.L1-3.1.1 “[a] authorized users are identified”
AC.L1-3.1.1 “[c] authorized devices are identified”
AC.L2-3.1.8 “[a] mobile devices that process, store, or transmit CUI are identified;”
Pro tip: If you have a complex asset which has sub-components that do different things… such as a productivity cloud that has file sharing (CUI asset), web hosting (out of scope), and an admin console (Security protection Asset), you can identify each sub-component with its detailed category. Having less CUI Assets is always a good thing during assessment.
6. Do you have a Plan of Action (and Milestones)?
I love how it is alternately described as a Plan of Action (POA) and a Plan of Action And Milestones (POA&M or POAM) depending on who you talk to and which DoD branch they worked in. They are both the same thing.
As described in NIST SP 800-171 and the CMMC Assessment Guide: “Organizations develop plans of action that describe how any unimplemented security requirements will be met and how any planned mitigations will be implemented”
CA.L2-3.12.2 expects every organization to have a POA and to implement it over time.
“[a] deficiencies and vulnerabilities to be addressed by the plan of action are identified;”
“[c] the plan of action is implemented to correct identified deficiencies and reduce or eliminate identified vulnerabilities.”
But to get back to the point.. you may be saying, “but I’m not allowed to have a POAM”. And that is kind-of true. That is because the CMMC Program Management Office has been using “POAM” as the term to describe a company which is not performing all CMMC requirements. That isn’t the original intent of the control. Did you see the word “reduce” in [c]?
The original intent was to track your progress over time until you reach full compliance, AND to track permanent or temporary deficiencies which should NOT cause you to fail a practice.
The DFARS Cyber FAQ is linked below this post. It is an authoritative source of guidance.
The FAQ gives more information about temporary and enduring exceptions to accommodate special circumstances. Reference A56 and A59 in particular. “The contractor should address issues, security requirement implementations in progress, special circumstances/enduring exceptions, and any individual, isolated or temporary deficiencies through “plans of action”…”
It is possible to pass CMMC with an open POA if you show that risks are actively managed, the problem and solution have been thoroughly reviewed for alternate measures, and you have a plan to resolve as soon as it is possible to do so. Not ideal! But every company that actually uses their information system will encounter situations where they cannot apply the requirements to every single system at all times. I’d rather see a company acknowledge and manage issues than try to ignore them.*
*This does not mean you will pass assessment if you have unimplemented requirements. However, good assessors should consider the nuanced advice in the DFARS Cyber FAQ before making a hard call.
7. Don’t be smarter than your assessor.
How can you tell that you are being smarter than your assessor?
1) You think it is acceptable to “tailor” the requirements that apply to your system, a la 800-53.
2) You have NOT asked DoD CIO to approve your “not applicable” practices or “alternative, but equally effective practices”, OR they have replied that the your plan is not approved.
3) You have already bragged about suing your assessor if they don’t agree with your decisions.
Assessors need to be consistent during their assessments. If they have assessed (and passed and failed) fifteen companies using standard criteria, they are not going to change those criteria just for you.
Topics where assessor expectations are often higher than OSC’s:
a) Separation of duties
b) Review and approval/disapproval of changes
c) What “monitor” means
d) What “authorize” means
e) Proof required for external service providers / clouds
f) Scoping for endpoints that access CUI on virtual desktops
g) Scoping for endpoints that process and store CUI files from a popular end-to-end encryption product
h) FIPS “compliant” encryption
This standardization can be good for OSCs. Many security professionals are too hard on themselves. They don’t know where the “bar” is. It is actually pretty common for an OSC to be down on themselves about a solution that the assessor just saw (and passed) in the last fifteen assessments.
Common examples of OSCs setting expectations too high:
a) FIPS 140-2 validated cryptography for protection of authentication mechanisms like MFA, fingerprint scanners.
b) Feeling forced to use hardware firewalls, not acknowledging software firewalls as an option.
c) Patching on an extreme schedule (such as less than a month)
d) Putting CUI stickers on computing devices
Why is it good to have a smart assessor?
The smarter your assessor, the more likely they are to understand out-of-the-box solutions and accept them (if they really do meet the assessment objectives).
Why is it bad to have a smart assessor?
It is much harder to show them a bad solution and have it accepted. Some smart assessors use their powers for evil (setting the bar too high).
Which is better? Neither. You want to have a consistent assessor.
Pro tip: I’ve talked to a dozen OSCs that were given a perfect 800-171 assessment by unqualified firms. Most commonly, the assessment took less than two days and was sponsored by a MEP or PTAC office. 800-171″A” assessment objectives were not reviewed, and the scope was faulty. These companies are going to have a harsh wake-up call. I actually consider it a red flag when an OSC reports they were given a perfect 110 score in a drive-by assessment.
(Shameless plug for Kieri Solutions, the author of this article)

8. Do you have your organizational ducks in a row?
Do you know the CAGE code(s) that will use this information system? These are unique place-of-performance (location) IDs that contractors registered on sam.gov use when billing for a contract. Any company can register on sam.gov to get one. The Department of Defense uses these CAGE codes to look up which contractors have been CMMC certified.
Do you have an Assessment Official – someone who has authority in your organization to commit to an assessment contract and is high enough in the chain that they can require participation from all in-scope departments?
Do you know which contract(s) CUI you will protect with the in-scope information system? All CUI in your company does not need to be assessed at once. There are good reasons to assess by contract, such as 1) setting up a known good system before migrating the entire company to it, 2) different requirements in different contracts, such as CMMC Level 3 vs 2, or export controlled vs international. While CMMC contract scope is still undefined by DoD, all prior cybersecurity requirements have applied at the contract level.
Do you have key compliance roles identified? Organizations tend to struggle identifying Security Officers / CISOs / Compliance Managers by title. At the least, you need someone who knows the SSP (overall security program) very well and who can be a primary technical point of contact.
Do you know which people PERFORM practices hands-on? Don’t make the mistake of bringing an executive to the interview who has never even seen the process performed. Assessors want to interview the person in the trenches, not the person two levels above them.
9. No security for Contractor Risk Managed Assets?
Do you think the scoping guide for Contractor Risk Managed Asset (CRMA) says “no security required”? (cue the disco music and freestyle dancing)
Hate to break it to you, but the DoD expects some security on those assets. Applicable security should be determined at least partially through your risk assessment process.
“Contractor Risk Managed Assets are part of the CMMC Assessment Scope. These assets are managed using the contractor’s risk-based information security policy, procedures, and practices and are not assessed against CMMC practices.”
The OSC is required to: “document these assets in the SSP to show they are managed using the contractor’s risk-based security policies, procedures, and practices;”
– CMMC Scoping Guide for Level 2
How do assessors interpret this guidance?
Most would like to see a thoughtful risk assessment performed against the CRMA assets. How could they be compromised? How could they be used to attack CUI or your operations?
Any good risk assessment should include a description of how risk is being mitigated currently as well as a plan for additional risk reduction (or acceptance).
If risk assessment is done correctly, the OSC should be able to define what is appropriate security for CRMA.
There is precedent that the DoD expects to see some security applied to CRMA assets used to access CUI via a Virtual Desktop session. This is due to the threat that unmanaged CRMA could be compromised to collect logon information or record the screen for an attacker.
Potential security could include malware protection, additional logging, software control, user privilege control, hard drive encryption, and/or patching. To my knowledge, the DoD has not published anything in writing about their expectation for CRMAs that access CUI via a Virtual Desktop session. However, they have talked about it repeatedly in regard to DIBCAC-C3PAO CMMC assessments.
If an OSC fails to perform risk assessment for their CRMA and doesn’t perform any security for them, would C3PAOs be willing to assess that OSC? This is still to be determined. The DoD seems to expect C3PAOs to follow DIBCAC’S precedent. I recommend doing a quality risk assessment and mitigation process for your CRMA so that you are covered no matter which direction the DoD goes.
10. Are you trusting the wrong sources of advice?
There are unfortunately many bad actors “helping” the Defense Industrial Base. They prey upon desperation, ignorance, and a lack of accountability.
Red flags include:
Security/incident response vendor: Very few or no incidents created. Expect at least 1 real incident per 5 users per year. Expect a lot more benign or false positives. There are too many security firms that do nothing and collect a nice monthly payment.
Web-based apps that allow viewing of CUI: Other than virtual desktop/terminal services, I have not yet seen a solution that keeps user endpoints from storing/processing CUI. If the web server decrypts CUI in order to render it in a browser, the web server (and probably the endpoint) is in scope. If the endpoint saves a copy of the doc locally (even in temp files) it is in scope. Don’t fool yourself that the solution can magically let you work with CUI without contamination.
Do it yourself compliance: If a vendor says you can do it yourself without significant IT and Cyber SME help (a few hundred hours at least), you are in trouble. A hallmark of a bad egg is saying CMMC/800-171 compliance is easy. Another sign is an offering that leans on the MEP Cybersecurity Handbook 162 rather than the Assessment guides for CMMC or 800-171(A).
Drive by gap analysis: If an assessment company spends less than two days with you, then you are either 1) completely failing and there is not much to review. 2) sooo amazing that you provided all evidence and screenshots in advance (very unlikely unless you are a dedicated cybersecurity firm). 3) working with a bad vendor. When in doubt, you can tell the difference between 1 and 3 with your score.
11. You might be more ready than you think.
Are you struggling to secure some of your systems to the required levels? Many organizations have this difficulty, especially with 1) Line of Business systems, and 2) Development systems.
You should carefully consider the description of Restricted Information System, a subcategory of Specialized Assets. This is a common asset category in the Defense Industrial Base.
“Restricted Information Systems can include systems [and associated Information Technology (IT) components comprising the system] that are configured based on government requirements (i.e., connected to something that was required to support a functional requirement) and are used to support a contract (e.g., fielded systems, obsolete systems, and product deliverable replicas).” -CMMC Scoping Guide for Level 2
Some questions to ask are..
1) If you removed the system, could you perform your contract?
2) If you applied all the CMMC requirements, would the system still function as needed to perform the contract?
3) Is there a reasonable alternative in the market that can implement all the CMMC requirements and still support the contract?
If all the answers are “No”, you may be able to argue the case for it being a Specialized Asset of type Restricted Information System.
For Specialized Assets, apply the security you can using your best risk-based approaches.
I always recommend getting a second opinion about your proposed scope. You can also interview potential C3PAOs to see if they interpret scoping (and other hot button topics like FIPS) in a standard way.
If this article is useful to you, please share it with others, join our newsletter and connect on LinkedIn!
Amira Armond is a CMMC Provisional Instructor, Provisional Assessor, CISSP, and CISA. She is the owner and Quality Manager for Kieri Solutions, an authorized C3PAO offering assessments, CMMC preparation services, and the Kieri Compliance Documentation package . Amira Armond is the chief editor for CMMCaudit.org and volunteers with the C3PAO Stakeholder Forum, an industry group striving for consistency of interpretation and successful rollout of the CMMC program.